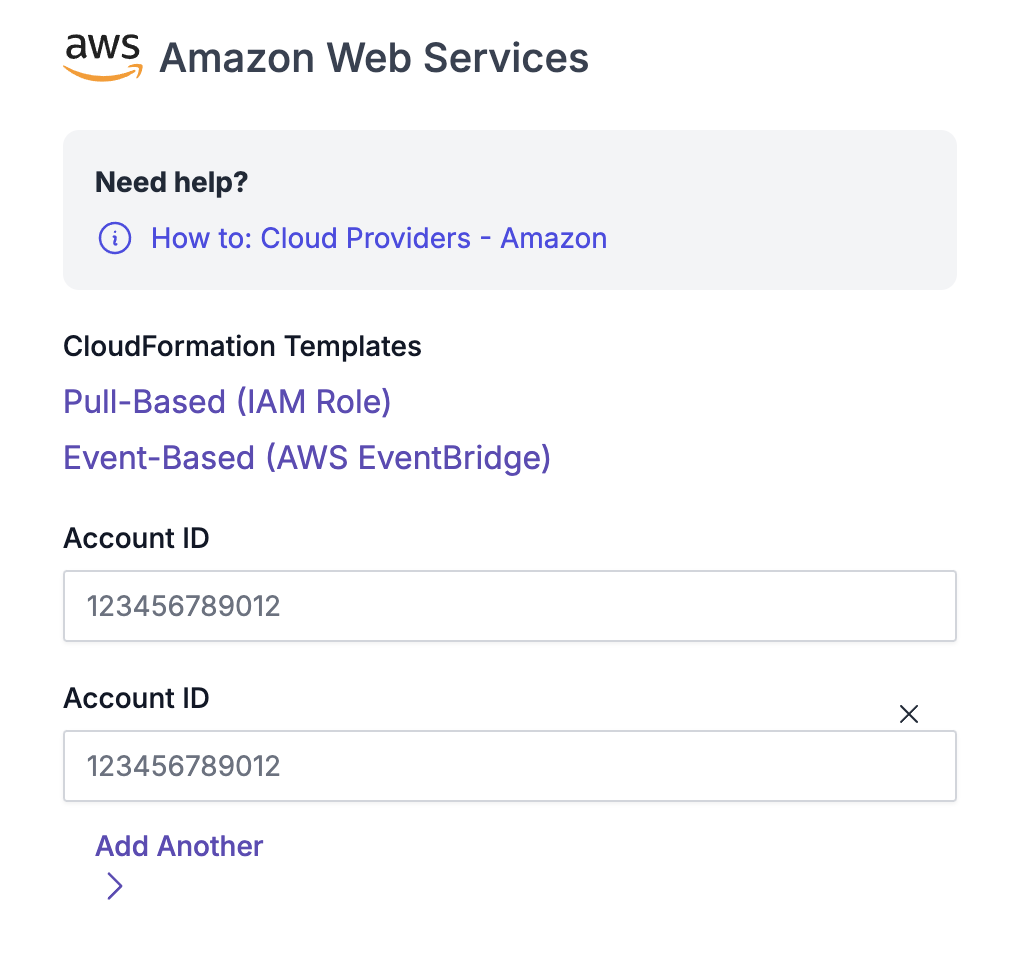
Amazon Cloud Integration Capability with Chariot
On March 22nd, 2019, CapitalOne experienced a data breach that resulted in the loss of more than 100 million credit card applications. This vulnerability resulted from a misconfigured web application firewall, which caused a server-side request forgery vulnerability. This issue then allowed an attacker to gain access to an AWS IAM role with access to […]
Exploiting Broken Authentication Control In GraphQL
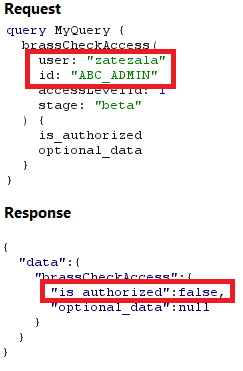
Overview The implementation of GraphQL in enterprise systems has grown rapidly. A recent report from Gartner predicted that at least 50% of enterprises will be implementing GraphQL in their production environments by the end of the calendar year. With its increasing adoption, correctly accounting for the security of GraphQL APIs becomes increasingly pertinent. Although the […]
Recursive Amplification Attacks: Botnet-as-a-Service
Introduction On a recent client engagement, we tested a startup’s up-and-coming SaaS data platform and discovered an alarming attack path. The specific feature names and technologies have been generalized to anonymize the platform. Like many data platforms, various source types could be configured to ingest data, such as third-party CRM or marketing services. The platform […]
Capturing Exposed AWS Keys During Dynamic Web Application Tests
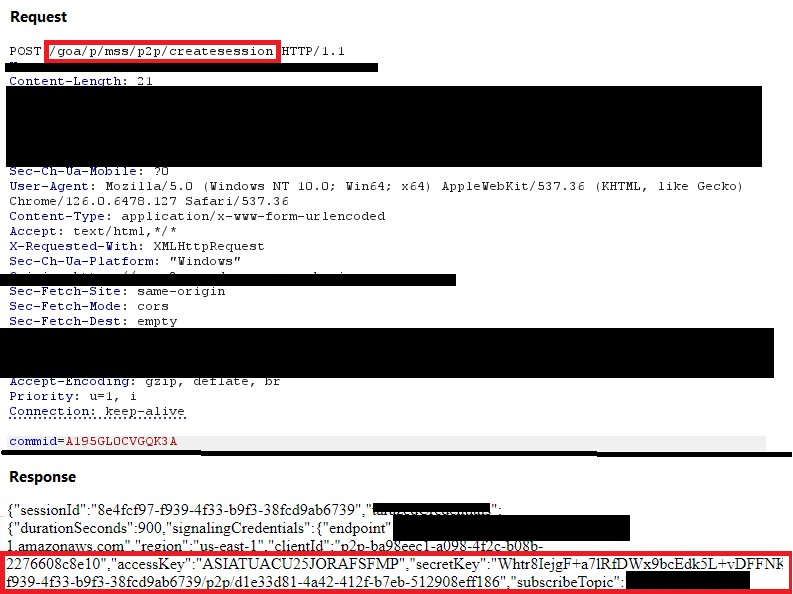
