Privilege Escalation in AWS with PassRole Attacks
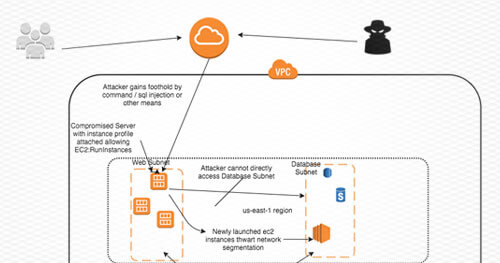
All instances launched by AWS by default have instance credentials supplied by the AWS metadata service. AWS operators can attach PassRole policies given to an instance at launch time.
Breaking Through Single Sign On (SSO)
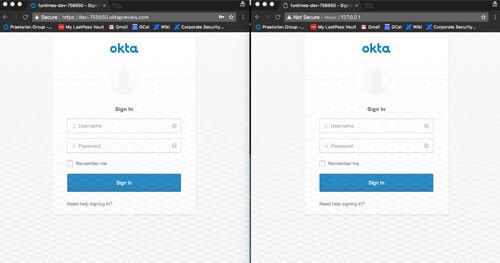
During my internship with Praetorian, I was able to create a new tool—Okta Watering Hole—that was used on some of the red team engagements. I created this tool because our team ran into the issue of not being able to get past two factor authentication on various web portals—so this is how we got around that. Okta Watering Hole sets up a carbon copy of a target Okta site and begins to capture credentials and sessions of visitors. This can be used to check how a company’s procedures and policies stand up to the “next generation” phishing attacks we are beginning to see. This new tool supports traditional phishing attacks as well as targeting two factor authentication devices—meaning perimeter security has to work double time.
Path.Combine Security Issues in ASP.NET Applications
Path traversal vulnerabilities are a common class of web application vulnerability, where an attacker aims to access files outside of the intended directory by using “../” patterns to traverse directories or by using absolute paths. These vulnerabilities are commonly found in file upload or download functionality of an application.
How to Mitigate Mimikatz WDigest Cleartext Credential Theft
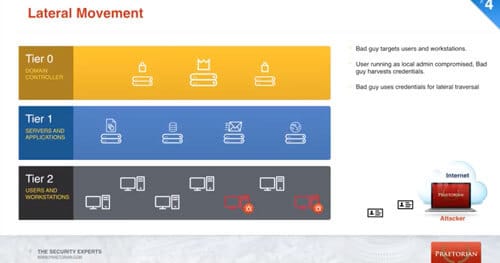
Penetration testers and malicious adversaries often focus on using the easiest attack vector to achieve their objectives. One common attack vector that has been around for several years is to use a tool called Mimikatz and steal cleartext credentials from memory of compromised Windows systems.
Reversing and Exploiting Embedded Devices: The Software Stack (Part 1)
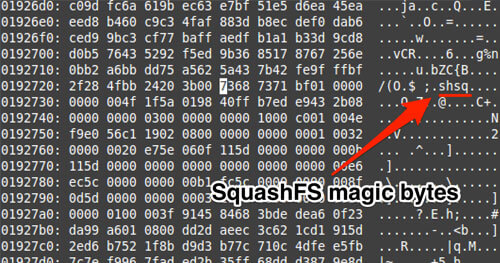
Over the course of the past few months I’ve been traveling around educating people on exploiting embedded devices. My slides alone aren’t able to provide enough information, so I wanted to write everything out for people to digest online. The following blog post is “Part 1”, which will introduce the reader to the software side of embedded devices. I decided to cover software first since most flaws reside within the software stack, ranging from binary applications to drivers. Part 2 will cover the Hardware stack with a focus on educating the reader on how JTAG actually works and how to leverage Hardware modifications to either bypass password protections or to extract secrets that may be baked into the targeted devices.
Broadcast Name Resolution Poisoning / WPAD Attack Vector
One of the common attack vectors for penetration testing is to leverage an attack known as Broadcast Name Resolution Poisoning. Recently, US-CERT posted an advisory about this attack being used externally. Attackers purchased new generic Top-Level Domains (gTLDS) and setup entries for the Web Proxy Auto-Discovery Protocol (WPAD). This is pretty interesting since it’s an old attack used in a new way. Let’s dive into how Broadcast Name Resolution Poisoning is used during internal penetration testing and go over recommendations for how to fully mitigate all forms of attack.
JTAGulator vs. JTAGenum, Tools for Identifying JTAG Pins in IoT Devices
Do you suspect some pins on your device are JTAG? There are several methods out there for identifying if pins are likely to be JTAG or not. One of those methods involves buying a $200 JTAGulator, however there is a cheaper Arduino-based alternative I will be detailing in this post. First I’ll explore the expensive way.
Why are JTAG and UART still effective attack vectors for IoT devices?
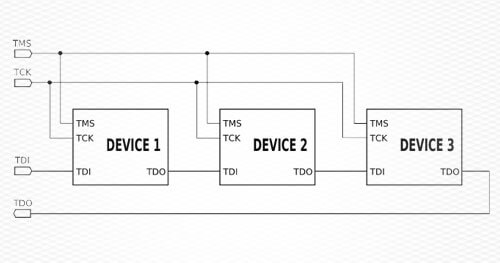
Whether it’s a vulnerable router, an Internet of Things (IoT) connected device, or some other piece of hardware, JTAG and UART debugging test pins left on the device are going to continue to be one of the most effective physical hardware attack vectors available to a malicious actor. Never assume your secrets on IoT devices, such as encryption keys, are safe. You may be wondering what JTAG and UART are, and why they’re left on boards.
Internetwache RE60 Writeup: Symbolic Execution Tramples CTF Challenge
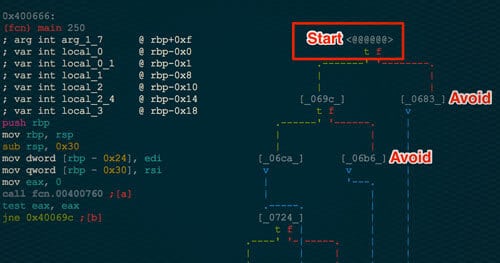
I am always looking for problems that symbolic execution could be applied to in the capture the flag space. This past weekend, this challenge was met during the Internetwache CTF for its RE60 problem. Below I describe the application of symbolic execution to solve the challenge without much knowledge of the inner workings of the binary itself. Symbolic Execution gives the reverse engineer the ability to find a specific path from Point A to Point B in a binary. This path is represented by a series of boolean expressions. These expressions can then be passed to a solver such as Z3 from Microsoft to solve the equation, creating an input that will exercise the found path.
Pentestly Framework: When Pentesting Meets Python and Powershell
Python appears to be an ever growing trend in the security community. Being able to connect Python tools together has proven beneficial for us. Powershell has also seen increasingly more use due to its wide availability in internal environments. Pentestly utilizes the power of these tools together in a familiar user experience.