Microsoft’s Local Administrator Password Solution (LAPS)
Hackers, incident responders, and penetration testers alike know that valid credential reuse is one of the most common real-world vulnerabilities in today’s networks. Valid credential reuse dominates as the top vulnerability in Verizon’s 2014/2015 Data Breach Investigations Reports Microsoft networks remain amongst the most vulnerable and exploited due to the way in which Active Directory is typically deployed: A base image is created with a standard local administrator password, which is duplicated on all workstations in the environment. When an attacker compromises any workstation, the local administrator password hash can be obtained and used to access every other workstation using the classic Active Directory exploit Pass-the-Hash (PtH). This methodology is described in detail in FireEye/Mandiant M-Trends 2015 case studies.
Statistics Will Crack Your Password
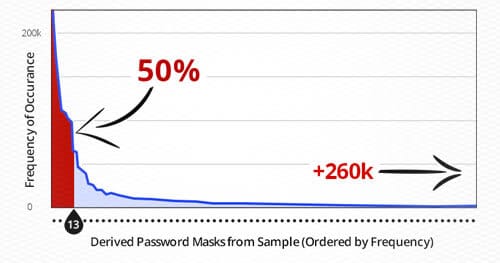
When hackers or penetration testers compromise a system and want access to clear text passwords from a database dump, they must first crack the password hashes that are stored. Many attackers approach this concept headfirst: They try any arbitrary password attack they feel like trying with little reasoning. This discussion will demonstrate some effective methodologies for password cracking and how statistical analysis of passwords can be used in conjunction with tools to create a time boxed approach to efficient and successful cracking.
NIST Cybersecurity Framework vs. NIST Special Publication 800-53
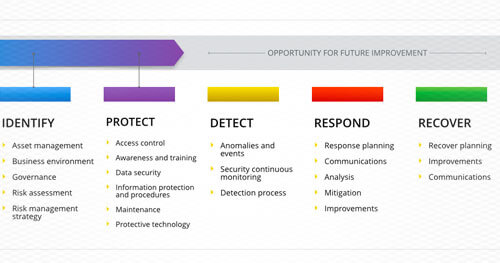
With the recent high-profile attacks on Sony and Anthem, it’s clear that cyber risks continue to grow and that organizations need to do more to strengthen their cybersecurity defenses. Security frameworks exist to guide the implementation and management of security controls, and they should be used by any organization looking to intelligently manage cyber risk. A security framework helps prevent a haphazard approach to information security, and reduces potential gaps in the organization’s security efforts. The ideal framework provides a complete guide to current information security best practices while leaving room for an organization to customize its implementation of controls to its unique needs and risk profile. Several existing and well-known cybersecurity frameworks include COBIT 5, ISO 27000, and NIST 800-53. Recently, a new framework has come into play: NIST’s “Framework for Improving Critical Infrastructure Cybersecurity.”
CRITICAL: Bash “Shellshock” Vulnerability
On September 24, 2014, a vulnerability in Bash—now referred to as the ‘Shellshock’ bug—was publicly announced after its discovery last week by Stephane Chazelas. Security experts expect the Shellshock bug to have significant and widespread impact, potentially more devastating than Heartbleed.
Building the HashCat API in Ruby to Crack Passwords in the Cloud
Have you ever had an amazing idea for automating two or more pieces of technology and then realized one of them doesn’t have an API? I came across this problem more than once during the development of a couple of projects here at Praetorian. In this post, I’ll share some of the libraries and techniques I have used to build out APIs for CLI programs, such as HashCat and nmap. Hopefully, these techniques and libraries will be helpful to you when building out new web applications and frameworks.
CRITICAL: New Internet Explorer Zero-day Vulnerability
Only a few weeks after Heartbleed hit the Internet by storm, reports of another serious zero-day vulnerability are starting to circulate within the security community. Over the weekend Microsoft released Security Advisory 2963983, which details a new remote code execution vulnerability impacting ALL versions of Internet Explorer (IE6-IE11). Microsoft is aware of “limited, targeted attacks that attempt to exploit the vulnerability.” The company is currently investigating public reports of the vulnerability and it has yet to publicize details to the reserved CVE-2014-1776, but there are steps organizations can take to protect against this threat.
NECCDC Red Team: Quick Twitter Command and Control (C2) Trojan

In the last few posts I covered a few C2 Trojans (DNS C2 Trojan, HTTP GET and POST Trojan). In this post I wanted to cover a method that uses Twitter for command and control.
NECCDC Red Team: Quick HTTP Command and Control (C2) Trojans
In my previous blog post, I described the Northeast Cyber Collegiate Defense Competition (NECCDC) and started to explain some of the techniques the red team used. For this post, I’m going to cover two more C2 Trojans that I wrote using HTTP (GET and POST). Similar to the C2 DNS Trojan, the HTTP Trojans are unidirectional and do not require installing software on the victim. By using multiple techniques at varying frequency we increased the likelihood we would be able to maintain persistence throughout the competition.
NECCDC Red Team: Quick DNS Command and Control (C2) Trojan

Recently, I had the opportunity to participate in the Northeast Cyber Collegiate Defense Competition (NECCDC) at the University of Maine. The competition was made up of 10 student groups (blue teams) from various colleges in the region that were tasked with protecting a mock network against a group of professional pentesters (the red team) who were trying to break in. This was my third year on the red team. Prior to the competition, I built several tools that would make life easier for the red team and enable us to differentiate between the qualities of the blue teams we were attacking. I am planning to release the code that I built for the competition over the next few months in a series of blog posts.
Advanced Threats: Driving Senior Leadership Awareness
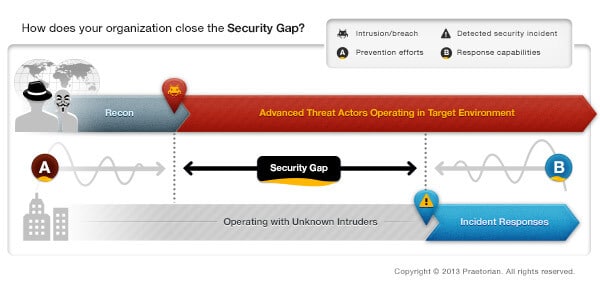
In today’s changing security environment, where advanced persistent threats (APT) are playing such a dramatic and notable role, it is the security organization’s responsibility to ensure that senior leadership understands and accepts risk associated with modern-day advanced threat actors. Regardless of your security maturity levels, you should at least be having the conversation about Advanced Threats. It is incumbent upon security leaders to drive this conversation within your organization in an effort to shift expectations away from thinking…