Nosey Parker Turns Two: Celebrating Two Years of Open-Source Secrets Discovery

Praetorian’s open-source secrets detection tool, Nosey Parker, was released two years ago. Learn more about updates Nosey Parker and importance in today’s environment.
Cutting Through the Noise: Chariot’s Zero False Positive Guarantee
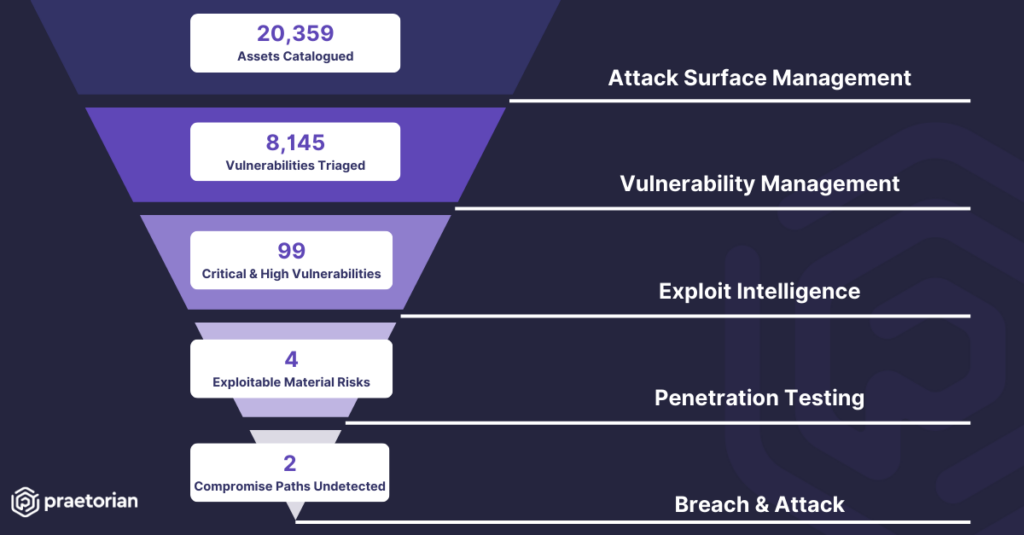
For years, cybersecurity teams have fought a persistent battle: overwhelming noise generated by vulnerability tools. It’s a familiar scenario – overtaxed security teams drowning in alerts, many leading to false positives or low-priority issues. Fatigued and lacking priorities, they risk missing critical vulnerabilities. While scanners aren’t intentionally built to generate needless noise, it’s an inevitable […]
Secrets Exposed: The Rise of GitHub as an Attack Vector

A Look at Chariot’s Capability to Protect On June 6, 2024, an anonymous user posted nearly 300 GB of stolen source code to 4chan. Per the user, the leak contained “basically all source code belonging to The New York Times”. The NYT later confirmed the leak and said the root case was an exposed GitHub […]
Chariot Continuous Threat Exposure Management (CTEM) Updates
Our engineering team has been hard at work, reworking our flagship Chariot platform to remain the most comprehensive and powerful CTEM platform on the market. So what’s new? Here are several new features recently added to Chariot: 1. Unmanaged Platform Chariot, Praetorian’s Continuous Threat Exposure Management (CTEM) solution, is now available as a self-managed platform. Organizations can […]
In Brief: Chariot Alignment with FDA Section 524B.1

