Dynamic Linking Injection and LOLBAS Fun
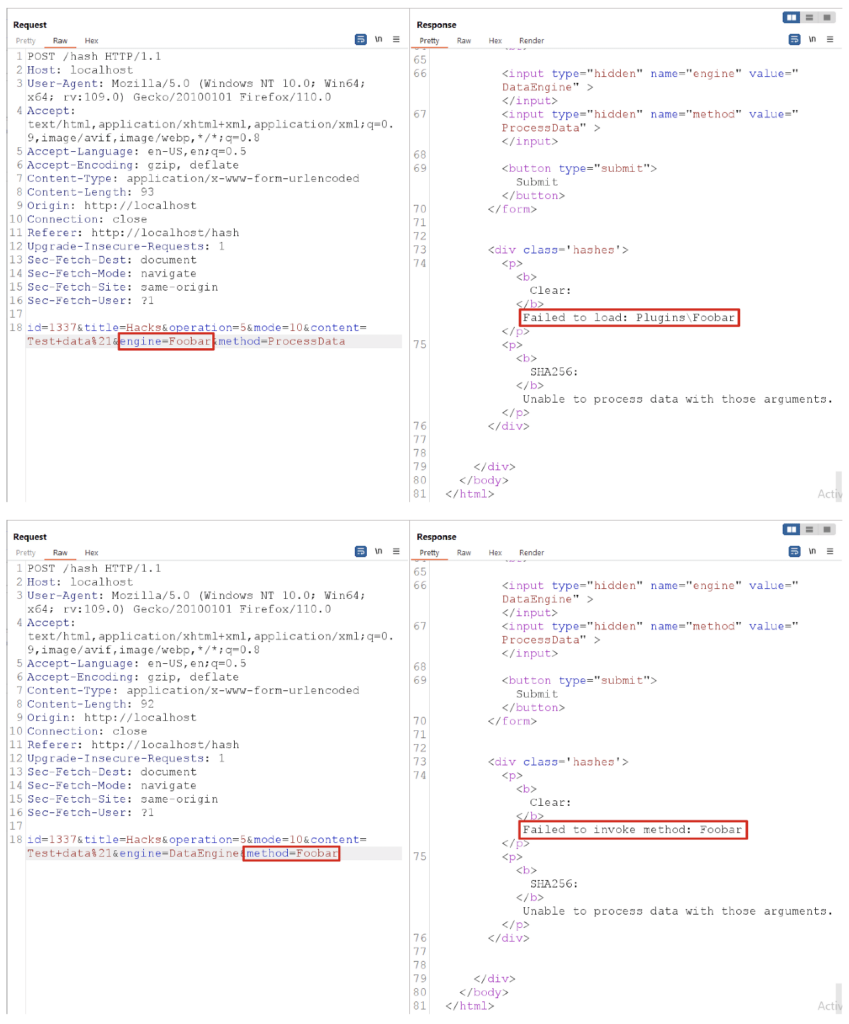
Introduction LoadLibrary and LoadLibraryEx are how Windows applications load shared libraries at runtime. Praetorian recently tested a .NET web application that unsafely passed user input into LoadLibrary. In this article, we discuss this vulnerability class, dubbed dynamic-linking injection. We begin with an explanation of the vulnerability. We then walk through a simple recreation of the […]
Web3 Trust Dependencies: A Closer Look at Development Frameworks & Tools
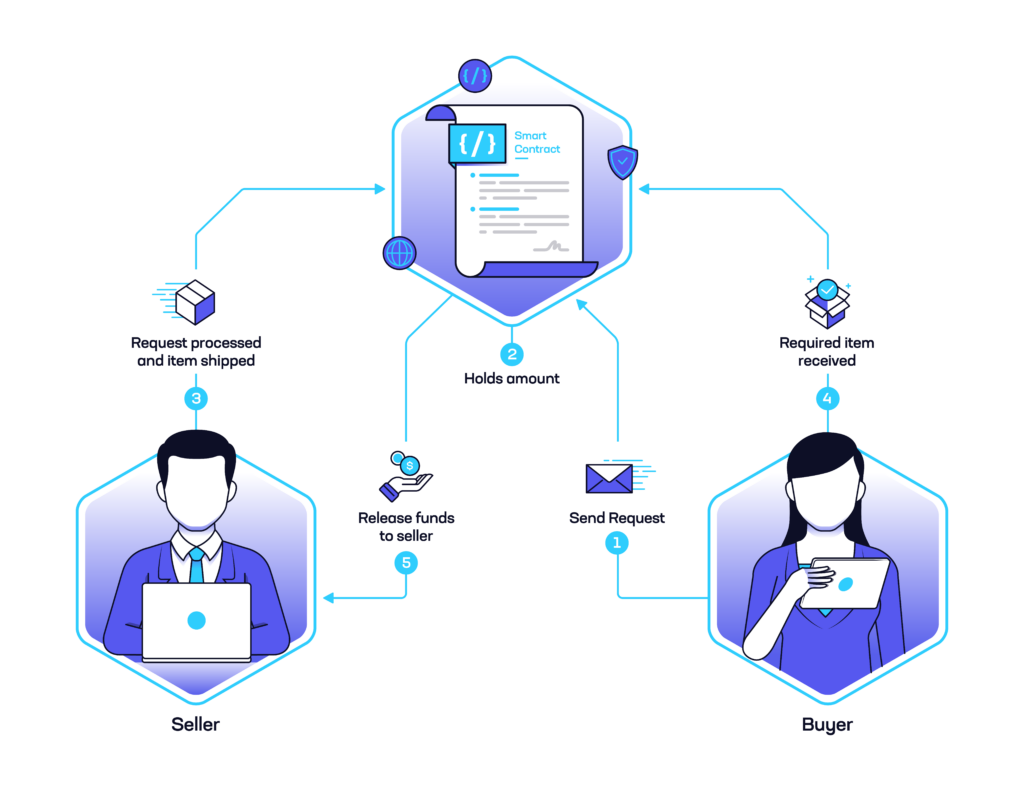
In the world of headline-grabbing smart contract exploits, developers and other stakeholders often skew their security attention in one direction; namely, they tend to focus on on-chain code, yet often neglect framework security. When writing smart contracts, this oversight can have significant negative security implications. Insecure frameworks or languages can subtly introduce vulnerabilities when compiling […]