Overview We have recently identified several vulnerable HTTP requests that allow attackers to capture access keys and session tokens for a web application’s AWS infrastructure. Attackers could use these keys and tokens to access back-end IOT endpoints and CloudWatch instances to execute commands. This blog was developed to raise awareness on common design flaws in […]
Unconstrained Delegation in Active Directory
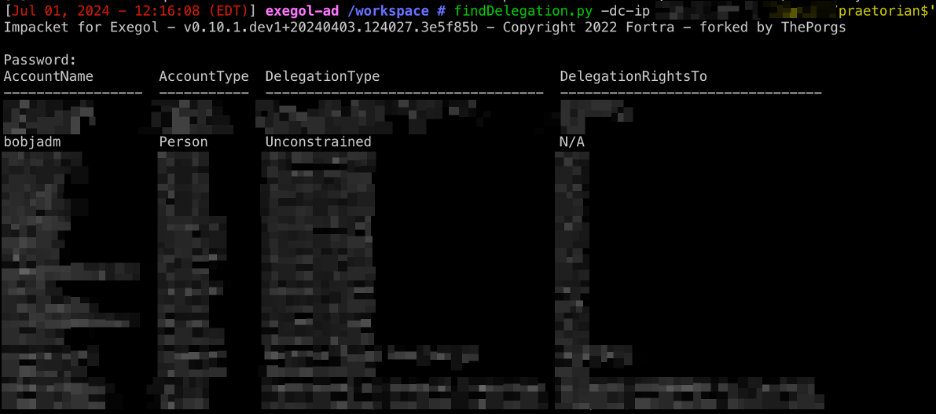
Overview Unconstrained delegation is a feature in Active Directory that allows a computer, service, or user to impersonate any other user and access resources on their behalf across the entire network, completely unrestricted. A typical example of a use case for unconstrained delegation is when certain services require access to another server or back-end database. […]
Why Azure B2C ROPC Custom Flows Are Inherently Insecure

Microsoft’s Azure Active Directory B2C service allows cloud administrators to define custom policies, which orchestrates trust between principals using standard authentication protocols. One such custom policy that B2C defines by default is the Resource Owner Password Credentials (ROPC) flow, which implements the OAuth standard authentication flow of the same name and allows users to simply […]
Konstellation: A Tool for RBACpacking in Kubernetes
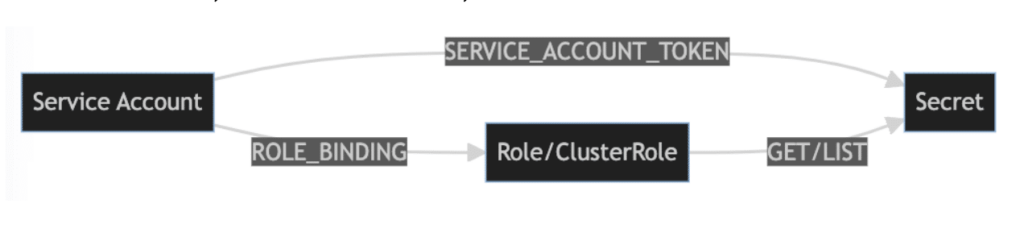
