How to Detect DFSCoerce
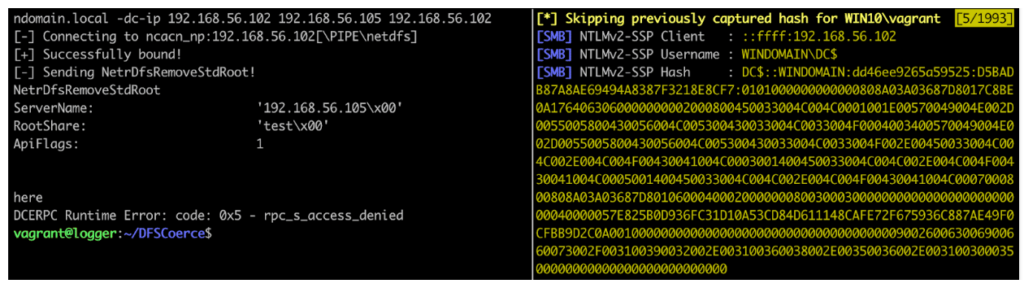
Background On 18 June 2022, security researcher Filip Dragovic published proof-of-concept code for a new forced authentication technique named DFSCoerce. This technique, inspired by other forced authentication techniques like PetitPotam and SpoolSample, often is used to force a victim Windows host to authenticate to an attacker’s machine. The attacker can then relay the credentials to […]
Relaying to ADFS Attacks
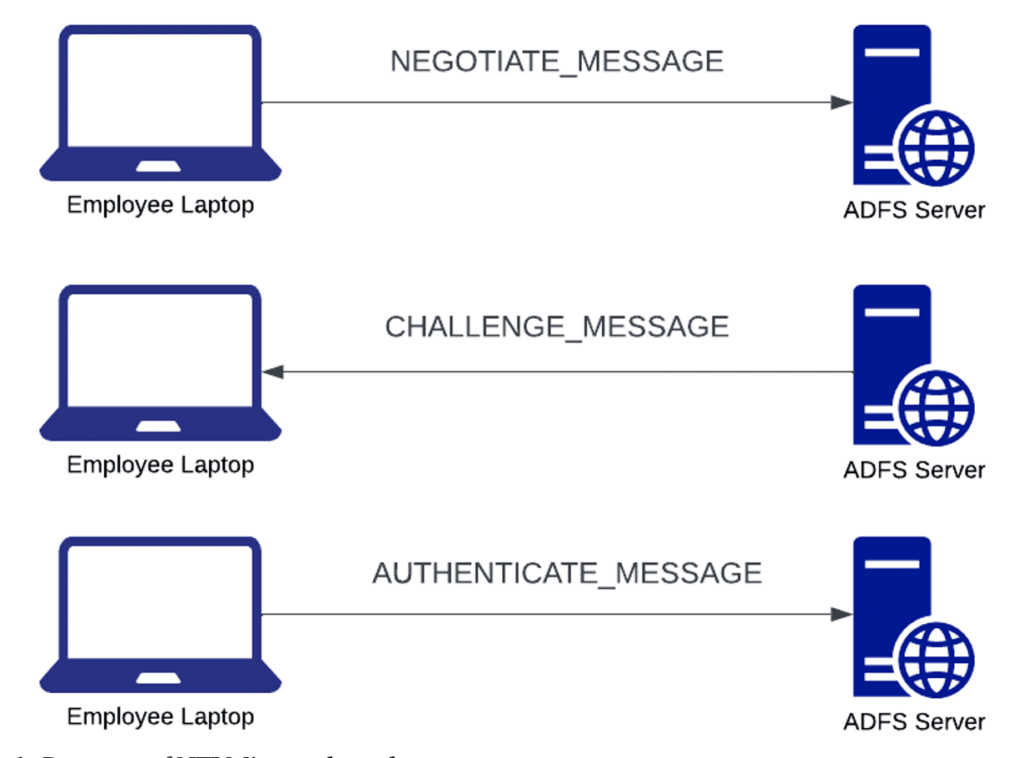
Overview During red team engagements over the last few years, I’ve been curious whether it would be possible to authenticate to cloud services such as Office365 via a relay from New Technology Lan Manager (NTLM) to Active Directory Federation Services (ADFS). If possible, this would unlock an entirely new attack surface for NTLM relaying attacks […]
Email Security (SPF, DKIM, and DMARC)

Introduction Our clients occasionally ask us to look into why a particular email that spoofed the client was not blocked by a mail server. Generally these emails are intended to impersonate a user at the company in question, and naturally our clients would want to ensure that the emails are rejected by a receiving mail […]
How to Implement Consistent Identity Management for Improved SaaS Security

Overview The number of SaaS products that businesses integrate into their workflows and processes continues to grow. BMC [1] reports 85% of small companies to have between 25-50 SaaS services in use. Larger organizations (greater than 250 employees) have more than 100 SaaS applications in place. The benefits of SaaS are undeniable: reduced time to […]
How to redirect traffic from an incoming TCP port using the Portbender utility

Overview In a previous article titled “Active Directory Computer Account SMB Relaying Attack,” we discussed how an attacker could leverage computers assigned administrative rights to other computers to escalate privileges or move laterally using the printer spooler service. Colloquially we often refer to this as a “Computer AdminTo Computer” vulnerability. Exploiting this issue in practice […]
How to Exploit Active Directory ACL Attack Paths Through LDAP Relaying Attacks

Overview This article describes methods by which an attacker can induce a victim user into authenticating using the NT Lan Manager (NTLM) Authentication Protocol to an attacker-controlled “Intranet” site, even in instances where that site points to an external internet-facing IP address. An attacker can then combine this primitive with LDAP relaying capabilities and the […]
CIS Controls Version 8 Overview: Bye-Bye “Top 20”

The Center for Internet Security (CIS) has just released Version 8 of their popular security controls. With this version, the “Top 20” moniker has been lost and the list of controls reduced to 18. The Version 8 is a major update to the Safeguards, builds on some of the new features in Version 7.1 (Implementation […]
NIST Cybersecurity Framework Vignettes: Backups

NIST Cybersecurity Framework Vignettes: Backups The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) Vignettes series focuses on findings from recent security assessments that highlight the importance of different NIST CSF objectives. The NIST CSF provides a comprehensive framework for complex organizations to close gaps and add layers to the “Swiss Cheese Model.” […]
The Elephant in the Room: Why Security Programs Fail

As a Principal with Praetorian, I’ve had the privilege of working with hundreds of clients, from fast growth startups to Fortune 500 giants. As we’ve performed red team exercises simulating an advanced persistent threat against our clients, I’ve seen that (much) more often than not we are able to compromise their “crown jewels.” In several […]
A simple and effective way to detect Broadcast Name Resolution Poisoning (BNRP)

A natural question that arises after an organization experiences a BNRP attack is “How can this be prevented?” The answer is simple on paper. To completely mitigate the risk, legacy Broadcast Name Resolution protocols should be disabled by policy. This is easier said than done, especially on large networks where the necessary data flows of […]