Hunting for Spring Core Exploitation
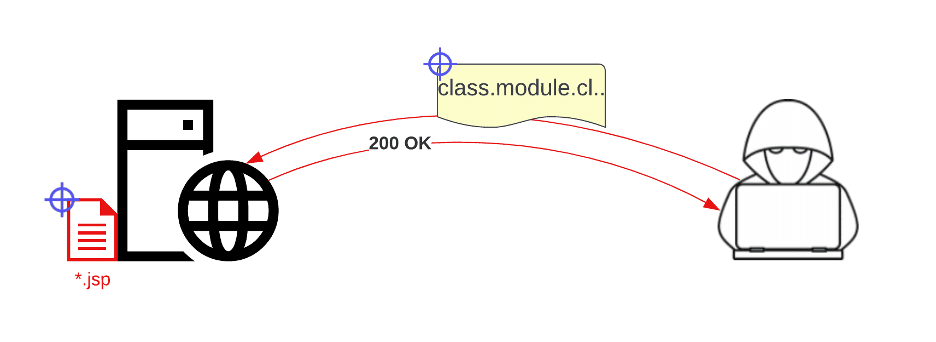
Background On March 30, 2022, Praetorian published remediation details for a remote code execution vulnerability for Spring Core on JDK9+ (CVE-2022-22965). A patch for vulnerable systems is now available and Praetorian has notified those affected through our Chariot offering. Hunting Opportunities Covering all our bases this early in the disclosure timeline can be a significant […]
The Click Heard Around the World

On April 19, 1775, the American Revolutionary War began at Middlesex County in the Province of Massachusetts Bay. While it’s actually hard to define a specific “first shot”, Ralph Waldo Emerson immortalized his view of the event in the “Concord Hymn” which begins with the following familiar stanza: By the rude bridge that arched the […]
How to Write and Execute Great Incident Response Playbooks

Introduction Security incidents of any magnitude are bound to happen within any organization, and they should be thoroughly investigated to prevent and protect critical data, resources and services. While it is hard to fully automate the investigation process, we can always introduce scripted plays for common occurrences we might come across – that is where […]
Incident Response Best Practices: Building an Evidence Wiki

What is an evidence wiki? As Blue Teams work to secure systems, it becomes especially important to keep track of interesting and helpful information gathered through the investigation process. During the investigation of a security incident, one of the very first things teams do is to create a timeline of events via checking various resources. […]
How to improve your Incident Response (IR) with Live Response

Live Response is the process of collecting data from compromised endpoints for an investigation while those assets remain active. Collecting Live Response data is critical to a successful incident response investigation. As Endpoint Detection and Response (EDR) and Antivirus (AV) have grown in capability, so too have attackers. To protect your environment and keep your […]
How to Prevent, Detect and Remediate ProxyLogon

Summary Our labs team’s ability to recreate a reliable end-to-end exploit underscores the severity of the ProxyLogon vulnerability. Compounding the criticality of this vulnerability, we’ve been able to use the ProxyLogon vulnerability in conjunction with a common Active Directory misconfiguration to achieve organization-wide compromise. The Active Directory and Exchange permission path issue up until now […]