Chariot is more than a product; it’s a partnership that combines automated monitoring and human analysis to identify externally-accessible security risks. In light of the FDA’s latest requirements for in-market device security (summarized in Section 524B), Praetorian’s customers are having success leveraging the Chariot Managed Service as a cost-effective and scalable approach to satisfying Section […]
Cyber Cartography: Mapping a Target
As Phil Venables has said, “at some level, cyber defense is a battle over whether the attacker or defender has better visibility of the target. Action is key, yes, but without good ‘cyber cartography’ it can be hard to act in the right way.” An attacker’s first step is enumeration, or identifying what looks hackable. […]
Screenshotting: Can You See What I See?
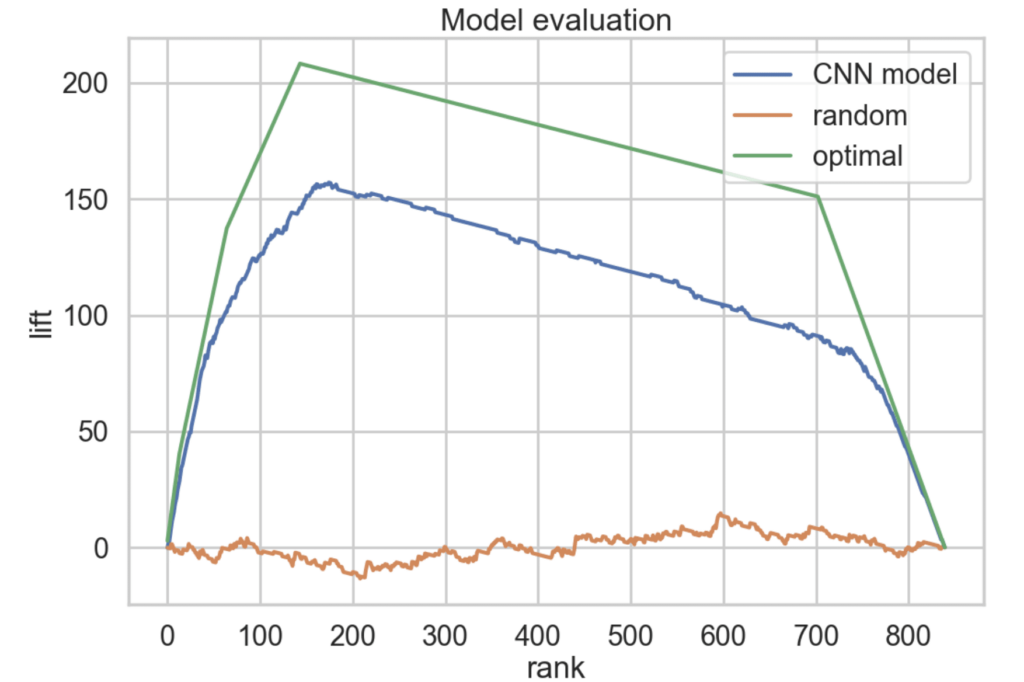
At Praetorian, we firmly believe that the most effective way to secure your systems is to look at them through an offensive lens. After all, when you view yourself the same way an attacker does, you get a better understanding of which defenses are likely to be effective. When building Chariot, our External Attack Surface […]
ASM: The Best Defense is a Good Offense
About 10 years ago, security was relatively simple because everything occurred on premises. Change releases were tightly controlled by a change ticket and review process. In contrast, current networks consist of auto-scaling containers that run in Kubernetes clusters and even serverless clusters like AWS Lambda. We have transitioned from constrained environments that humans closely scrutinized […]
Introducing FingerprintX: The fastest port fingerprint scanner

Introduction Port fingerprinting can detect specific services running on a network, which makes it useful during penetration tests. It expands visibility into potential attack surfaces and vulnerabilities within the network environment. Over the summer, our interns worked towards developing a new tool for port fingerprinting services: Fingerprintx Fingerprintx is a port fingerprinting utility tool useful […]
Multi-Step Attack Vectors: When Vulnerabilities Form an Attack Chain
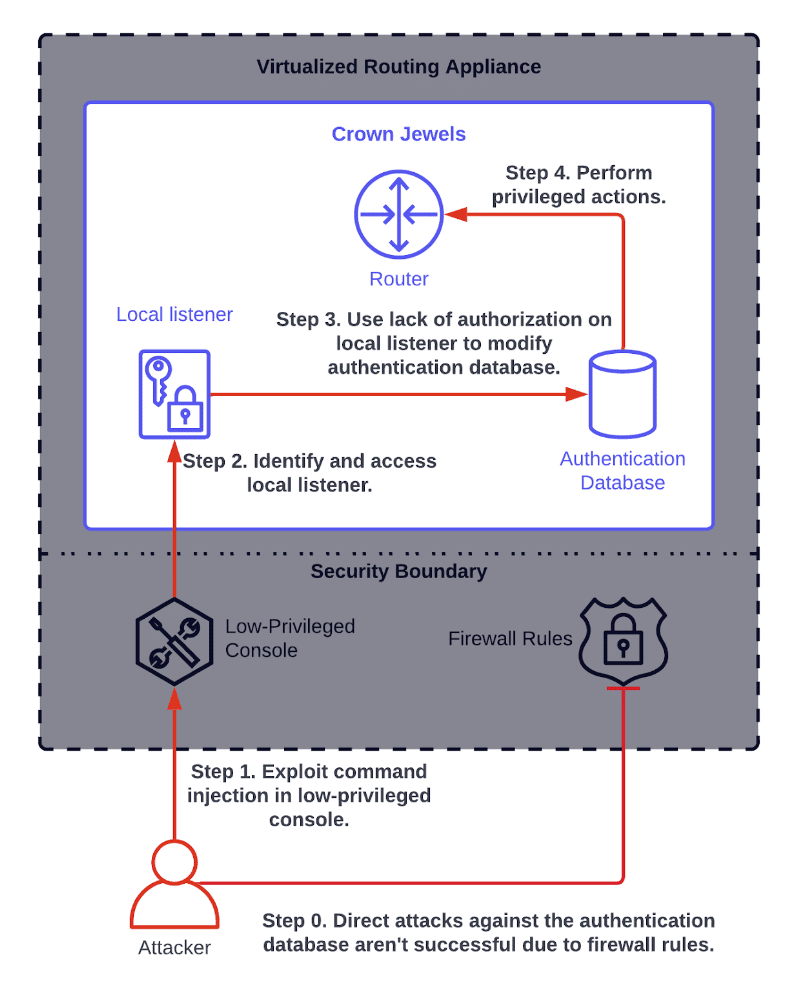
Praetorian’s approach to cybersecurity centers around a core belief that combining innovative technologies and the best people in the business leads to real results. In our experience, neither can fully solve cybersecurity challenges on its own. We therefore have designed our services organization and offerings to blend them seamlessly. We applied the same philosophy when […]