Instrumenting an Automotive Module for Bench Testing
Finding vulnerabilities, hacks, exploits, and full root access are goals for security engineers when they begin to assess a device, right? But when working with hardware, you cannot simply dive into the hacking on day one. Your exploits will only be as successful as the setup work you’ve done! This post will discuss the process […]
Assessment of an Ecosystem: The importance of end to end, holistic testing
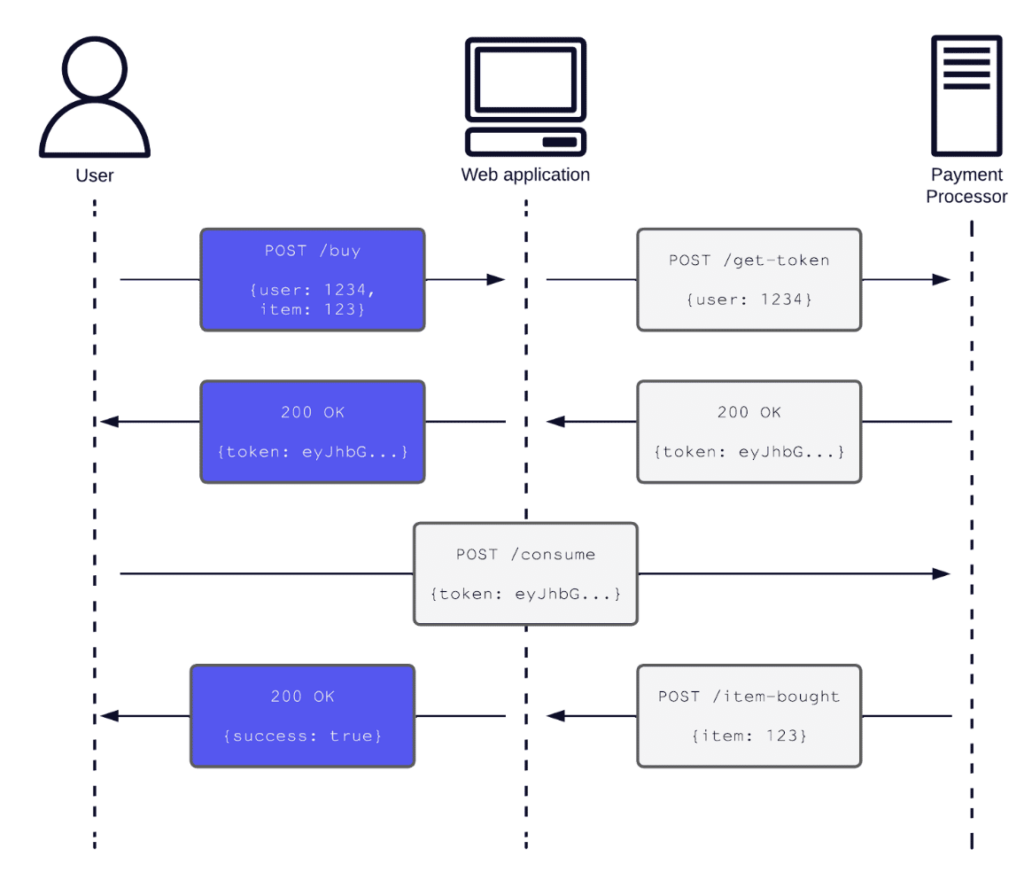
Expanded interaction between cloud-hosted and on-premise components has contributed to the increased complexity of companies’ tech stacks. As this and other cyber technologies evolve, so do the associated cybersecurity concerns. Traditional penetration testing, focused on a single component like a web application, has difficulty aligning to this new dynamic. If an identified vulnerability lies between […]
