Adversarial Exposure Validation
Proactively test your defenses against simulated real-world attacks
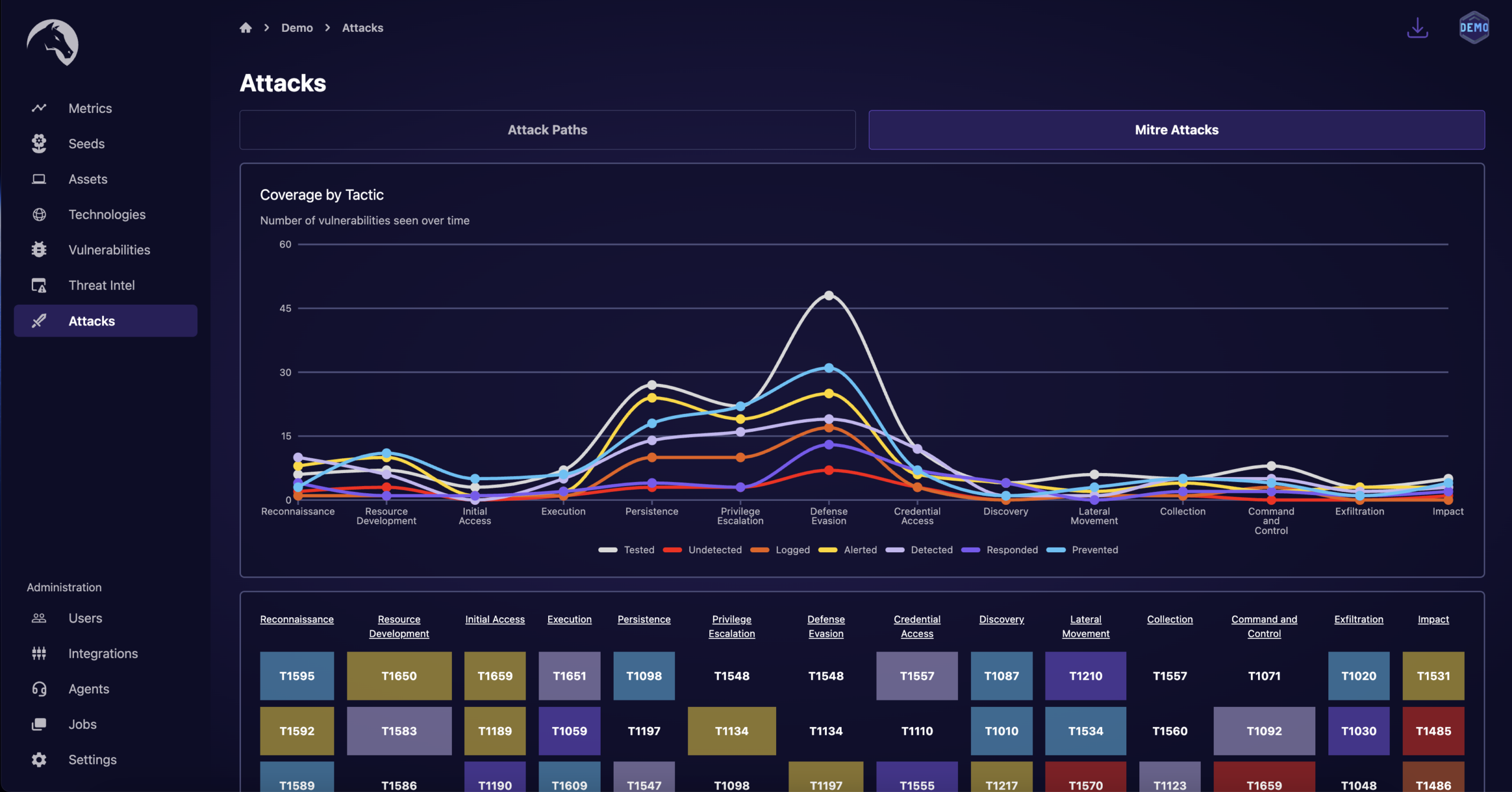
Anticipate the Attackers Next Move
Provide your organization with the necessary resources and knowledge to proactively anticipate, identify, and respond to real-world cyber threats. Through the simulation of sophisticated attack techniques and hacker tradecraft, including but not limited to lateral movements, elevation of privileges, and unauthorized data transfers, we present an authentic and objective evaluation of your security readiness.
Comprehensive Threat Emulation
Praetorian’s team of ethical hackers use the latest threat intelligence and hacker tradecraft to simulate advanced persistent threats, insider threats, and other sophisticated attack vectors putting an organization’s defenses to the ultimate test.
