Red Team Local Privilege Escalation – Writable SYSTEM Path Privilege Escalation – Part 1

Overview In this two-part series we discuss two Windows local privilege escalation vulnerabilities that we commonly identify during red team operations. These issues are of particular interest due to their prevalence within organizations with mature security programs. Furthermore, exploitation of the issue is unlikely to trigger a detection within commonly used endpoint and network monitoring […]
Building a Domain Specific Language for Red Team Payload Generation

This article shares how Praetorian developed a customer YAML-based domain-specific language (DSL) to specify red team dropper behavior.
Inside the Mimikatz Pass-the-Hash Command (Part 2)

Second in a two-part series providing an overview of how the Mimikatz pass-the-hash command works.
Inside the Mimikatz Pass-the-Hash Command (Part 1)

First in a two-part series providing an overview of how the Mimikatz pass-the-hash command works.
Red Team Infrastructure Tooling: Command Line Utilities and U2F
This article shares observations and best practices for red team infrastructure tooling, with a focus on command-line applications to manage server infrastructure.
Praetorian’s Approach to Red Team Infrastructure
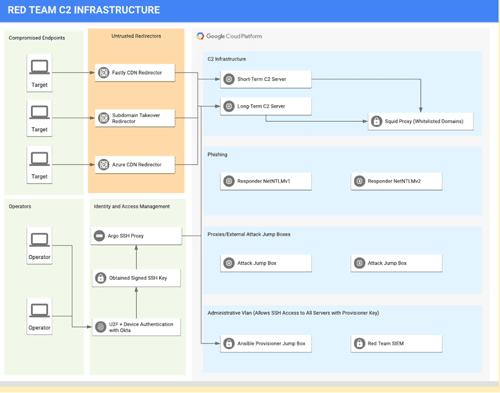
Praetorian provides a best practices approach to Red Team Infrastructure using a Google BeyondCorp architecture
Obtaining LAPS Passwords Through LDAP Relaying Attacks

Commentary on Praetorian’s recent contribution of additional functionality to the Impacket ntlmrelayx utility.
Getting Started with Praetorian’s ATT&CK Automation
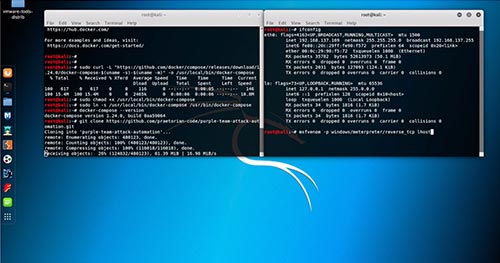
Earlier this month, Praetorian released its automation for emulating adversary tactics, techniques, and procedures (TTPs) based on the MITRE ATT&CK framework. We’ve gotten a number of requests from users asking for more detailed instructions on how to get started with the tool. This blog post accompanies the recently released video tutorial.
Process Injection and Process Hollowing (ATT&CK T1055 & T1093)
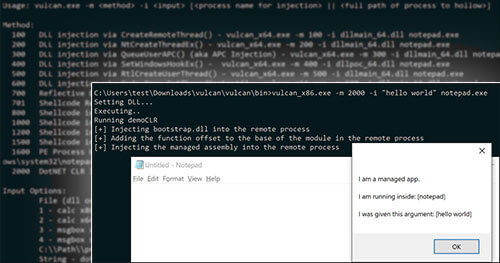
We are releasing Vulcan, a tool to make it easy and fast to test various forms of injection. All of the techniques included are already public. Vulcan brings them together in a single tool to test endpoint detection and response (EDR) coverage so that you can quickly identify detection gaps. This tool can be used as a test-harness to identify gaps so that efforts can be focused on detecting holes.
Red Team Supply Chain Attacks in Modern Software Development Environments
The future of red teaming not only requires updated adversarial tradecraft – although that’s a big part of it – but also a shift in buyer mindset to scope realistic scenarios that continue to test and challenge their defences.