How to Mitigate Mimikatz WDigest Cleartext Credential Theft
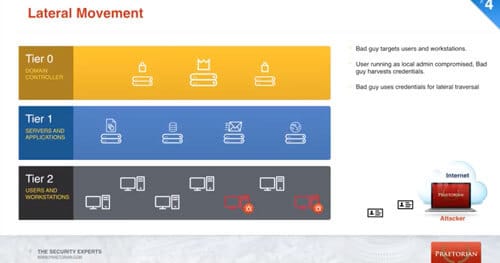
Penetration testers and malicious adversaries often focus on using the easiest attack vector to achieve their objectives. One common attack vector that has been around for several years is to use a tool called Mimikatz and steal cleartext credentials from memory of compromised Windows systems.
Broadcast Name Resolution Poisoning / WPAD Attack Vector
One of the common attack vectors for penetration testing is to leverage an attack known as Broadcast Name Resolution Poisoning. Recently, US-CERT posted an advisory about this attack being used externally. Attackers purchased new generic Top-Level Domains (gTLDS) and setup entries for the Web Proxy Auto-Discovery Protocol (WPAD). This is pretty interesting since it’s an old attack used in a new way. Let’s dive into how Broadcast Name Resolution Poisoning is used during internal penetration testing and go over recommendations for how to fully mitigate all forms of attack.
Email Filters: A Reliable Phishing Protection?
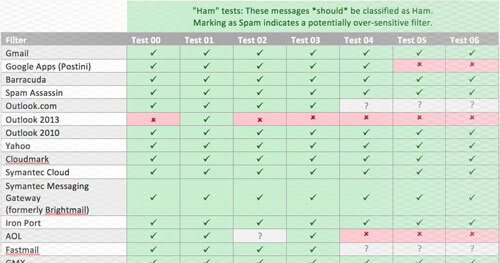
It’s no secret that spear phishing is a prevalent threat and is making an appearance in many CISOs' nightmares. The Verizon’s 2016 breach digest is out and—for anyone who hasn’t looked through it yet—the answer is 30%. That’s the percentage of breaches from 2013 to 2016 that leveraged social engineering tactics to stage a compromise. Of those attacks, phishing accounts for 72% of them. That means that nearly 22% of breaches in the last 3 years have leveraged phishing in some way or another. It's hard enough to secure external and internal assets… but having to secure your employees too? It’s a scary thought. Definitely something to keep one up at night. Current solutions include improving user awareness through training exercises, minimizing and controlling damage through defined incident response programs, and stopping phishing emails before they ever make it to employees' inboxes through email/spam filtering solutions. We're here to talk about the last one. Using a collection of benign and phishy emails alongside a spam filter testing service called Email on Acid, we've taken a stab at comparing 22 different spam filtering solutions. These tests measure each spam filter's ability to stop spear-phishing emails in their tracks. To anyone afraid of long articles, the “tl;dr” reads something like this: Spam filters are okay. They’re not perfect and not terribly intelligent, but they can be effective at times and represent one layer of defense that should be in-place to protect an organization from phishing or spear-phishing attacks.
Internetwache RE60 Writeup: Symbolic Execution Tramples CTF Challenge
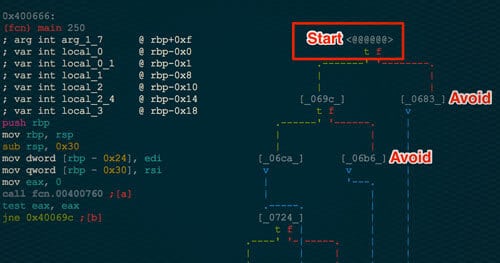
I am always looking for problems that symbolic execution could be applied to in the capture the flag space. This past weekend, this challenge was met during the Internetwache CTF for its RE60 problem. Below I describe the application of symbolic execution to solve the challenge without much knowledge of the inner workings of the binary itself. Symbolic Execution gives the reverse engineer the ability to find a specific path from Point A to Point B in a binary. This path is represented by a series of boolean expressions. These expressions can then be passed to a solver such as Z3 from Microsoft to solve the equation, creating an input that will exercise the found path.
Pentestly Framework: When Pentesting Meets Python and Powershell
Python appears to be an ever growing trend in the security community. Being able to connect Python tools together has proven beneficial for us. Powershell has also seen increasingly more use due to its wide availability in internal environments. Pentestly utilizes the power of these tools together in a familiar user experience.
