Attack Surface Management
Gain complete visibility into your constantly expanding attack surface through continuous discovery, identification, and monitoring of your ever evolving digital landscape.
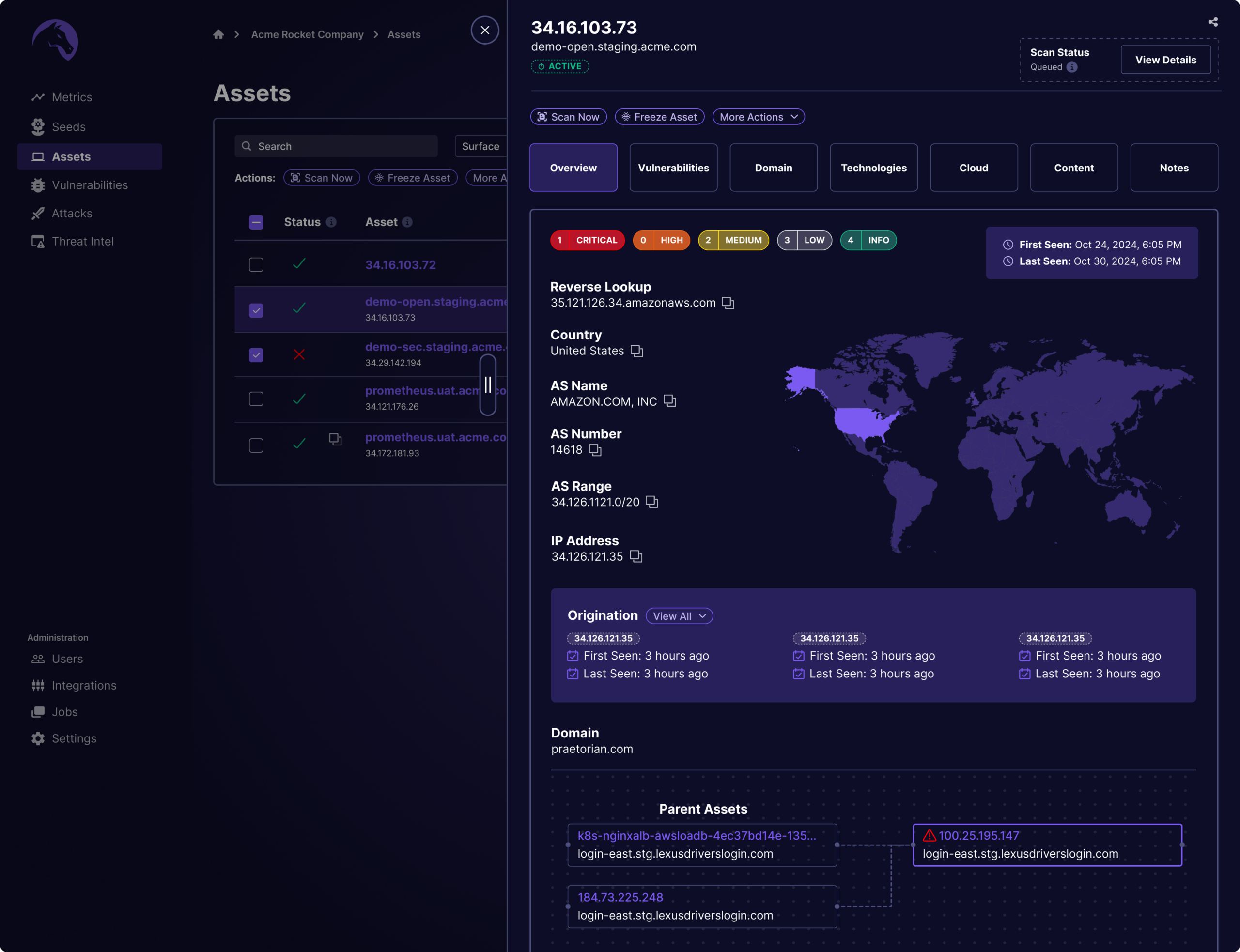
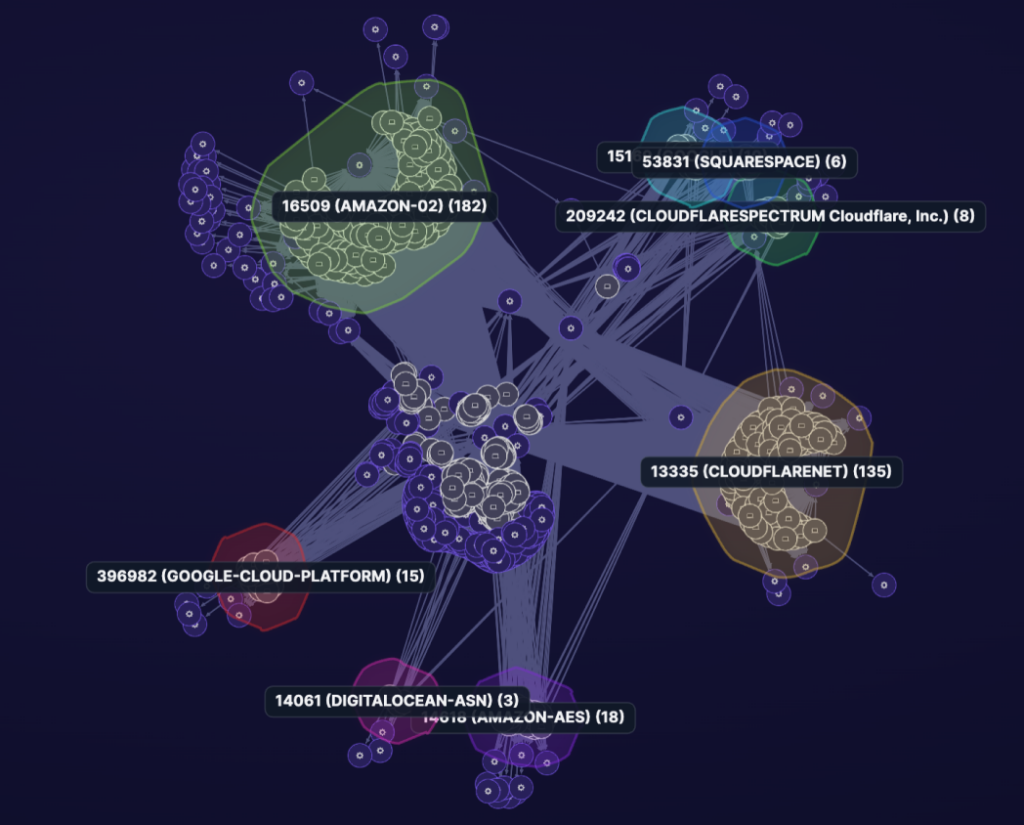
Uncover the Hidden Risks Within Your Attack Surface
You can’t protect what you can’t see. By mapping your digital assets, you gain valuable insights into your infrastructure, applications, and connected devices. This comprehensive view empowers you to understand the various entry points attackers may exploit and take proactive measures to minimize risks.
Manage Your Attack Surface from the Hackers’ Perspective
Discover Shadow IT and Reduce Technology Sprawl
Proactively defend your attack surface and discover weaknesses within your environment; assets both known and unknown
Close the Attackers’ Window of Opportunity
Find the weakness before attackers do and quickly close the attack window through white-glove remediation guidance from a dedicated Praetorian security engineer.
Gain Full Technology Coverage
Praetorian’s Chariot platform offers the most holistic attack surface coverage on the market, accounting for all internal, external, cloud, web apps, secrets, phishing, and third- party attack vectors.
Address Material Risk, Not Superficial Detections
By combining continuous automation with human driven context and triage, internal IT teams can focus their efforts on the strategic initiatives that matter most
Industry Leading Technology Platform
Praetorians’ continuous offensive security platform, Chariot, enables organization to proactively defend their attack surface through continuous discovery and identification of exposures, eliminating risk before it is exposed.
Ready to Begin Your Attack
Surface Management Initiative?
Praetorian’s Offense Security Experts are Ready to Answer Your Questions