ABAC in Lambda
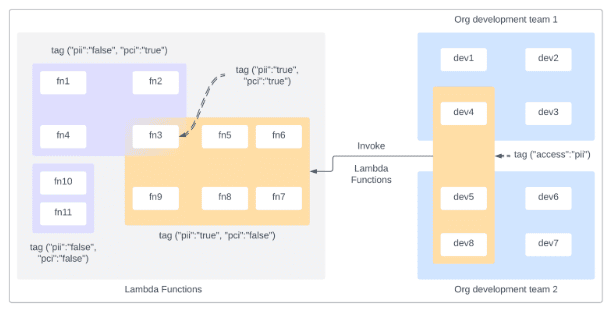
During August 2022 we published a blog discussing AWS Security Trends of 2022 , one of which was ABAC in Lambda. AWS allows administrators to use tags to designate attributes for both IAM and AWS resources. Attribute Based Access Control, or ABAC, is a strategy to allow permissions assignment based on the value of such […]
Best Practices for Identity and Access Management When Using Google Cloud Platform
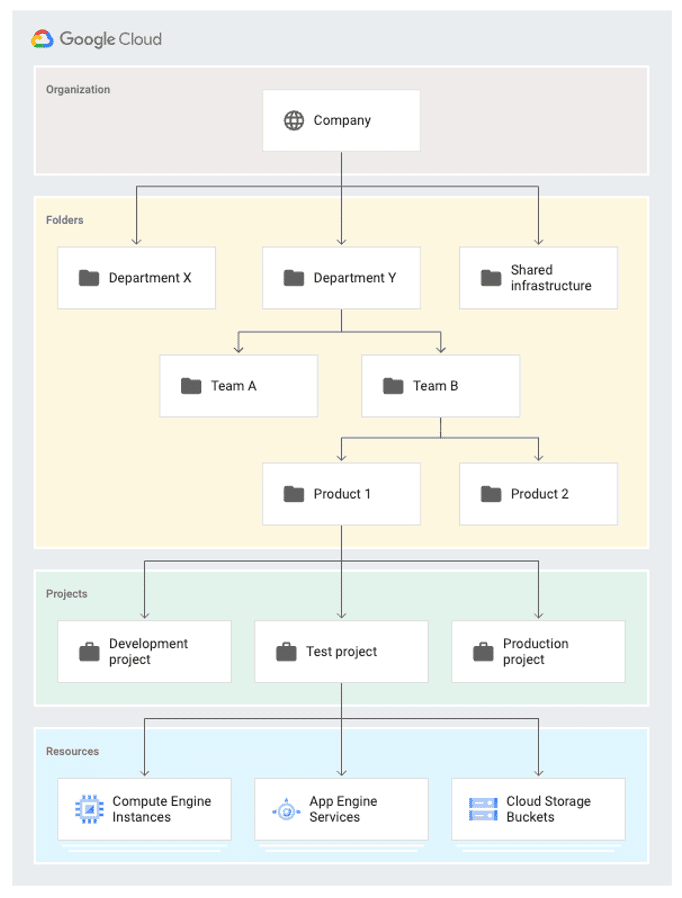
At Praetorian, one of our top priorities is looking over each client’s Identity and Access Management (IAM) structure. Several of our large clients use Google Cloud Platform (GCP), which is one of the top three cloud providers with about eight percent of the cloud services market share. During our work with GCP, we have noticed […]
AWS Security Trends of 2022: Five Themes and Why They Matter

Building securely in the cloud can feel daunting given the sheer volume of ever-changing information to review, assess, and deconflict for your business needs. For example, AWS releases countless updates, new features, and new security services around its summer security conference, re:Inforce. Praetorian analyzed all the information pertaining to AWS’s new releases and security related […]
Chaining MFA-Enabled IAM Users with IAM Roles for Potential Privilege Escalation in AWS

Overview In AWS, sts:AssumeRole is an action within AWS’s Security Token Service that allows existing IAM principals to access AWS resources to which they may not already have access. For example, Role A can assume Role B and then use Role B’s privileges to access AWS resources. Common use cases include assuming a role within […]
Guest who? Insecure Azure Defaults!
Introduction Azure has an insecure default guest user setting, and your organization is probably using it. The default settings Azure provides would allow any user within the organization (including guest users) to invite guest users from any domain, bypassing any central identity management solutions (e.g. Okta, Auth0) and onboarding processes. Additionally, an attacker may use […]
Introducing Snowcat: World’s First Dedicated Security Scanner for Istio

Why Service Meshes Matter Over the last few years, the pace of moving workloads to the cloud has continued to accelerate. Mostly, this has been a boon for innovation, allowing complex monolithic on-prem instances to be broken into microservice architectures, which provide decoupling, agility, and stability. From a development perspective, life has in some ways […]
10 Common Security Issues when Migrating from On Premises to Azure

Introduction Cloud migrations often involve moving data, workloads, and applications from an on-premise datacenter to a private or public cloud provider. While cloud migrations can offer significant cost savings, faster product deployments, and improved security controls, there are many common pitfalls to avoid during migration, along with best practices that should be followed to maximize […]
Google Cloud IAM: Designs for Self-Service Privilege Escalation

In a perfect world, all organizations would incorporate security into their cloud environments from the start. Unfortunately, common development practices tend to postpone the implementation of security controls in the product environment in favor of shipping product features. The reasons for this are manifold: an early-stage product may ignore robust security processes in favor of […]
Alibaba Cloud Cross Account Trust: The Confused Deputy Problem

In this second blog post in our series on cross-account trust, we explore Alibaba Cloud and the security implications of their trust model.
Google Cloud Platform (GCP) Service Account-based Privilege Escalation paths

This article examines a Google Cloud Platform (GCP) risk scenario, in which a malicious user can use their privileges in a compromised service to further escalate their privileges.