Free Attack Surface Management
An Enablement Technology for Effective Continuous Threat Exposure Management
We believe that attack surface management should be a foundational capability available to all organizations without cost. Attack surface management is a crucial enablement technology that provides visibility into potential attack vectors, allowing organizations to understand their exposure and take proactive measures.
- Address exploitable risk, not superficial detections
- Reduce complexity through an all-in-one offensive platform
- Bring the attacker's perspective to every challenge
- Integrate technologies and expertise into a cohesive, efficient, and effective Continuous Threat Exposure Management strategy
- Quantify risks and focus on material threats rather than attempting to address every potential issue
Start Free with Attack Surface Management
Please complete the form below to get started.
Trusted by the World’s Most Iconic Brands

Stay Ahead of Potential Attacks
Address Exploitable Risk, Not Superficial Detections
Praetorian aims to democratize access to essential security tools, enabling organizations to focus on identifying and mitigating material risks.
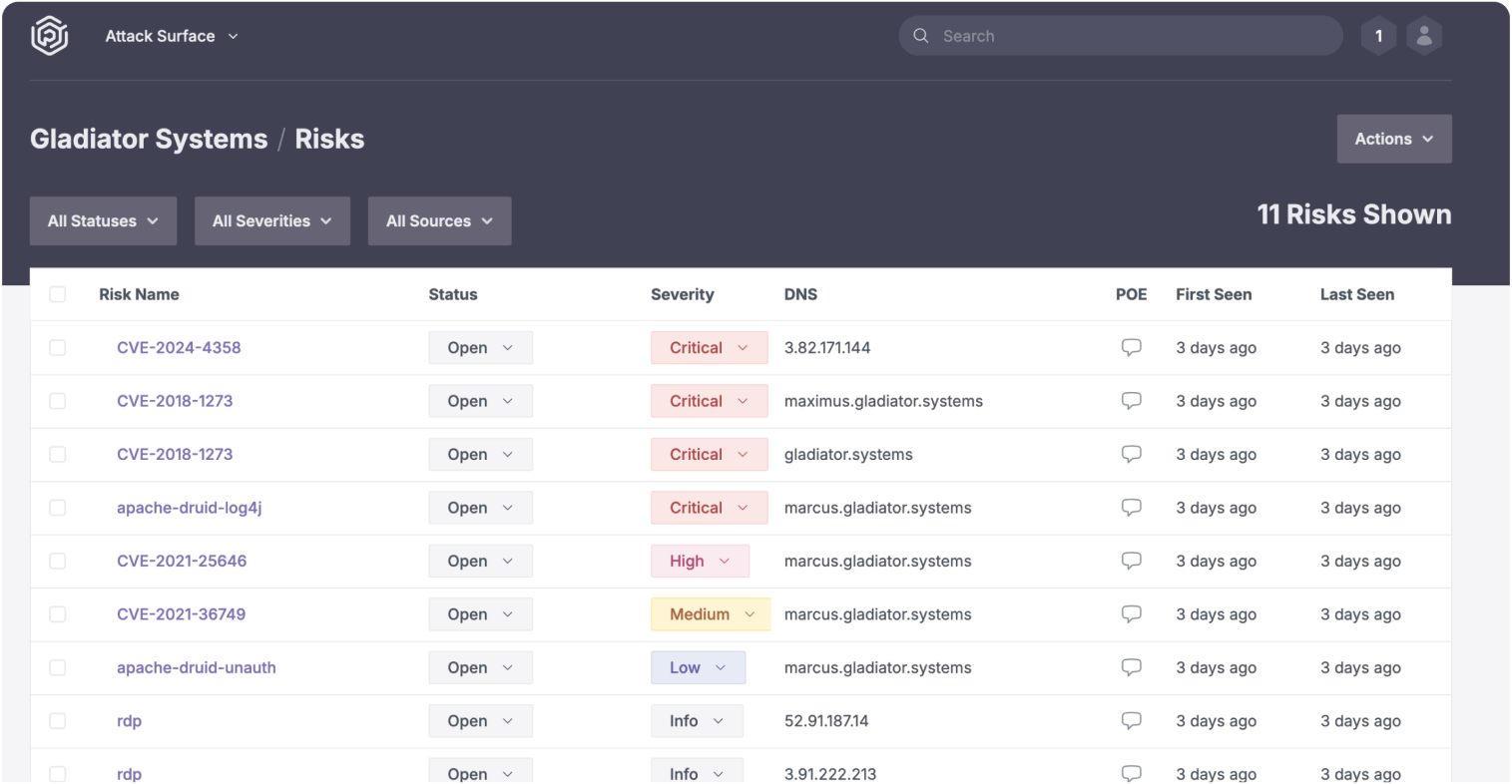
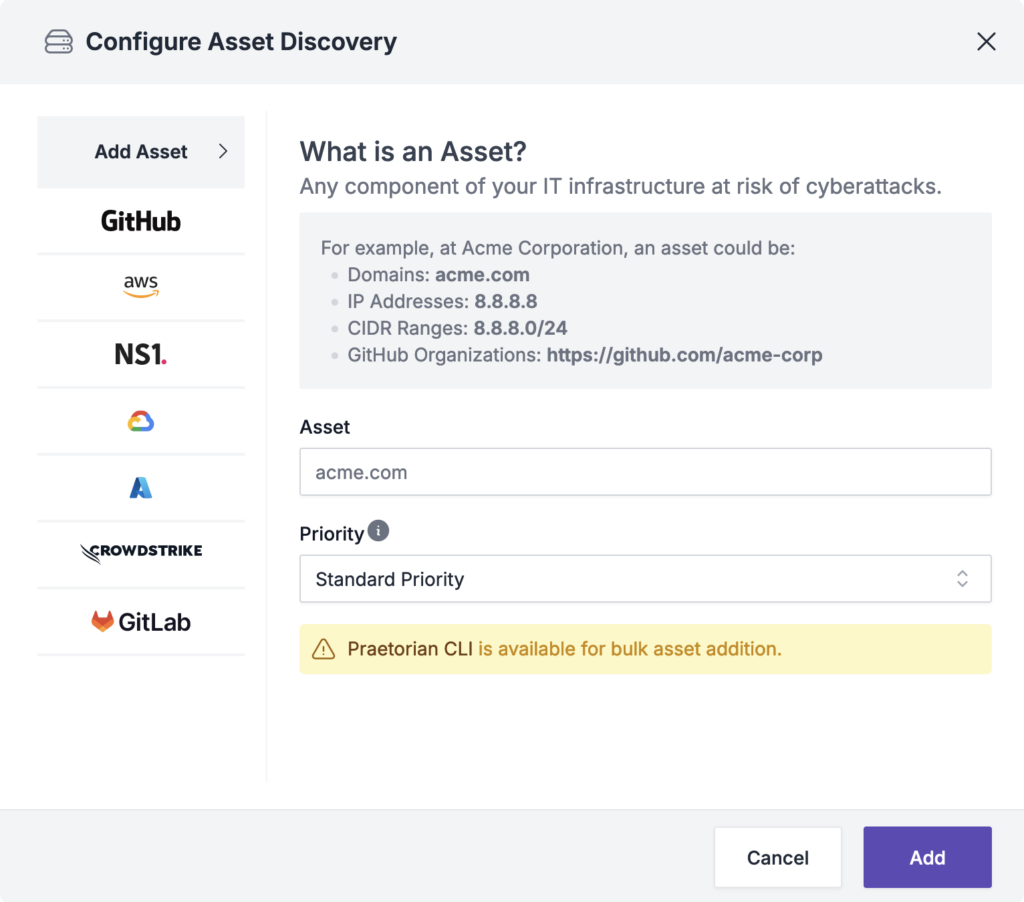
Chariot’s Attack Surface Management Module
Our Chariot platform includes a comprehensive attack surface module designed to provide deep insights into an organization’s assets and attack surface. Asset identification and attack surface mapping include both outside-in attack enumeration and inside-out system of record integrations. Current integrations supported under freemium include:
- AWS
- Azure
- GCP
- GitHub
- GitLab
- NS1
- Cloudflare
Attack Surface Management Features at No Cost to You
Exposed Secrets in Code
Automatically identifying secrets that have been inadvertently exposed in public or private repositories.
