Hardware Hacking a Nicotine Vape

Praetorian recently finished a tour de force at Hack Space Con, providing paid training, a workshop, and three talks: The entire Praetorian team had a blast at the conference, sharing our knowledge with the security community and making many new friends. HackVapeCon Before the conference started, four members of Praetorian’s Internet of Things (IoT) team […]
Breaking the Air Gap Through Hardware Implants

IoT security assessments expose diverse technologies, use cases, and protocols. While wireless components like WiFi and Bluetooth enhance functionality and enable features like OTA updates, they also increase the attack surface. This blog explores the challenges of assessing non-wireless IoT devices and considers the potential of adding wireless capabilities for comprehensive security testing.
Anatomy of an Automotive Security Assessment
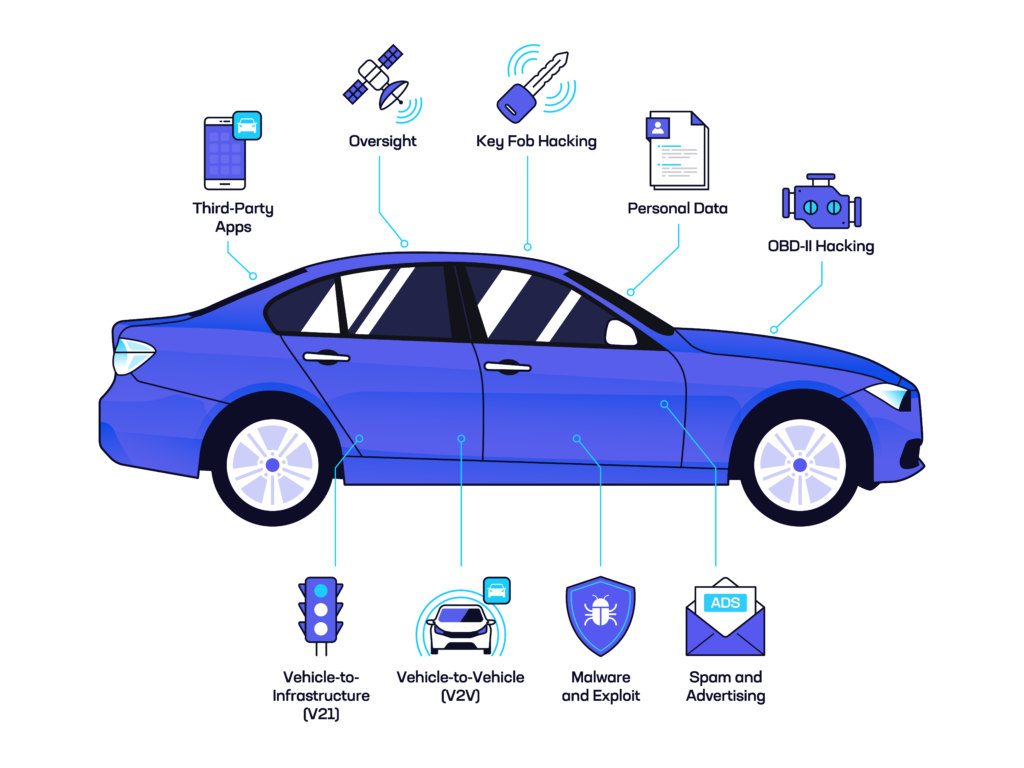
An Expanding Problem $1,000,000,000 One billion dollars. According to a 2015 Detroit Free Press article, that was the amount Fiat Chrysler Automotive might have to pay in buybacks and fines due to an automotive cybersecurity vulnerability. That year, Charlie Miller and Chris Valasek had published security research demonstrating the ability to remotely take over and […]
Multi-Step Attack Vectors: When Vulnerabilities Form an Attack Chain
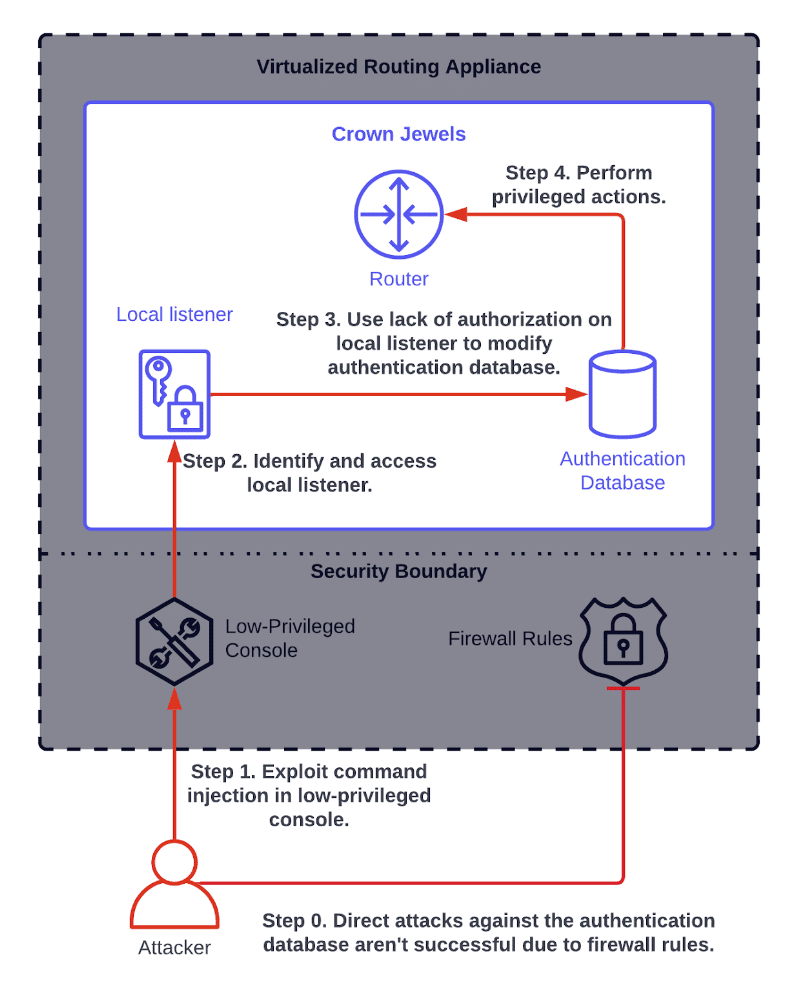
