Implementing Application Whitelisting with Google Santa and Upvote (Part 2 of 2)

In part 2 of this series, we will provide technical guidance on how you can deploy Google Santa and Upvote in your organization.
Implementing Application Whitelisting with Google Santa and Upvote (Part 1 of 2)
In this post, we are going to take a real-life example of implementing application whitelisting inside of Praetorian and the challenges that were overcome.
Why Praetorian Benchmarks to MITRE ATT&CK™ and Why You Should Too

When it came to improving our Purple Team service line, which maps to “Detect” and “Respond” in the NIST CSF, we wanted to provide a similar high quality of data and metrics to our clients. In our experience, it is hard to drive change in any organization unless those changes can be tied to measurable results. After conducting a survey of known frameworks, we settled on the ATT&CK™ framework from MITRE.
Running a .NET Assembly in Memory with Meterpreter
In this blog post I will discuss leveraging Meterpreter’s powershell module to execute .NET assemblies in-memory. Metasploit and Meterpreter are effective and useful tools, but occasionally one encounters a situation where they lack features. Cobalt Strike (a different Command and Control framework) contains an execute-assembly command providing in-memory .NET execution for situations where it lacks built in commands. Meterpreter contains the features required to perform the same behavior, albeit slightly less polished.
Active Directory Visualization for Blue Teams and Threat Hunters
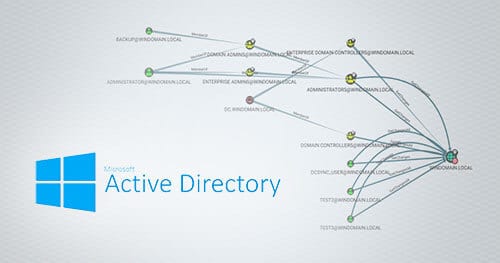
As a network defender, it can be easy to attribute a certain degree of omnipotence to attackers. Advanced threats have an uncanny knack for figuring out how to move through an environment without regards for passwords, roles, permissions, or what “should” be possible.
Benchmarking Enterprise Cybersecurity Programs with NIST CSF
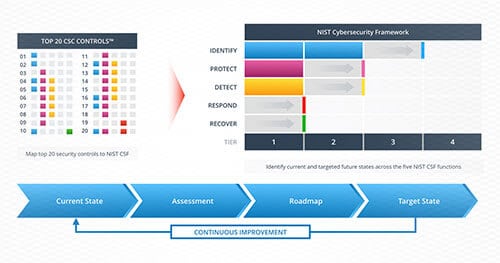
Benchmarking enterprise cybersecurity programs with NIST Cybersecurity Framework (CSF) helps organizations strengthen their security posture.
Summary of April MITRE ATT&CK RELEASE

MITRE’s Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK™) is a curated knowledge base and model for cyber adversary behavior, reflecting the various phases of an adversary’s lifecycle and the platforms they are known to target. ATT&CK is useful for understanding security risk against known adversary behavior, for planning security improvements, and verifying defenses work as expected.
KRACK (Key Installation Attack) Against Wi-Fi Networks
A flaw in the implementation of WPA2-based encryption allows for an attacker within physical range of the wireless network to decrypt traffic from a vulnerable client, allowing for viewing, intercepting, and modifying data in transit. This vulnerability has been assigned CVE numbers CVE-2017-13077 through CVE-2017-13088. There does not yet exist a working public exploit for this attack. However, the research group who discovered it have published their efforts, and working exploit code is likely a matter of days away.
Shadow Brokers After Action Report
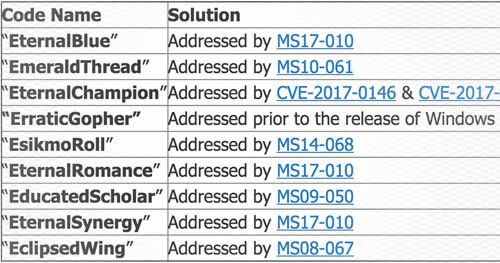
Microsoft released security updates in March that address many of the issues already. Therefore, there are no 0day vulnerabilities included in the toolset that can be used against fully patched versions of Windows. The toolset was built in 2013 which means it doesn’t include Windows 10 and 2016. Legacy versions of Windows are still vulnerable since Microsoft won’t release security updates for them.
Hashjacking: Anyone Can Steal Your Windows Password

There is currently an architectural vulnerability within the Windows SMB authentication protocol that affects modern Windows Operating System. The core of this issue is due to the presumptive nature of current SMB authentication methods. When a user accesses a file share or remote file (by typing “file://” or “” in a browser or file explorer) hashed Windows credentials from the current user are automatically sent to the remote server in attempt to authenticate and access the remote file. The default behavior of assuming the remote server is trusted allows for systems to quickly access file shares in large corporations so that users won’t need to sign in with their company credentials each time to access network resources. However, this implementation presents a significant security risk to user accounts and passwords.