Long Live the Pwn Request: Hacking Microsoft GitHub Repositories and More
Software supply chain attacks have been increasing both in frequency and severity in recent months. In response to these attacks, the CISA has even released a cybersecurity information sheet (CSI) on how organizations can secure their CI/CD pipelines. The introduction to the CSI states: “(The) CSI explains how to integrate security best practices into typical […]
Helpdesk Telephone Attack: How to Close Process and Technology Gaps
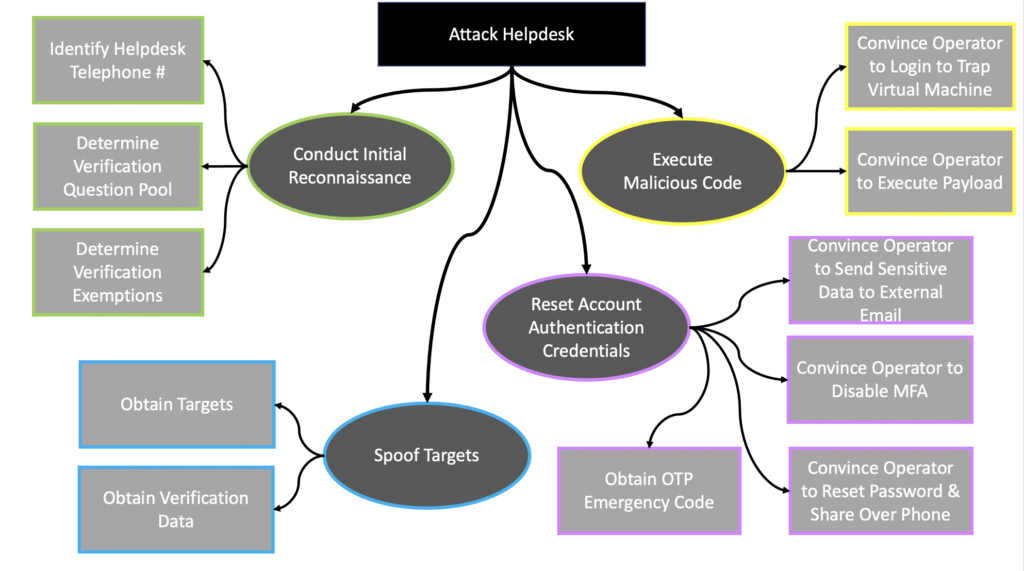
Introduction As we have witnessed in recent weeks with the MGM and Caesars Entertainment breaches, helpdesks are prime attack surfaces that are seeing a surge in exploitation. Although much of the press surrounding these most recent events alludes to helpdesk operators’ roles in the exploits, this type of vulnerability actually is a technology and process […]
Announcing Gato Version 1.5!

On January 21, 2023 at ShmooCon 2023, Praetorian open-sourced Gato (Github Attack Toolkit), a first of its kind tool that focuses on abusing offensive TTPs targeting self-hosted GitHub Actions Runners. Since then, Praetorian and other offensive security practitioners across the information security community have leveraged Gato for so much more than just self-hosted runner attacks. […]
Phantom of the Pipeline: Abusing Self-Hosted CI/CD Runners