Praetorian’s approach to cybersecurity centers around a core belief that combining innovative technologies and the best people in the business leads to real results. In our experience, neither can fully solve cybersecurity challenges on its own. We therefore have designed our services organization and offerings to blend them seamlessly. We applied the same philosophy when […]
Inter-Chip Communication: Design Considerations to Mitigate Commonly Overlooked Attack Paths
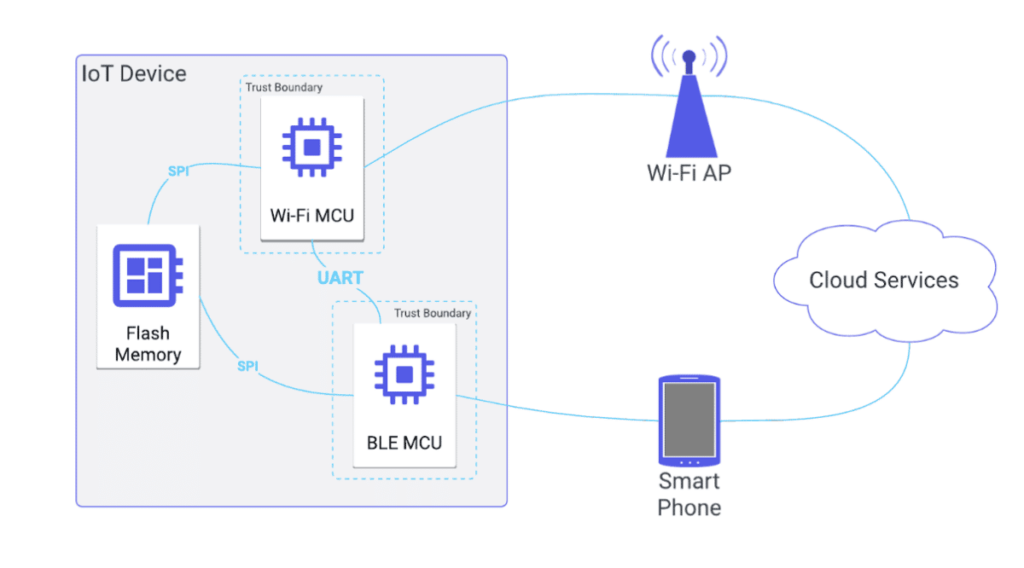
Introduction At Praetorian, we perform security assessments on a variety of Internet of Things (IoT) devices ranging from commodity home “smart” devices, medical devices, critical infrastructure, and autonomous vehicles. While previous blog posts have discussed a general methodology we’ve followed for a complete assessment, the nature of our “chip-to-cloud” security has led us to one […]
Methodology for Hacking IoT: From Chip to Cloud
Introduction Over the past 10 years, Praetorian has tested hundreds of embedded systems, ranging from autonomous vehicles, medical devices, critical infrastructure, and smart consumer devices. Through our collective experience, Praetorian developed techniques and methodologies for testing a large range of IoT systems. In this article, we will go through our methodology to hacking IoT systems, […]
How to Create a Secure Authentication Scheme for IoT Systems

This article discusses some of the common authentication pitfalls that Praetorian has observed in IoT devices and address ways to fix these problems.
Safely Conduct Security Assessments of Industrial Control System (ICS) Environments

