Attack Path Mapping
Navigate the complexities of your network’s security with precision, ensuring every potential vulnerability is not just identified but effectively neutralized.

Gain insight into your digital environment
Identify security gaps allowing you to focus your defenses and enhance your security posture against advanced cyber threats.
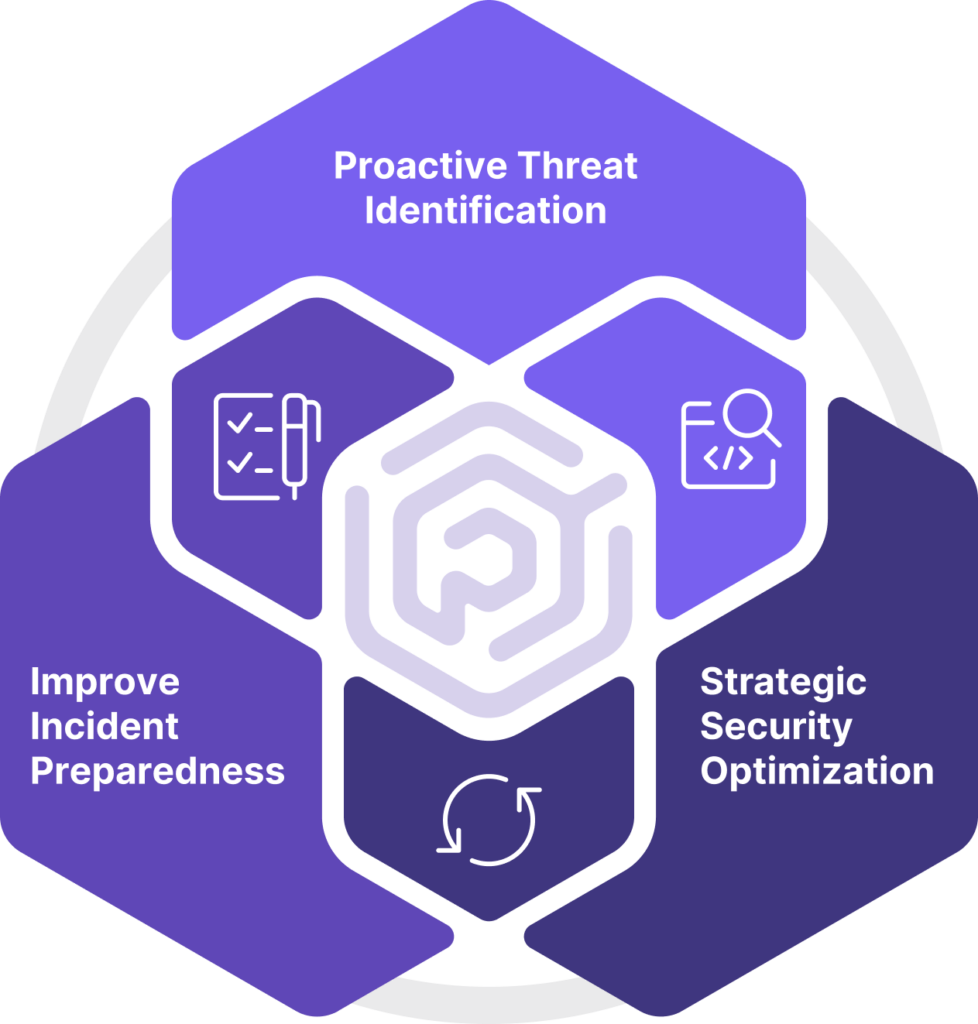
Proactive Threat Identification
Test and evaluate the effectiveness of your security controls through the simulation of attack chain components. Incorporate MITRE ATT&CK Framework TTPs through atomic testing of preventive and detection controls.
Strategic Security Optimization
By identifying vulnerabilities along attack paths, our service helps organizations strategically allocate security resources to address the most critical risks first.
Improve Incident Preparedness
By understanding potential attack vectors, organizations can develop incident response strategies, reducing the time to detect and respond to cyber incidents, thereby minimizing potential damage.
Comprehensive Attack Path Visualization
Our expert security engineers create a detailed visual representation of potential attack paths, highlighting critical vulnerabilities and their relationships.