The author presented this paper and corresponding tool at Black Hat: Arsenal 2023 on August 10, 2023. For a more general overview of Konstellation and its capabilities vis a vis Kubernetes RBAC, please see our earlier companion post. Kubernetes Role-Based Access Control (RBAC) is a mechanism for controlling access to resources in a Kubernetes cluster. […]
Introducing Konstellation, for Kubernetes RBAC Analysis
Praetorian is excited to announce the upcoming release of Konstellation, a new open-source tool that simplifies Kubernetes role-based access control (RBAC) data collection and security analysis. Join us August 10, 2023, at Black Hat Arsenal 2023 for a deeper dive on exactly what this tool can do for you. Kubernetes RBAC is a powerful tool […]
fwd:cloudsec 2023: Top Four Themes in Cloud Security for 2023

At Praetorian, we pride ourselves on our extensive expertise in cloud security and our commitment to staying at the forefront of the ever-evolving landscape. We consequently were excited to attend the highly anticipated fwd:cloudsec 2023 conference held on June 12–13, in Anaheim, CA. This non-profit conference brings together cloud security professionals, researchers, and practitioners from […]
Technical Advisory – Azure B2C – Crypto Misuse and Account Compromise
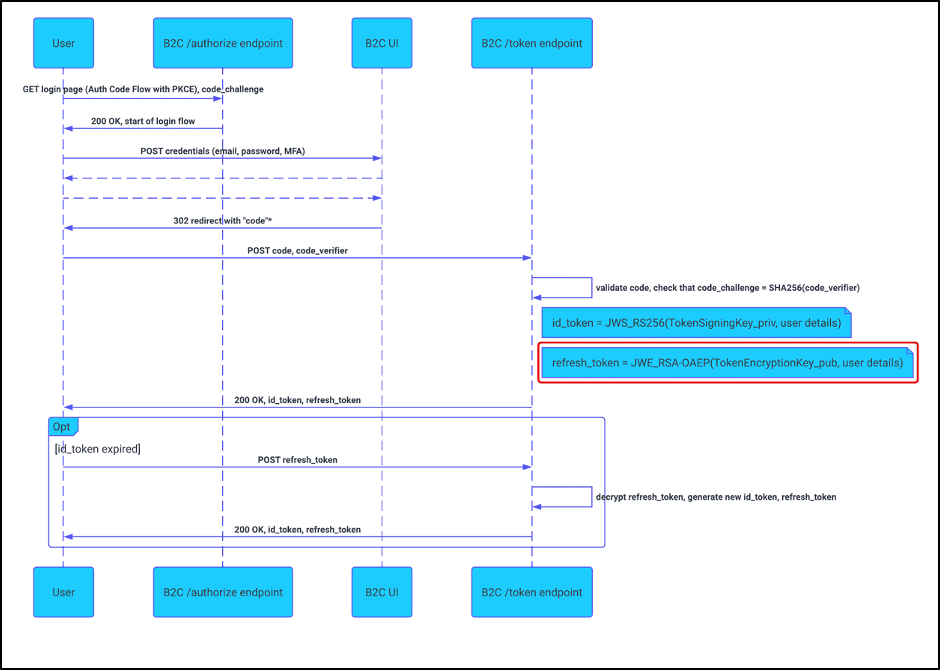
Microsoft’s Azure Active Directory B2C service contained a cryptographic flaw which allowed an attacker to craft an OAuth refresh token with the contents for any user account. An attacker could redeem this refresh token for a session token, thereby gaining access to a victim account as if the attacker had logged in through a legitimate […]