Repository Status Changes
Monitoring changes from private to public repository status to ensure sensitive information is not unintentionally exposed.
New Public Repositories
Detecting the addition of new public repositories to manage and mitigate potential risks.
Vulnerabilities in GitHub Self-Hosted Runners
Identifying and addressing vulnerabilities in self-hosted runners used for CI/CD pipelines.
Shift the Focus to Material Risk
The goal is not merely to identify potential vulnerabilities but to prioritize and address the most significant risks.
Vulnerability Prioritization
Continuous Monitoring
Threat Intelligence Integration
A Force Multiplier for Your Security Team
Praetorian's Offensive Experts Permanently Stand Side-by- Side with Our Customer's Defensive Teams
We Consolidate and Save Money
We consolidate attack surface management, vulnerability management, continuous penetration testing, breach simulation, and exploit intelligence into a single cost-effective platform.
We Include Security Experts
Our team of offensive security experts provides continuous support, aligning your security strategy with best practices and emerging threats.
We Are All Signal and No Noise
We prioritize only critical and validated risks, ensuring you focus your time and resources on what truly matters.
We Give Your Team The Ammo It Needs
As an external third party, we help you obtain the buy-in from the business to fix the risks we uncover through demonstration of impact and hard evidence.
We Got Compliance Covered
Our tech-enabled service meets annual penetration test requirements, ensuring compliance and adding value to your security efforts.
We Verify Mitigation
We ensure identified risks are remediated and provide third-party validation, supporting your IT teams every step of the way.