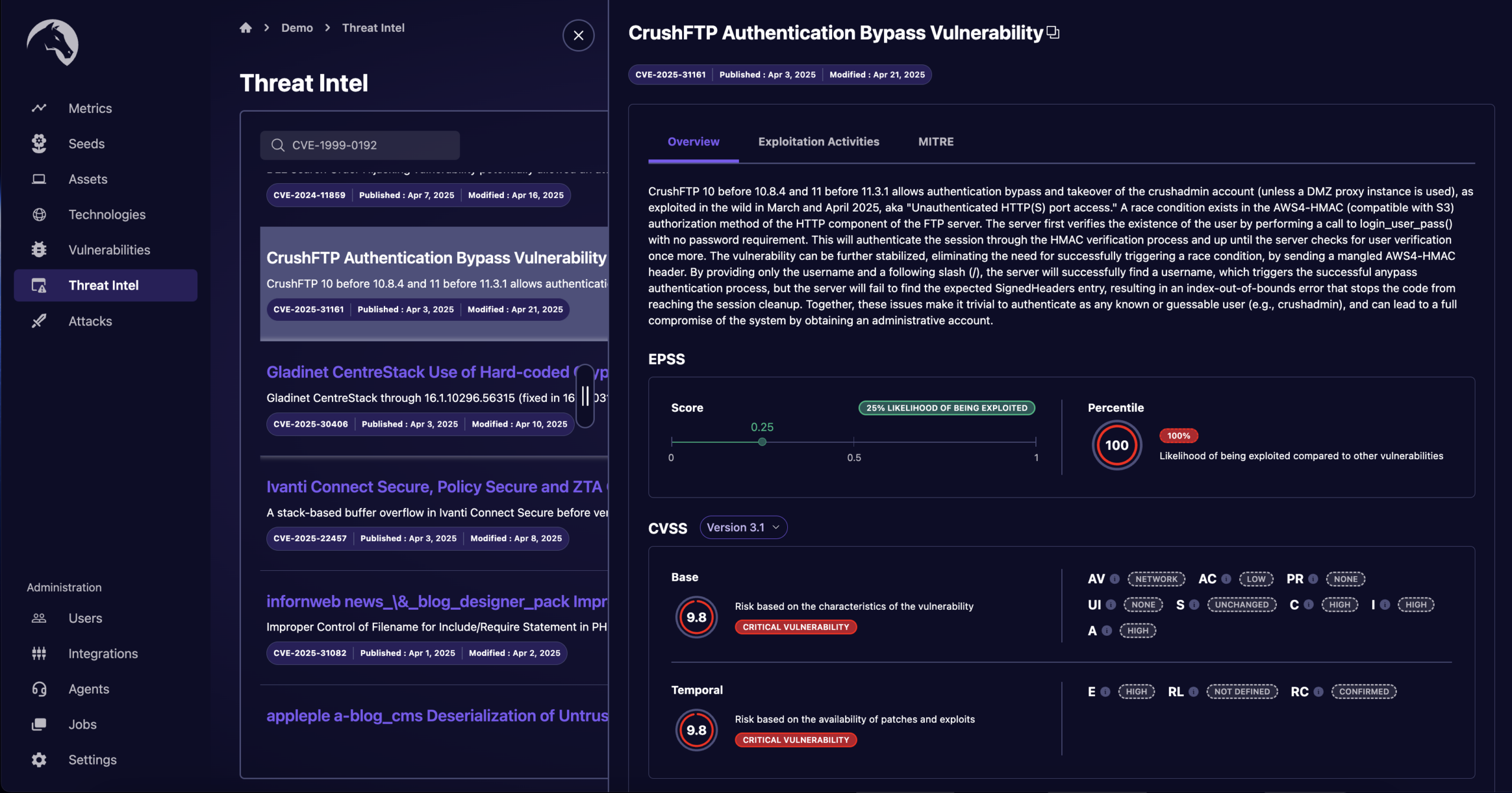
Cyber Threat Intelligence
Our attack surface management platform continuously monitors emerging threats, including detailed analysis of new vulnerabilities, exploits, and attack vectors from a variety of trusted sources.
Integrate Threat Intelligence and Expertise into a Cohesive, Efficient, and Effective CTEM Strategy
Our managed service approach ensures that all components work together seamlessly,
providing continuous monitoring, assessment, and improvement of the organization’s security posture. Each technology’s output serves as an input to the next, creating a seamless flow that zeroes in on the risks that truly matter.
Attack Surface Management
Vulnerability Management
Learn More
Attack Path Mapping
Continuous Penetration Testing
Breach and Attack Simulation
Threat Intelligence
Learn More
A Force Multiplier for Your Security Team
Praetorian's Offensive Experts Permanently Stand Side-by- Side with Our Customer's Defensive Teams
We Consolidate and Save Money
We consolidate attack surface management, vulnerability management, continuous penetration testing, breach simulation, and exploit intelligence into a single cost-effective platform.
We Include Security Experts
Our team of offensive security experts provides continuous support, aligning your security strategy with best practices and emerging threats.
We Are All Signal and No Noise
We prioritize only critical and validated risks, ensuring you focus your time and resources on what truly matters.
We Give Your Team The Ammo It Needs
As an external third party, we help you obtain the buy-in from the business to fix the risks we uncover through demonstration of impact and hard evidence.
We Got Compliance Covered
Our tech-enabled service meets annual penetration test requirements, ensuring compliance and adding value to your security efforts.
We Verify Mitigation
We ensure identified risks are remediated and provide third-party validation, supporting your IT teams every step of the way.
Ready to Start Your Continuous Threat Exposure Management Initiative?
Get a free trial to see Chariot in action.