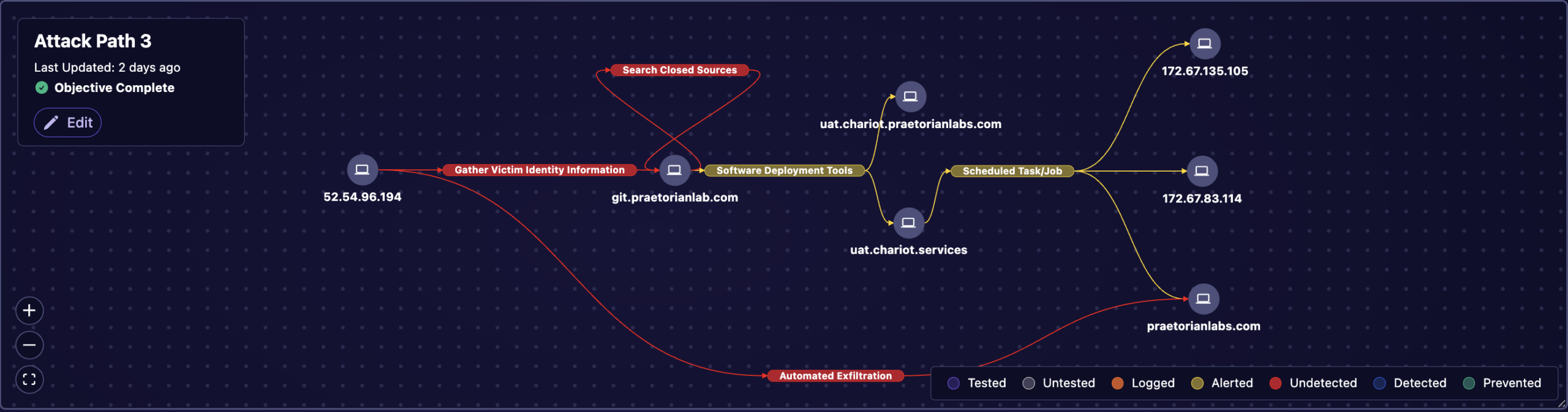
Build the Most Robust Security Playbook
Customized Scenarios
We realize every organization has unique needs, regulatory requirements, and operational motions. This is why our team of security experts creatively design and execute customized breach and attack simulation scenarios that align with your organization’s unique needs and objectives.
Advanced Threat Intelligence
Leverage the latest threat intelligence and hacker tradecraft provided by advanced research of the Praetorian Labs team to strengthen your cyber resilience. By uncovering potential attack paths and patterns that could be exploited by real-world adversaries you stay one step ahead in anticipating the attacker’s next move.
Actionable Reporting and Insights
Receive a suite of detailed reports including an executive summary, technical remediation guidance, and a business impact analysis. Each report aids in speaking to the diverse needs of each stakeholder.
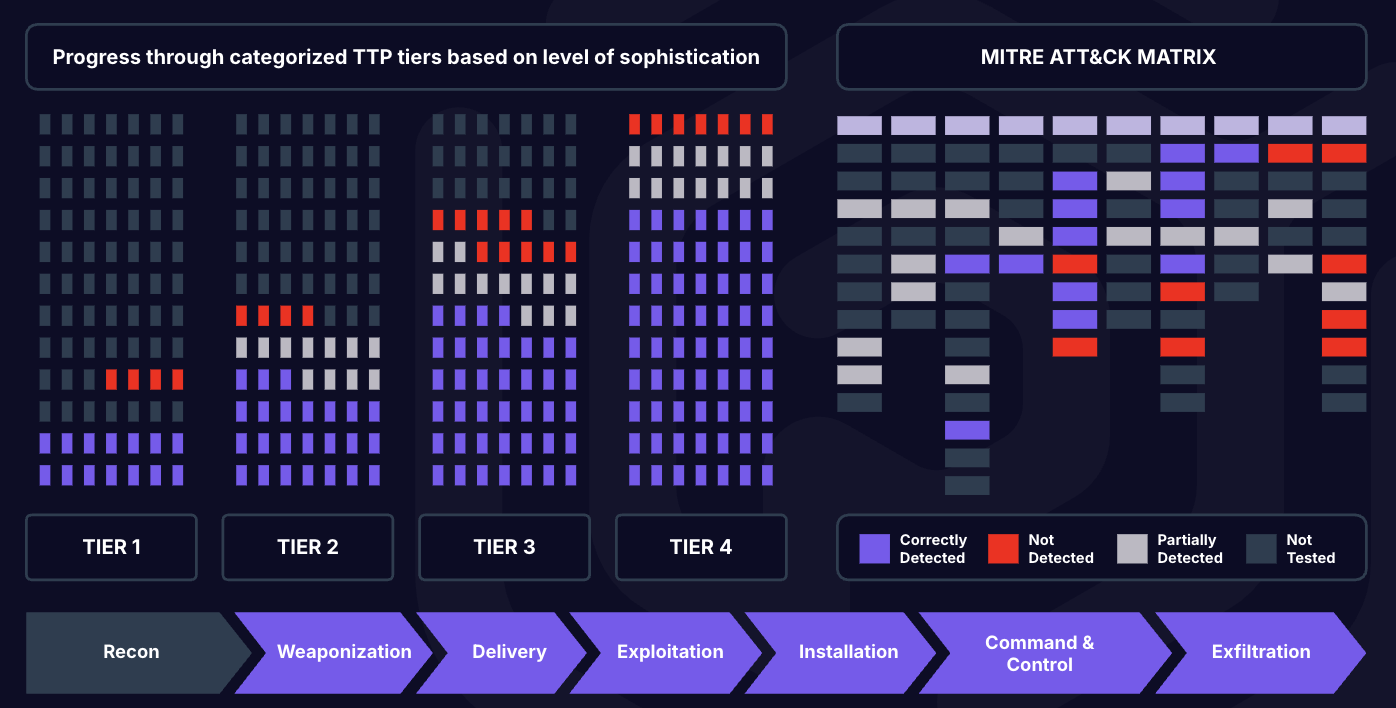
Identify Security Gaps in Your Prevention and Detection Plans
Enhance Cyber Resilience
Understand and prepare for the latest TTPs used by even the most sophisticated attackers. Gain the insight needed to prevent, detect, and respond to cyber incidents while measuring against frameworks such as NIST and CIS Controls.
Continuous Improvements
Breach and Attack Simulation is designed to be a continuous managed process that leverage both automation and human-driven intelligence. Regular testing of security controls allow for iterative adjustments and continuous improvement to your security posture.
Maturity Roadmap
Accelerate the development of your security program by building a clear roadmap for improvement while aligning to your organizations priorities.
Ready to Discuss Your Breach and Attack Simulation Initiative?
Praetorian’s Offense Security Experts are Ready to Answer Your Questions