Our current standard of living is made possible due to the massive scale of critical infrastructure that supports our needs as a society. Electricity, Oil, Gas, Water, and Security are a few of the well-known industries whose infrastructure is managed by Industrial Control Systems (ICS). Few systems have the potential for catastrophic consequences from a security incident as is possible with an ICS breach.
Reversing and Exploiting Embedded Devices: The Software Stack (Part 1)
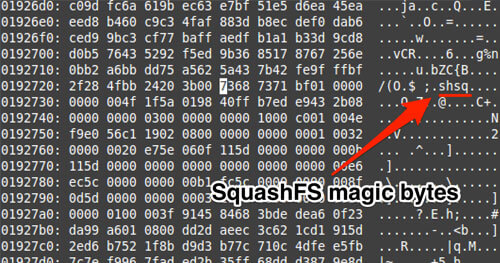
Over the course of the past few months I’ve been traveling around educating people on exploiting embedded devices. My slides alone aren’t able to provide enough information, so I wanted to write everything out for people to digest online. The following blog post is “Part 1”, which will introduce the reader to the software side of embedded devices. I decided to cover software first since most flaws reside within the software stack, ranging from binary applications to drivers. Part 2 will cover the Hardware stack with a focus on educating the reader on how JTAG actually works and how to leverage Hardware modifications to either bypass password protections or to extract secrets that may be baked into the targeted devices.
JTAGulator vs. JTAGenum, Tools for Identifying JTAG Pins in IoT Devices
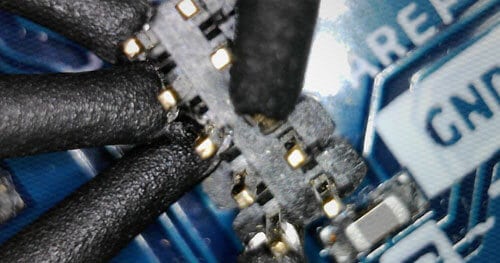
Do you suspect some pins on your device are JTAG? There are several methods out there for identifying if pins are likely to be JTAG or not. One of those methods involves buying a $200 JTAGulator, however there is a cheaper Arduino-based alternative I will be detailing in this post. First I’ll explore the expensive way.