Why You Should Add Joern to Your Source Code Audit Toolkit
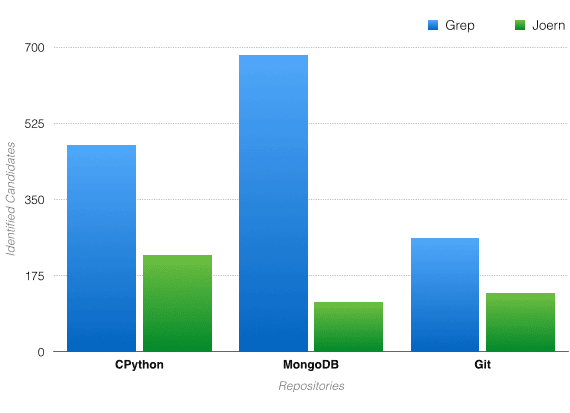
Joern is a static analysis tool for C / C++ code. It builds a graph that models syntax. The graphs are built out using Joern’s fuzzy parser. The fuzzy parser allows for Joern to parse code that is not necessarily in a working state (i.e., does not have to compile). Joern builds this graph with multiple useful properties that allow users to define meaningful traversals. These traversals can be used to identify potentially vulnerable code with a low false-positive rate.
Using Developer Debugging Tools to Pentest Mobile Applications
During a recent assessment, I was pentesting a hybrid mobile application that is a companion to a web application. The applications allow users to collaborate while creating new interactive digital content. Through the web interface, content creators are allowed to upload a wide range of files, including HTML files, and share the content with other individuals in their organization. Thus, any user with proper permissions is able to view and edit shared content.
Man-in-the-Middle TLS Protocol Downgrade Attack
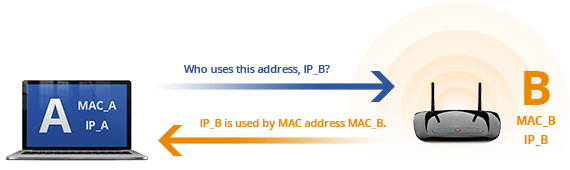
A flaw was recently found in OpenSSL that allowed for an attacker to negotiate a lower version of TLS between the client and server (CVE-2014-3511). While this vulnerability was quickly patched, an attacker that has control of your traffic can still simulate this attack today. Let’s explore how this is possible through looking at man-in-the-middle attacks and how browsers handle SSL/TLS connections. In addition, we will see the implications of the attack on cryptographic security.
MAC Cryptographic Errors and Vulnerabilities in SSO Authentication
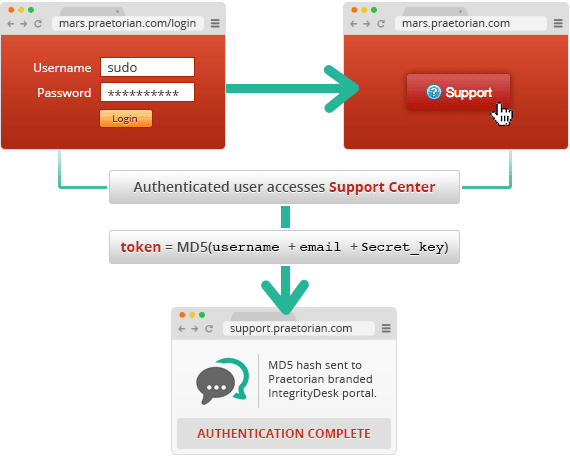
In-house crypto is often a goldmine of cryptographic errors and vulnerabilities. In this post, I’ll describe one of the glaring errors discovered in an online customer support and help desk solution we were considering for use in Praetorian’s cloud-based password cracking service, Project Mars. Hopefully, this can serve as a warning to anyone thinking about writing his or her own crypto libraries.
Exploiting Mobile Banking with HeartBleed Vulnerability

For anyone who has not heard, a critical SSL vulnerability called HeartBleed was made public earlier this week that affects a widely used version of OpenSSL. In this post, I will demonstrate the HeartBleed vulnerability being exploited on a vulnerable mobile banking application and backend server within our test environments.
CRITICAL: HeartBleed Vulnerability
There is a new critical vulnerability affecting a widely used version of OpenSSL called HeartBleed (CVE-2014-0160). This new bug allows an attacker to read system memory remotely, without authentication. It has been reported that 60-70% of the Internet is affected. Immediate action should be taken to identify vulnerable systems within your environment and take necessary steps to mitigate risk associated with this critical vulnerability.
Whats up with WhatsApp’s Security?

Facebook’s acquisition announcement coincided with the starting week of Project Neptune’s beta program. Project Neptune is Praetorian’s new mobile application security testing platform that allows companies to keep pace with rapid mobile development cycles by incorporating continuous, on-demand security testing. And what’s a better way to properly kick off our beta program than to test a publicly available mobile app worth $19 billion? Within minutes, Project Neptune picked up on several SSL-related security issues affecting the confidentiality of WhatsApp user data that passes in transit to back-end servers. This is the kind of stuff the NSA would love. It basically allows them—or an attacker—to man-in-the-middle the connection and then downgrade the encryption so they can break it and sniff the traffic. These security issues put WhatsApp user information and communications at risk.
How to Identify and Prevent UIWebView Cross-Site Scripting

Cross-site scripting occurs when malicious scripts are injected into an otherwise benign or trusted website. Within the mobile security field, cross-site scripting can occur in unlikely places, such as the UIWebView on iOS. For purposes of illustration, we’ll discuss a recent instance of UIWebView cross-site scripting we came across in a test. We’ll also discuss a similar app that does things correctly. Then we’ll cover why problems like this occur and how it’s difficult for developers to foresee these security issues.
How To Identify and Prevent LDAP Injection (Part 2)

LDAP injection occurs when an application fails to neutralize characters that have special meaning in LDAP. Closely, resembling SQL injection, LDAP injection occurs when LDAP statements are constructed with unverified user-supplied data. This can result in the execution of arbitrary commands such as granting permissions to unauthorized queries as well as content alterations within the LDAP tree. The same advanced exploitation techniques leveraged in SQL Injection can be similarly applied in LDAP injection.
How To Identify and Prevent Query and Command Injections (Part 1)

Query and command injections are some of the most devastating classes of vulnerabilities in existence. This series of blog posts will teach you how to identify and prevent this vulnerability from occurring. In part one we will explore examples of command injection.