Leveraging DevSecOps Practices to Secure Red Team Infrastructure
This article explores how Red Teams can leverage DevSecOps best practices, including automating policy enforcement using OPA for secure Red Team Architecture
Cloud Security and Architecture: The 8 Pillars

Praetorian has created a 8-pillar framework to simplify the assessment of multi-cloud environments across a broad client base. Together with proven methodologies for enterprise and product security, the framework provides a holistic approach to securing organizations from chip to cloud.
AWS IAM Assume Role Vulnerabilities Found in Many Top Vendors

Research by Praetorian has uncovered a common misconfiguration in Amazon Web Services Identity and Access Management Assume Role process. This post outlines the issue and how it can be mitigated.
CI/CD Supply Chain Attacks for Data Exfiltration or Cloud Account Takeover
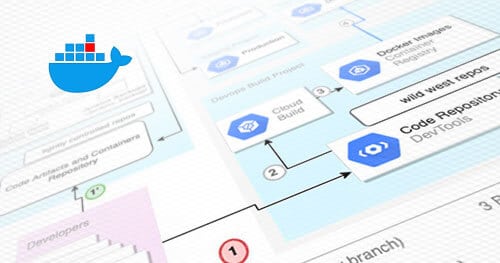
The great challenge of securing CI/CD lies in the nature of the beast. Building arbitrary code and CI/CD scripting tools grant the attacker RCE from the get-go. In this blog we examine a fairly robust architecture, how to break it, and how to further harden the design.
Secure and Scalable Secrets Management in the Cloud for DevOps
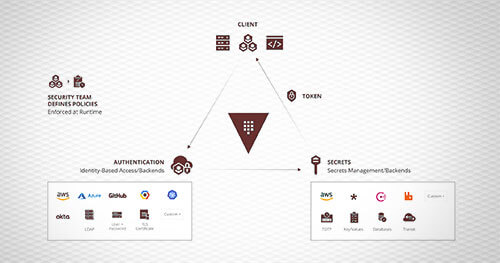
Regardless of industry, size, or tech stack, modern organizations rely on secrets to operate their infrastructure. Increasingly, DevOps teams elect to build or migrate their infrastructure with the cloud. All too often, secure and scalable secret management strategies are forced onto the backlog for the sake of development velocity or underappreciated implications. Ad hoc secret management strategies can have disastrous implications – as application security weaknesses can readily metastasize into complete infrastructure compromise. With increasing complexity and modernization, DevOps operators need a standard method for managing and maintaining secrets within modern environments.
Cloud Data Exfiltration via GCP Storage Buckets and How to Prevent It

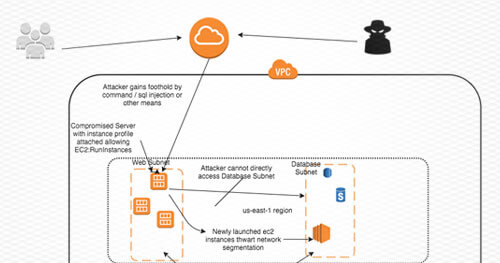
On a recent engagement, we gained the ability to execute code on a pod which we compromised through a SQL injection vulnerability. With the SQL injection, we could write pickled python objects to a table in a database and those objects would be unpickled and executed by a different pod. The customer was using a Private Kubernetes GKE cluster and had restricted all egress traffic to pass through a network proxy which denied general access to the Internet. This prevents standard exfiltration of data from the pod. However, the pods had permissions to write to GCP Storage Buckets, and therefore, the storage.cloud.google.com URL was whitelisted.
Privilege Escalation in AWS with PassRole Attacks
All instances launched by AWS by default have instance credentials supplied by the AWS metadata service. AWS operators can attach PassRole policies given to an instance at launch time.
Navigating Today’s Shared Security Responsibility Model in the Cloud
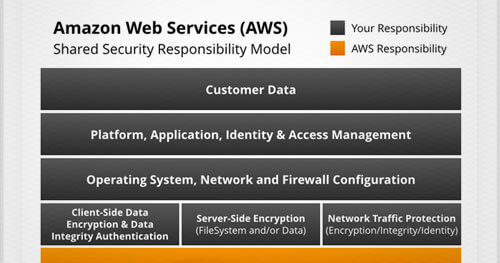
How do you protect the confidentiality, integrity, and availability of systems and data in your organization’s growing cloud environments? It starts by understanding your responsibility.
Addressing security in a public cloud environment is slightly different than in your on-premises data centers. When you move systems and data to the cloud, security responsibilities become shared between your organization and the cloud service provider. Infrastructure as a Service (IaaS) providers, such as Amazon Web Services (AWS), are responsible for securing the underlying infrastructure that supports the cloud, and you are responsible for anything you put on the cloud or connect to the cloud.
Cloud Security Best Practices for Amazon Web Services (AWS)

Over the last 18-months we have seen more and more of our clients turn to IaaS (Infrastructure-as-a-Service) providers to support their enterprise infrastructure needs. While there are obvious benefits to utilizing these types of services, such as reducing the complexity associated with managing an enterprise infrastructure, moving to the cloud can also introduce new security concerns. Most often these concerns arise as a result of misconfigured cloud instances.