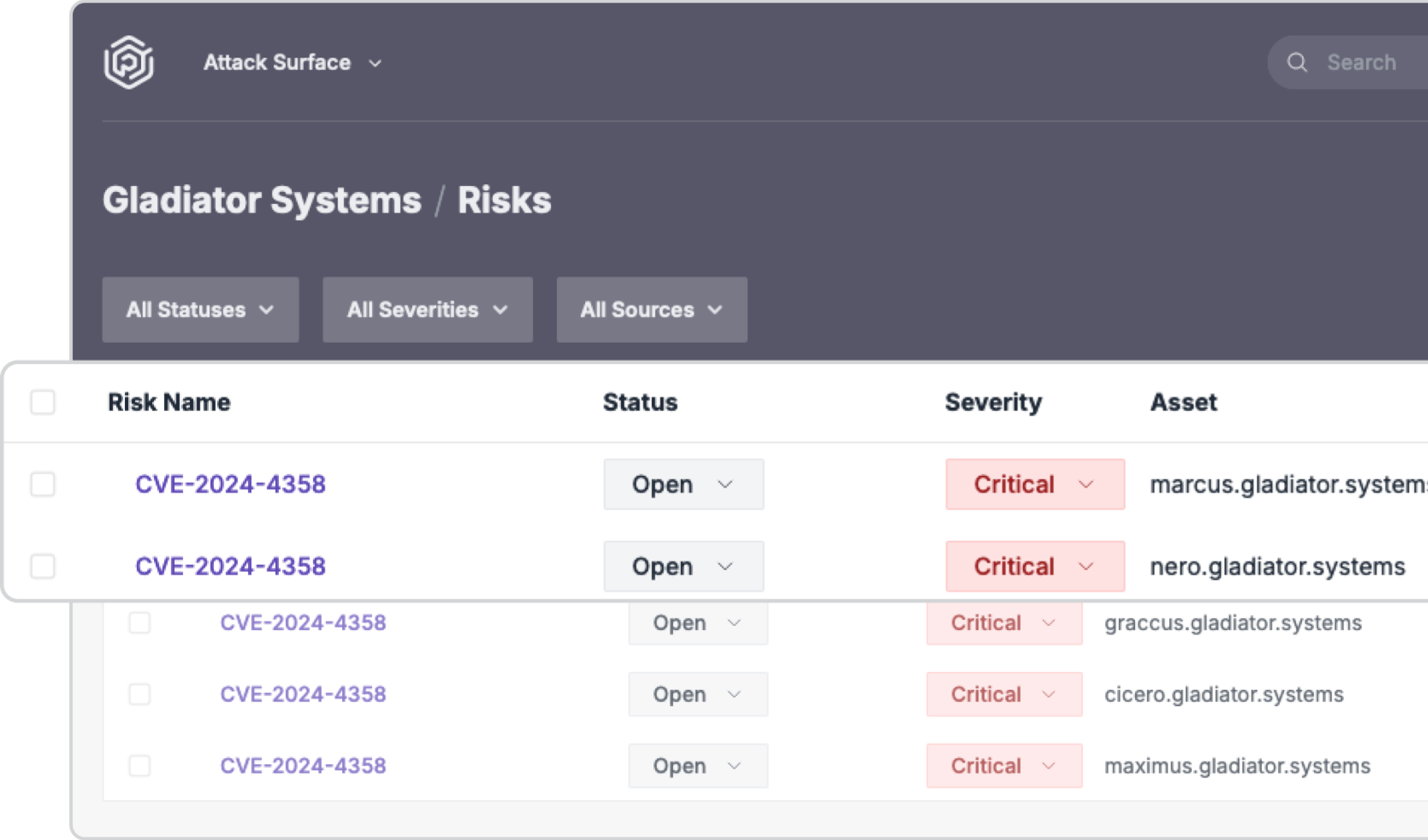
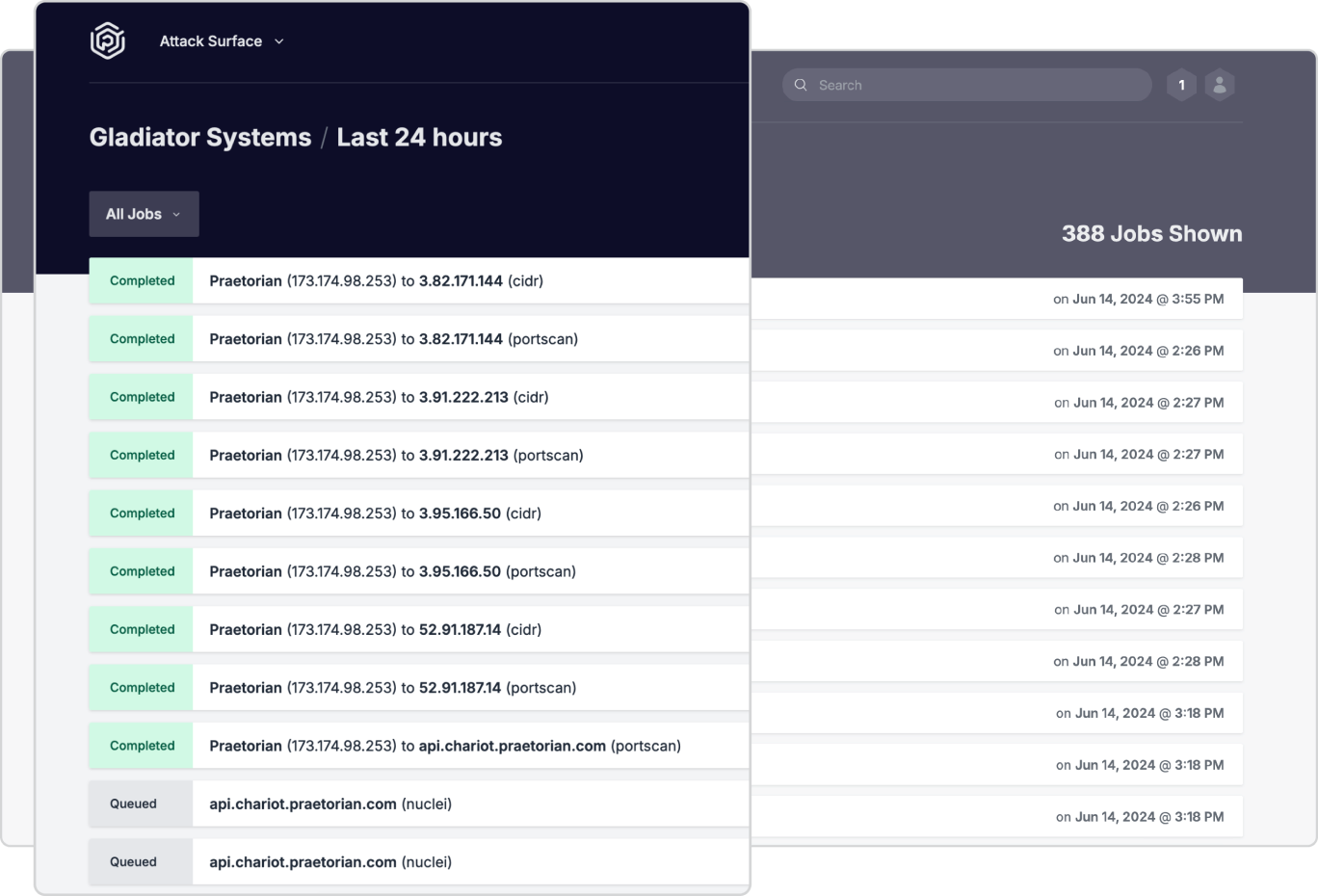
Automated and Manual Analysis Techniques
Combining automated tools with expert manual analysis, we ensure a thorough examination of your network’s security, from software configuration to user behavior and privileges.
Real-World Attack Simulations
Customized Security Roadmap
Risk-Informed Approach
Gain insights into the most critical vulnerabilities within your network, allowing for prioritized and effective risk management strategies to fortify your defenses against targeted attacks.
Cost- Effective Security Planning
Maximize your security investments by understanding and prioritizing critical vulnerabilities to ensure cost-effective planning and resource allocation.
Improved Security Architecture
Enhance your security architecture by utilizing insights from attack path mapping to redesign or reconfigure it, strengthening your defense against cyber threats.
Enhanced Compliance and Third-Party Risk Management
Our service helps organizations meet regulatory compliance requirements and manage third-party risks by providing a comprehensive view of potential attack paths that could compromise sensitive data.
Ready to Discuss Your Attack Path Mapping Initiative?
Praetorian’s Offense Security Experts are Ready to Answer Your Questions