Introduction Throughout numerous Red Teams in 2022, a common theme of Source Control Supply Chain attacks in GitHub repositories has emerged. After many hours manually hunting for and exploiting these attack paths, we’ve built an all-in-one toolkit called Gato (Github Attack Toolkit) for finding and attacking repositories where these misconfigurations are present. We released the […]
Automating the Discovery of NTLM Authentication Endpoints
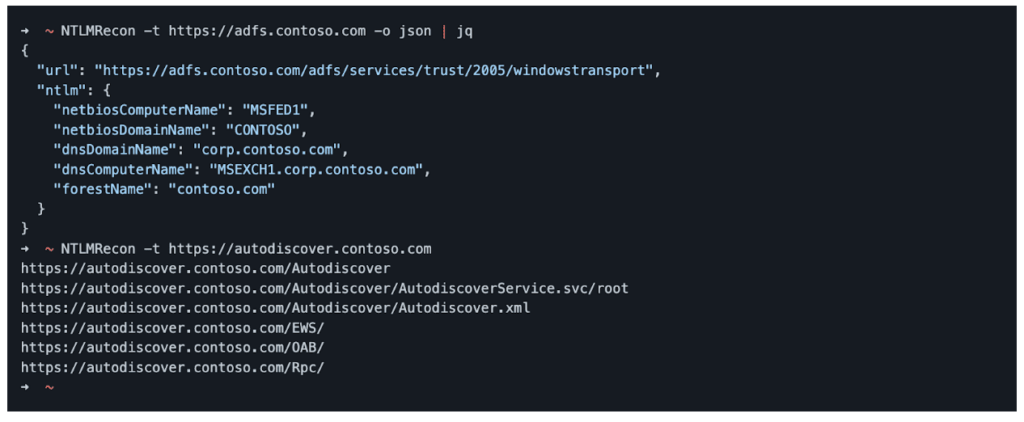
Recently, I have been working on adding support for automated enumeration and discovery of NTLM authentication endpoints to Chariot, our external attack surface and continuous automated red teaming product. Our red team requested this feature as a way to identify NTLM authentication endpoints exposed over HTTP that they could potentially leverage for password spraying attacks […]
From Self-Hosted GitHub Runner to Self-Hosted Backdoor
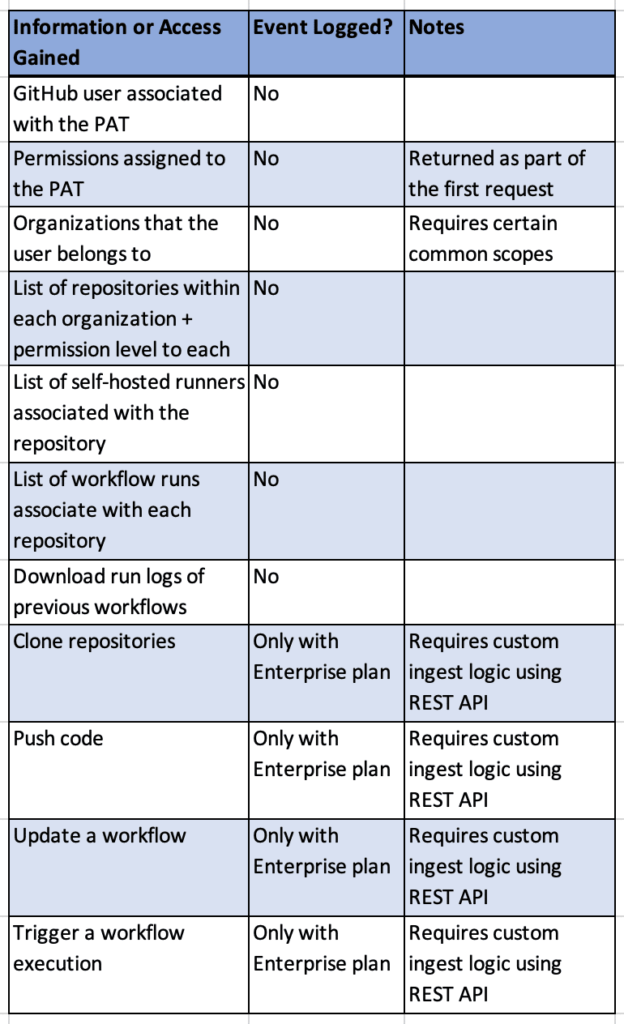
Overview Continuous Integration and Continuous Delivery (CI/CD) systems are powerful and configurable tools within modern environments. At Praetorian, we are seeing organizations migrate to SaaS solutions like GitHub (GitHub.com) as their source code management and CI/CD solution, instead of on-premises tools like BitBucket, Bamboo, and Jenkins. On our Red Team engagements , we routinely employ […]
Developing a Hidden Virtual File System Capability That Emulates the Uroburos Rootkit

A few years ago, I read the “Uroburos: The Snake Rootkit” [1] paper written by Artem Baranov and Deresz and was captivated by the hidden kernel-mode Virtual File System (VFS) functionality implemented within Uroburos. Later, I decided to learn Windows device driver programming and thought replicating this functionality within my own rootkit would be an […]