Hob0Rules Released: Statistics Based Password Cracking Rules
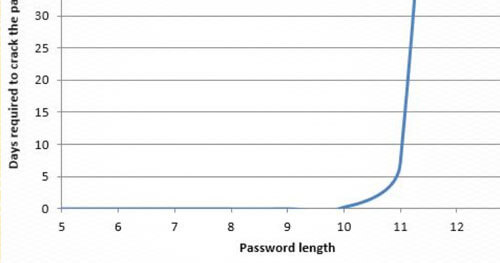
It’s now 2016 and people are still decisively using poor, predictable passwords. Employees around the world will soon be appeasing their mandatory 90-day password rotation by changing their password from ‘Winter2015’ to ‘Spring2016’. This happens in nearly every company – you would be surprised. Previously, I conducted password research to determine common traits of passwords, which was presented at various conferences. The password cracking rules that Praetorian utilizes for all hash cracking have now been released for Hashcat (described below) which are based on these findings. A quick compromise list of 64 of these rules have been released as hob064 and a more extensive ruleset has been released as d3adhob0 for public use. These rulesets were made to compete against their industry standard counterparts, Best64 and d3ad0ne. Both of the released rulesets have bypassed their counterpart in both time speed and number of hashes cracked and will continue to improve. The two sets of rules are living lists and change as the environment of passwords changes.
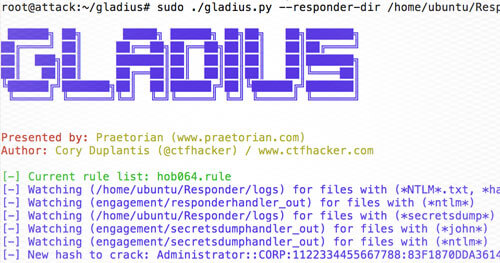
Gladius: Automatic Responder Cracking
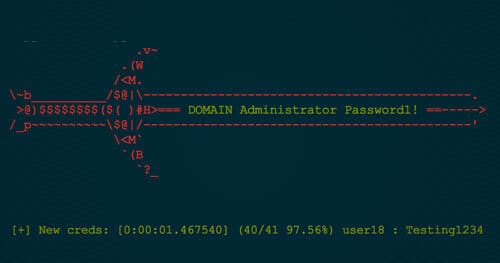
So there you are, performing your internal penetration test, using Responder to potentially grab hashed credentials and thinking "Responder is awesome… but manually cracking credentials isn’t fun." Well, welcome Gladius! Gladius happily listens for Responder hashes (and.. spoiler alert.. secretsdump.py and hashdump) and automatically passes them to hash cat. At its core, Gladius listens in target directories for file events and then performs computations based on the event. Let’s walk through the Responder workflow with Gladius.
IPv6 Has Arrived — Is Your Security Infrastructure Prepared?
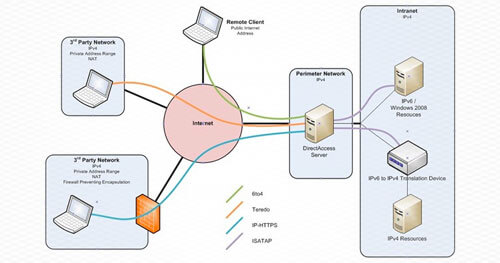
Just over 20 years ago, RFC 1883 – ‘Internet Protocol, Version 6 (IPv6) Specification’ – was published. Since then, exhaustion of the IPv4 address space, and a subsequent migration to IPv6 connectivity has been predicted, heralded, and warned against repeatedly. The seemingly endless stream of warnings and proddings over the past decade to “migrate or else…” have proved unfounded for most organizations. Understandably, this causes many organizations to dismiss or ignore recurring questions about IPv6 adoption, migration, and management plans.
Engineer Spotlight: Cory Duplantis and the 2015 SANS Holiday Hack Write-up

As an engineer, solving puzzles is part of everyday life. Any new challenge, whether it be learning a new exploitation technique or seeing a new embedded architecture for the first time, is simply another puzzle that I can learn how to solve in time. It is that mindset of always being curious and wanting to explore and apply new concepts that is utilized everyday at Praetorian. This mindset is also my default when approaching capture the flag (CTF) puzzles such as the CounterHack HolidayHack from this past year. As an internal penetration tester at Praetorian, I don’t usually dabble in the web spaces frequently, so the web challenges from the HolidayHack were a great opportunity to brush off the old web knowledge and maybe add a new web technique to the ever growing bag o’ tricks.
Group Policy Preferences (GPP) Pwned
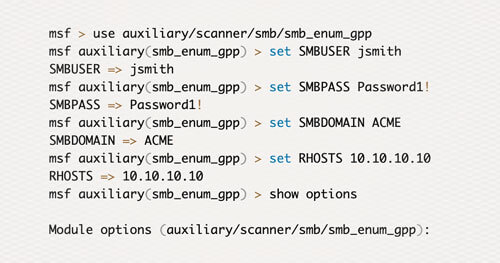
Over the past few months I’ve had a chance to clean up some code that we’ve used internally for penetration testing for some time now. This code was built to demonstrate the weaknesses of using Group Policy Preferences (GPP) to store and distribute local or domain credentials. We have found that many organizations store local admin, domain service, and even Domain Admin account credentials using GPP. The module that I submitted to the Metasploit Github repo provides the ability to enumerate GPP credentials as a domain user with access to the SMB share on the DC. Extracted credentials will be stored in the Metasploit creds tables.