Path.Combine Security Issues in ASP.NET Applications
Path traversal vulnerabilities are a common class of web application vulnerability, where an attacker aims to access files outside of the intended directory by using “../” patterns to traverse directories or by using absolute paths. These vulnerabilities are commonly found in file upload or download functionality of an application.
Well-tested Authorization Design Patterns

Authorization is a strange beast. In theory, it appears to be rather straight-forward: a user should not be able to create, read, update, or delete data that it does not have access to. However, from our experience, theory tends to deviate from practice. Missing or incorrect access controls are a dime a dozen for applications we test and this very rarely stems from a complete lack of access controls. More often then not, authorization issues spring up during assessments where the application manages a complex authorization model and an incorrect assumption was made or an edge case was missed. Conversely, we have seen applications that have incredibly complicated authorization models that have zero access control problems.
An Opinionated Series on Why Signal Protocol is Well-Designed: Deniability
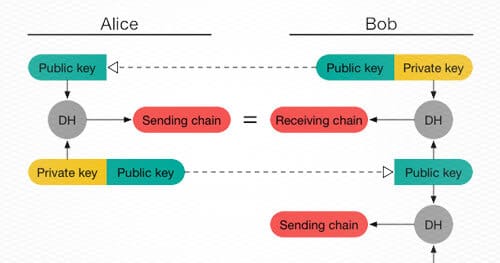
In my previous blog post covering WhatsApp end-to-end encryption, I spoke about Signal Protocol and how certain design decisions allowed Signal Protocol to be efficient on mobile devices. For this blog post, I’ll cover deniable authentication, how it has worked in the Off-The-Record (OTR) Messaging protocol, and how Signal Protocol has approached this problem. Deniable authentication tries to digitally recreate “off-the-record” conversations in the physical realm. If you tell Bob an embarrassing story in-person and Bob proceeds to tell Mallory about that story, it is possible for you to claim that Bob made the story up. Conversely, if you were to “sign” every statement you have ever made to Bob it would be practically impossible to deny that you told that story to Bob.
Engineering Efficiency and Continuous Improvement in Security Services
Highlight is a simple utility that creates an image from a text stream, automatically draw boxes around user defined content and automatically blurs sensitive content.
Sometimes we have a text stream, such as the output of a configuration file, and we want to include that as an image into a document. At the same time, we might want to highlight a particular string of text that’s found and we might want to hide other details that might contain things such as passwords. We could use a screen capture utility and then proceed with marking up the image. This leads to inconsistent boxes around text and certainly does not lend itself to automation.
With this utility, the entire process can be automated.
End-to-End WhatsApp: An Opinionated Series on Why Signal Protocol is Well-Designed

WhatsApp recently announced that client communications are now end-to-end encrypted using Open Whisper System’s “Signal Protocol” (previously Axolotl). This has received quite a bit of press lately due to WhatsApp's massive user base, along with the controversial going dark debates. Less importantly, the crypto-nerd in me loves Signal. Because of all of this, I thought I would write a blog series on some of Signal's design decisions that I feel are well-designed.
Secure Password Storage in Go, Python, Ruby, Java, Haskell, and NodeJS
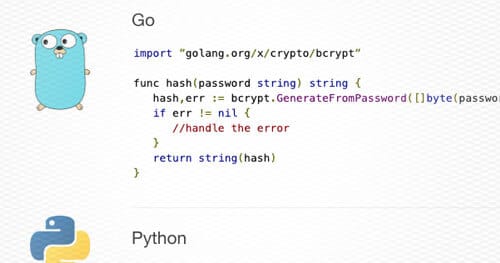
In order to authenticate users, web applications often store user passwords. This can be tricky, because password storage mechanisms are a watering hole for bad advice: there are several solutions to this problem but very few are truly secure. If you store the passwords of your users, your goal should be to make sure that in the event of a data compromise, user passwords should remain safe. The best way to store users passwords is to use a password-based key derivation function (PBKDF) with a sufficient work factor. If your application does not leverage a PBKDF, you should migrate password storage schemes immedietely. More on this later.
Machine Learning Tutorial

We see huge benefits of machine learning in the field of computer security. Much of the work we do on a daily basis can be automated and classified by a machine, leaving us to focus on more interesting and challenging problems. One stunning example is the automated binary exploitation and patching research funded by DARPA for the Cyber Grand Challenge. Problems like these are the stepping stones that will lead us to a future of automated computer security. To encourage future candidates (and ourselves) to delve into the world of machine learning, we built a new technical challenge to test the waters. The challenge is based on a CTF problem from SECCON, discovered by @ctfhacker, and features a mysterious compiler that always produces unique binaries.
Ruby Unsafe Reflection Vulnerabilities
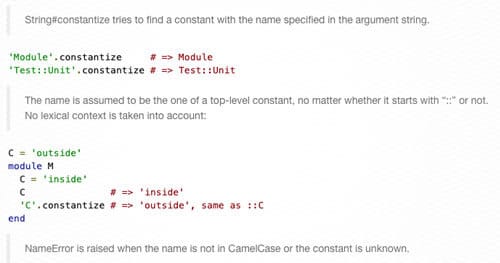
One of the interesting properties of Ruby is the fact that everything is an object. The manipulation of objects at runtime is what makes Ruby so flexible and interesting as a language. At its heart, this is the idea behind reflection. Reflection is a tool to allow a program to examine and modify its own behavior at runtime, granting programmers the ability to simpilify certain constructs (e.g. framework development, dependency resolution).
Introducing MitM-VM & Trudy: A Dead Simple TCP Intercepting Proxy Tool Set
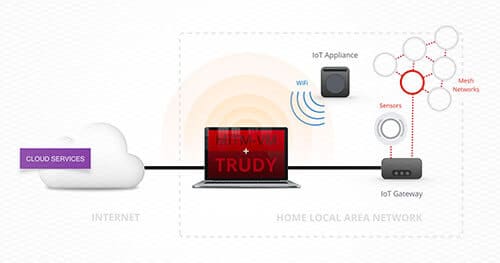
Positioning yourself as a man-in-the-middle (MitM) is a powerful situation to leverage during a security assessment. Unfortunately, in some situations, leveraging an active MitM position is difficult. There are existing proxies that try to alleviate these issues but they all seem to suffer from a flaw that makes using the tool undesirable. MitM-VM and Trudy are a complimentary set of tools that are designed to address several issues with existing proxies. Together they enable easy-to-setup and powerful man-in-the-middle positions. Why build these tools? Modifying custom binary protocols on the fly while sitting between an embedded device and a server is usually a slow process that involves sniffing legitimate traffic and then rebuilding packets programmatically. Trudy makes this process easy by enabling Burp-like features for generalized TCP traffic.
Javascript Sensor API and New Browser Features Raise Privacy Concerns
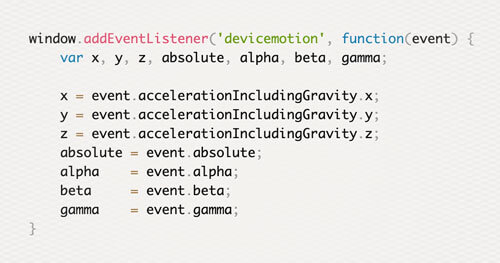
The W3 specs get updated and expand faster than most people can keep up with them. In 2015, many browsers began adding support for mobile sensors which do not prompt users for permission to access them. The new Javascript sensor API and browser features should start raising privacy concerns. These new features allow web applications to be more powerful and ultimately replace the role of many mobile apps. As both a developer and user, it’s important to stay aware of new features and to be mindful of what a website is capable of doing to your mobile device.