Develop Secure Mobile Apps by Studying Vulnerable Android, iOS, and Mobile Web Apps
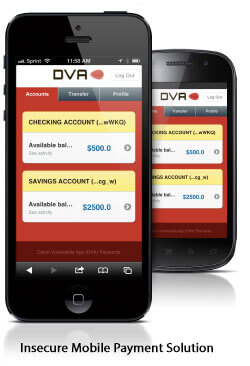
In today’s mobile world, demand for high-quality, feature-rich applications is increasing, while mobile app development cycles are becoming shorter. With time-to-market pressures greater than ever, security vulnerabilities are manifesting themselves in every stage of the mobile app development life cycle. For our summer internship project, we wanted to come up with a way to help developers create more secure mobile apps.
Introducing the New ROTA Tech Challenge
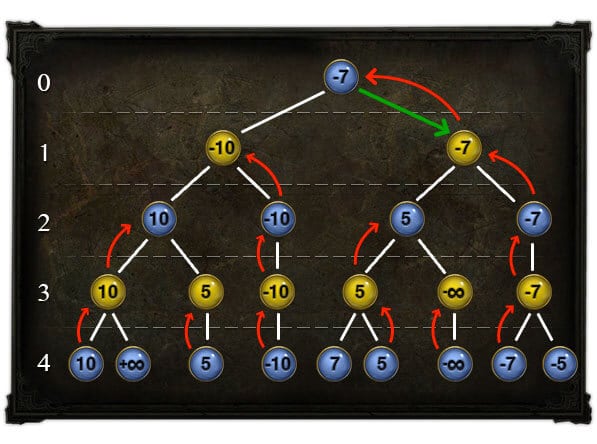
Hello everyone! I first want to introduce myself, my name is Anthony Marquez and I am the newest member of Praetorian’s technical team. I’m excited to join a group of such bright individuals and work with a company that values the promotion of thought leadership and realizes the importance of allowing their employees to take on interesting side projects. I hope to be contributing to several blog posts in the future. For my first post I wanted to talk about one of the first side projects that I recently completed here at Praetorian —ROTA.
Burp SQLmap plugin for Windows
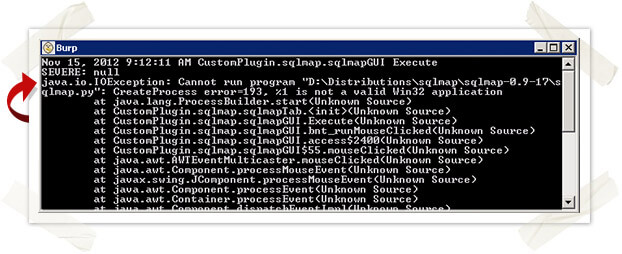
Burp Suite provides a very basic SDK known as Burp Extender. Burp Extender allows third parties to extend the features of an already powerful web application testing suite. In March of this year, Daniel Garcia (cr0hn) created a SQLmap plugin for Burp using the Burp Extender SDK. With Daniel’s SQLmap plugin, automated SQL injection discovery and exploitation is now seamless between two of our favorite web application pentesting tools.
Twitter’s Charlie Miller is Coming to Austin ISSA to Discuss iOS Security
Praetorian is excited to be a platinum sponsor for the upcoming ISSA Chapter Meeting on Wednesday, November 7 from 11:00am to 3:00pm at St. Edwards Professional Education Center. The event will feature the famous/infamous security researcher Charlie Miller.
Praetorian sponsors 2012 Boston Application Security Conference (BASC)

Praetorian is excited to sponsor and attend the upcoming 2012 Boston Application Security Conference (BASC). The Boston Application Security Conference (BASC) will be held Saturday, Oct. 13, from 10 a.m. – 6:30 p.m. at Microsoft’s New England Research & Development Center at One Memorial Drive, Cambridge. Admission to the BASC is free but registration is required for breakfast, lunch, and the evening social time.
Multi-Core and Distributed Programming in Python
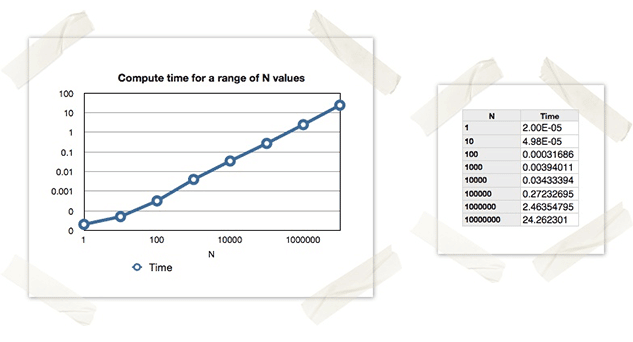
In the age of big data we often find ourselves facing CPU-intensive data processing tasks, therefore it is useful to understand how to harness all available CPU power to tackle a particular problem. Recently we came across a Python script which was CPU-intensive, but when the analyst viewed their overall CPU usage it was only showing ~25% utilization. This was because the script was only running in a single process, and therefore only fully utilizing a single core. For those of us with a few notches on our belts, this should seem fairly obvious, but I think it is a good exercise and teaching example to talk about the different methods of multi-core/multi-node programming in Python. This isn’t meant to be an all-encompassing tutorial on multi-core and distributed programming, but it should provide an overview of the available approaches in Python.
Effectively Measuring Risk Associated with Vulnerabilities in Web Applications
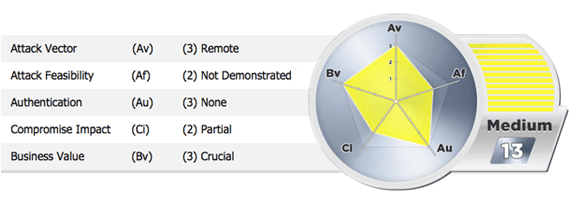
An objective risk rating framework enables our team to compare a standardized measurement of risk across an organization. It also allows our clients to prioritize steps needed in an action plan to mitigate, accept, or transfer organizational risk. Prioritization of vulnerability remediation should be organized objectively based on factors used in the risk rating framework, such as: ease of exploitation, severity of impact if exploited, and level of effort to remedy. If you are considering adopting a risk-rating framework, it is important to tailor a solution that best suits your organizational needs. The following risk rating scale was developed to satisfy the specific needs of our clients, and we hope it provides you with valuable guidance as you plan for the management of risk within your organization…