Safeguarding Memory in Higher-Level Programming Languages
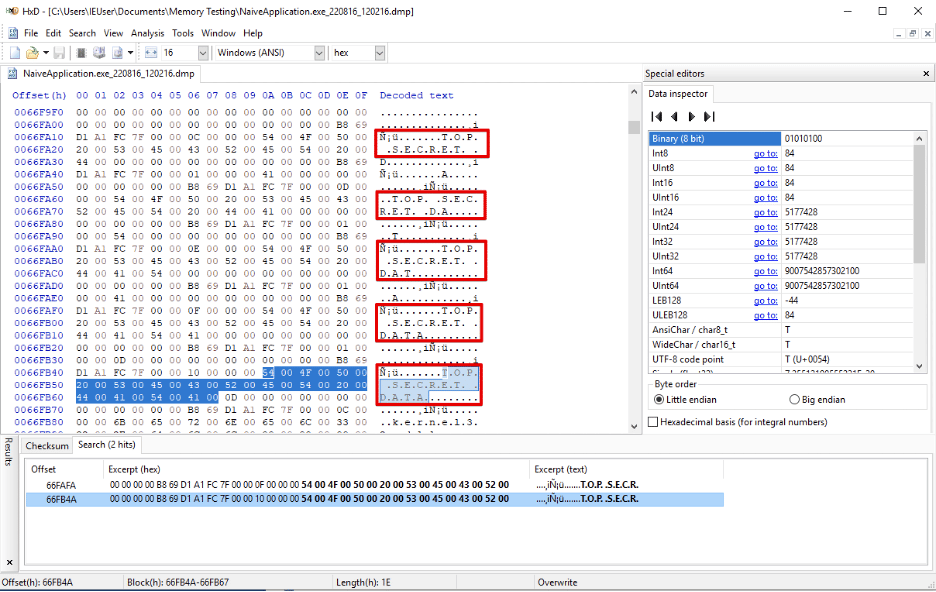
Consider an application written in a higher-level language like Python, NodeJS, or C#. This application must handle sensitive data such as banking credentials, credit card data, health information, or network passwords. The application developers have already hardened the application against malicious users and are confident that it is not vulnerable to database injections, account takeovers, […]
Whitebox Security Assessments: Doing More with More
When deciding on what type of security assessment to get, an organization should consider how much information they are willing to share. Several types of assessments exist, and the key differentiator is how much access an organization grants the testers from the beginning. The terms blackbox, greybox, and whitebox refer to whether a client chooses […]