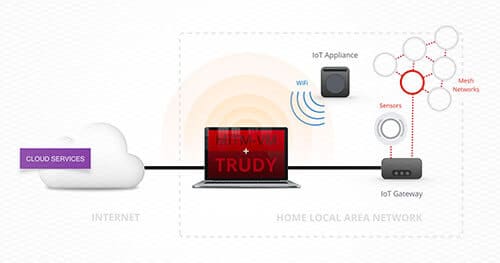
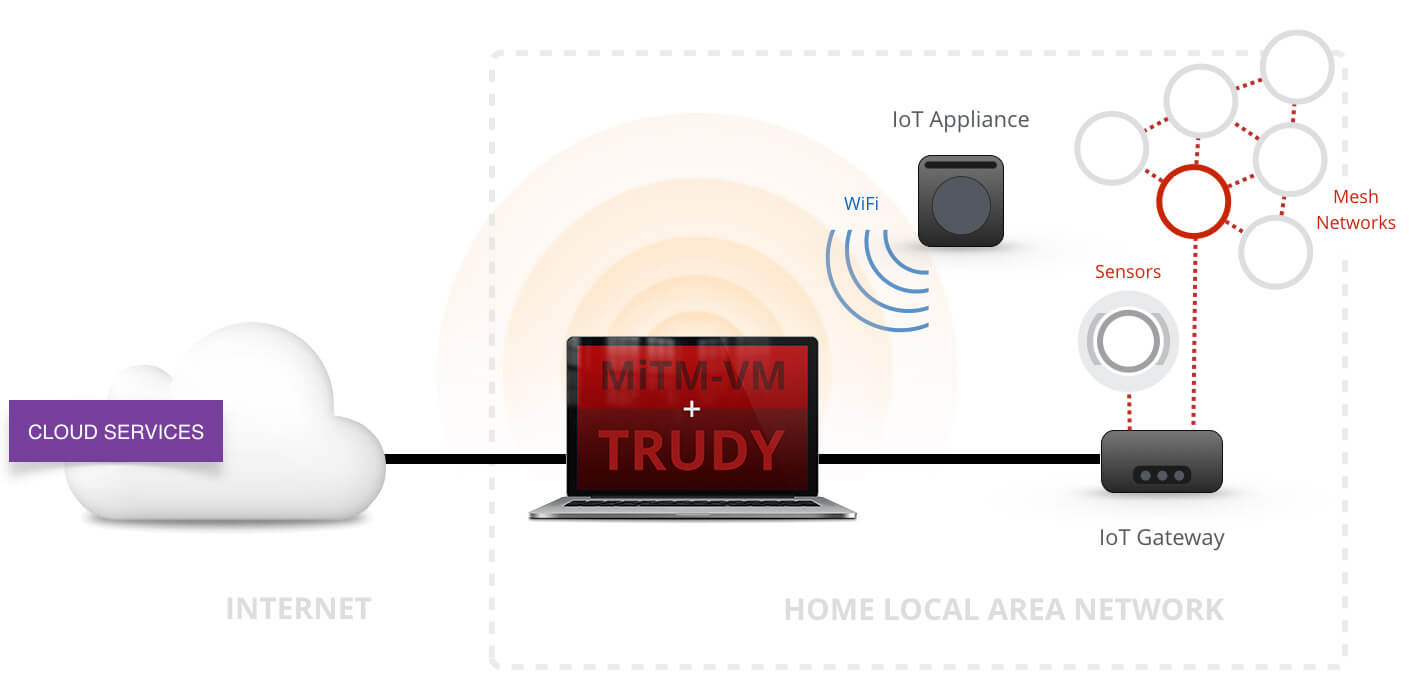
Positioning yourself as a man-in-the-middle (MitM) is a powerful situation to leverage during a security assessment.
Unfortunately, in some situations, leveraging an active MitM position is difficult. There are existing proxies that try to alleviate these issues but they all seem to suffer from a flaw that makes using the tool undesirable. MitM-VM and Trudy are a complimentary set of tools that are designed to address several issues with existing proxies. Together they enable easy-to-setup and powerful man-in-the-middle positions.
Why build these tools? Modifying custom binary protocols on the fly while sitting between an embedded device and a server is usually a slow process that involves sniffing legitimate traffic and then rebuilding packets programmatically. Trudy makes this process easy by enabling Burp-like features for generalized TCP traffic.
MitM-VM is a Vagrant virtual machine that can be used as a transparent proxy. For those who have not used Vagrant, deploying the virtual machine is very straightforward and the virtual machine will be configured to handle most proxying situations. A simplistic motivating example: before MitM-VM, I often used an OpenWRTrouter with tcpdump (or similar) to monitor the traffic of my target device. This works well in most cases, but suffers from two major issues: first, routers are equipped with inferior hardware when compared to my laptop; second, I now have two pieces of hardware to manage. MitM-VM can be configured to provide the same functionality as my multi-hardware setup. Aside from the added benefit of less physical hardware and better specifications, I now also have a fully-featured Debian box to handle my traffic. (I still love OpenWRT though!)
MitM-VM also installs and configures several utilities that can be used to monitor or modify traffic. MitM-VM’s documentation lists these tools.
Trudy is written in Golang and intended to be used within MitM-VM. Trudy is a transparent proxy that works for any TCP connection and allows for programmatic and manual modification of TCP packets. Trudy aims to be simple to configure, easy to install, and generic enough to provide value in unique situations.
It does this by creating a 2-way “pipe” for each connection it proxies. The device you are proxying (the “client”) connects to Trudy (but doesn’t know this) and Trudy connects to the client’s intended destination (the “server”). Traffic is then passed between these pipes. Users can create Go functions to mangle data between pipes.
To proxy TLS connections, the Trudy binary spins up a TLS server with an invalid certificate. Obviously, you will need a valid certificate or a client that does not validate certificates.
Trudy was designed for monitoring and modifying proxy-unaware devices that use non-HTTP protocols. If you want to intercept and modify HTTP(S) traffic, Burp Suite is probably the better option.
Case Study
Praetorian was engaged to perform an assessment of an Internet-connected home device. This device leveraged a custom binary protocol on top of TCP that had several security issues. Notably, the protocol header information contained the packet’s length information and the packet’s headers were not authenticated. This length value was trusted by the device and used during a packet processing routine. An active man-in-the-middle could leverage this flaw and overflow a buffer. We needed to modify non-HTTP traffic, so Burp would not work. We also needed to modify a byte whose location and value was dependent on other information within the packet, so netsed would not work. Lastly, we wanted minimal configuration and install time, so Mallory or Squid would not work. Trudy coupled with MitM-VM alleviated all of these issues.
Getting Started
If either MitM-VM or Trudy seem interesting to you, please check out the READMEs on their respective Github repos. I have documented enough information to make getting started with either project a straightforward process. If anything seems unclear, difficult to set up, or broken please feel free to open a Github issue or contact us directly at: info@praetorian.com.