Red Team Supply Chain Attacks in Modern Software Development Environments
The future of red teaming not only requires updated adversarial tradecraft – although that’s a big part of it – but also a shift in buyer mindset to scope realistic scenarios that continue to test and challenge their defences.
ICMP C2 Standard Non-Application Layer Protocol (ATT&CK T1095)
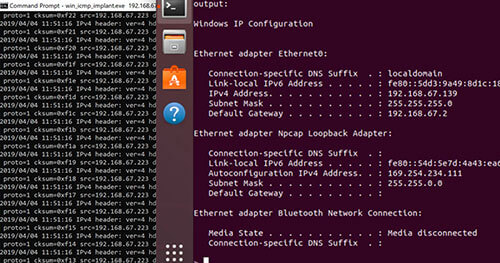
While ICMP may not be the answer for exfiltration, it can be very useful as a long-term C2 alternative channel. If all other communications channels didn’t work or failed or if persistence / access was terminated, we could always maintain a stealthy ICMP backup channel, which we could use to respawn primary C2 channel.
Using Slack Web Services as a C2 Channel (ATT&CK T1102)

Our proof of concept (PoC) blends in with normal business activities such as user-to-user or user-to-group communications. Detecting this type of activity requires sophisticated network analysis capabilities, such as the ability to intercept and decrypt SSL messages. Future versions may add additional encryption on top of SSL. In our PoC, we also configure a random sleep between 1m and 5m to further obfuscate our activity. These sleep times can help our C2 fly under the radar, but will also impact the ability of the attack operator to execute rapidly depending on how aggressively the timeouts are configured.
Signed Binaries Proxy Execution – T1218
The MITRE ATTACK April release included is a new TTP known as ‘Signed Binaries Proxy Execution’ which is T1218. This TTP is based on an attacker using signed binaries to perform malicious activities.
Signed Scripts Proxy Execution – T1216
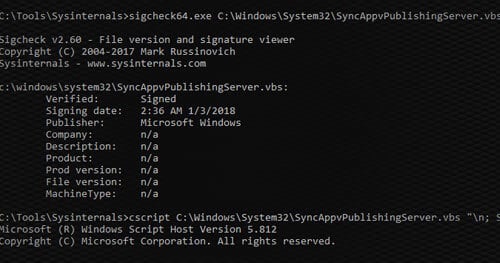
Many organizations trust all signed code from Microsoft. Unfortunately, there are many ways in which attackers can use this trust against them. Previously, we covered using signed binaries to perform malicious activities. In this post, we will be covering how to use signed scripts.
How to use Kerberoasting – T1208 for Privilege Escalation
In our experience, Kerberoasting is an attack that is similar to others in that defenders need to fully under it to be able to properly migrate the risks. It’s our goal that through pushing this content into the MITRE ATT&CK framework we have increased the awareness of this TTP so that organizations can be better protected in the future.
PHP-CGI Remote Command Execution Vulnerability Exploitation

During a recent penetration test, our team found a few web servers that were vulnerable to a PHP-CGI query string parameter vulnerability (CVE-2012-1823). This vulnerability allows an attacker to execute commands without authentication, under the privileges of the web server. The target environment had very strong egress controls in place. All outbound ports were blocked and only ports 80 and 443 were allowed inbound. This made it difficult to obtain an interactive shell. Therefore, we decided to build a proof of concept exploit script using cURL to execute commands and then take it to the next level by authoring a new Metasploit Module.