NTLMv1 vs NTLMv2: Digging into an NTLM Downgrade Attack

Overview During the summer, my colleague Derya Yavuz and I published an article on some of the different methods we’ve leveraged to elevate privileges within Active Directory environments. We discussed authentication coercion techniques such as PrinterBug, PetitPotam, and DFSCoerce. One of the techniques we mentioned in that article was performing an NTLM downgrade attack to […]
Thinking Outside the Mailbox: Modernized Phishing Techniques
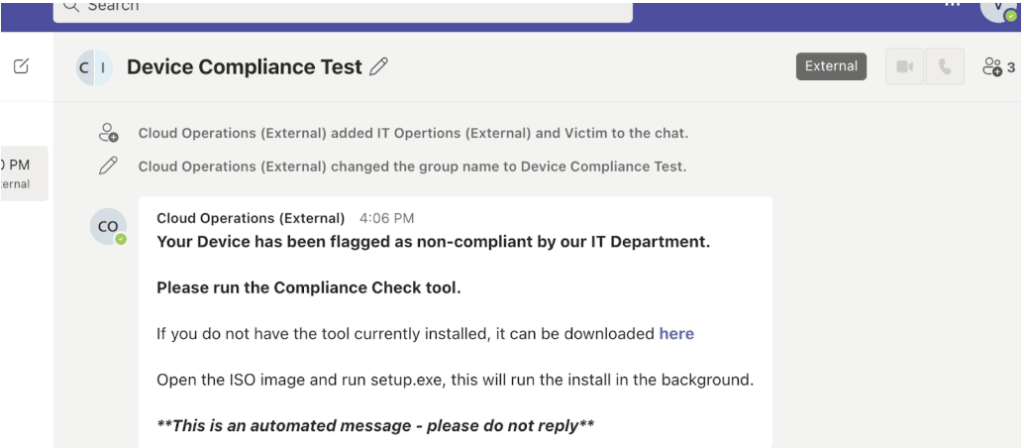
As defensive controls have advanced, so too have adversaries’ approaches to social engineering. Landing a phishing email in an inbox has become harder, and most campaigns that do make it to an inbox are quickly reported, quarantined, or triaged. So, adversaries have asked themselves why not skip the inbox all together or leverage a service […]
Elevating Privileges with Authentication Coercion Using DFSCoerce
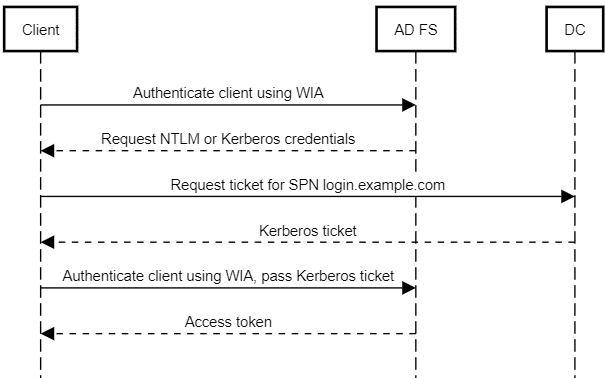
Background In our previous blog post, we talked about the recently-published DFSCoerce utility which is useful for forcing NTLM or Kerberos authentication by interacting with the Distributed File Service (DFS) over Remote Procedure Calls (RPC) on Windows. This forces the victim to authenticate into the attacker’s machine, very much like authentication coercion tools like PetitPotam […]