Vulnerability Management
Validate. Prioritize. Remediate.
Praetorian’s Vulnerability Management and Prioritization solution empowers your organization to stay ahead of threats by systematically identifying, evaluating, and addressing security vulnerabilities across your digital infrastructure.
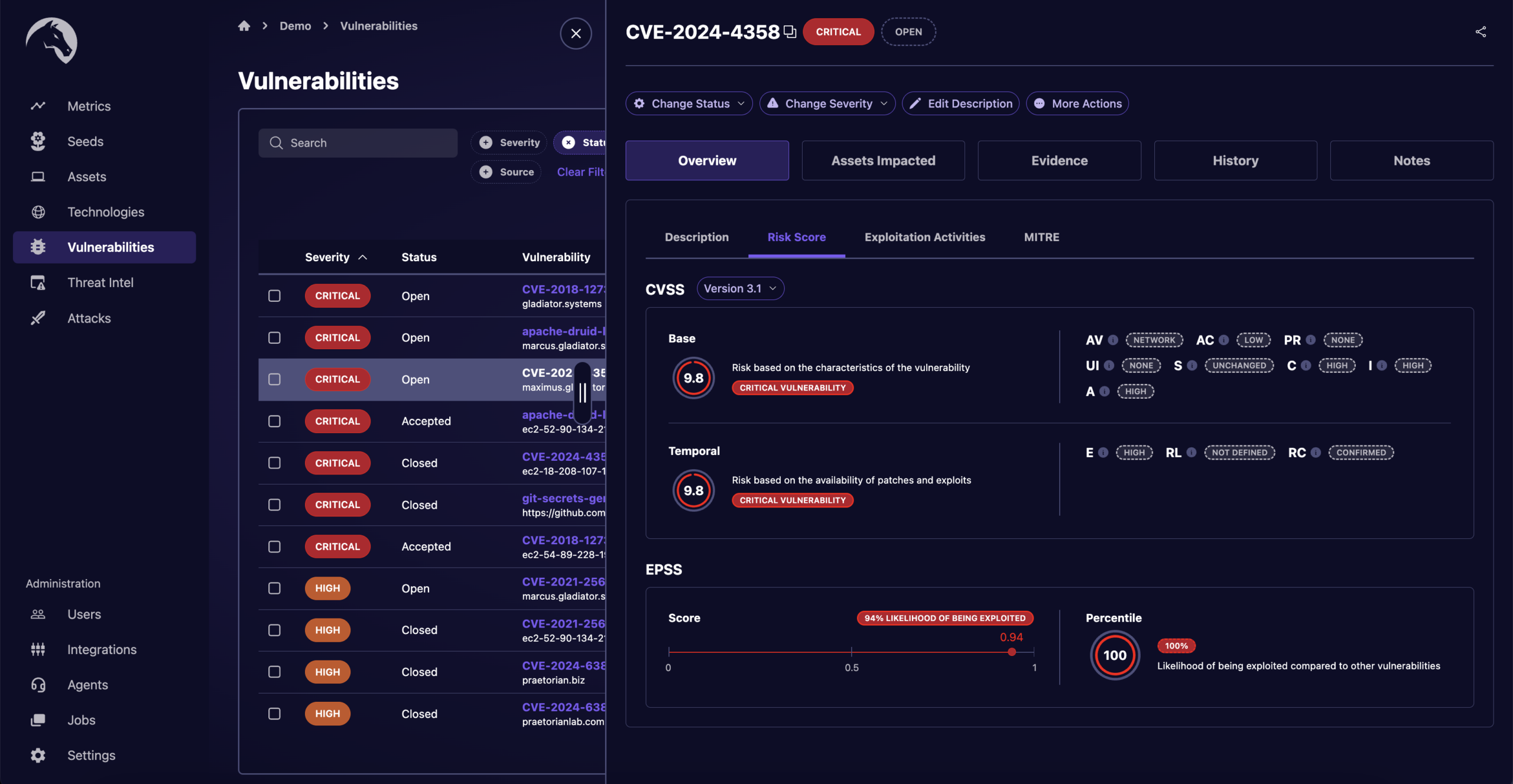
Ready to Eliminate the Vulnerability Noise?
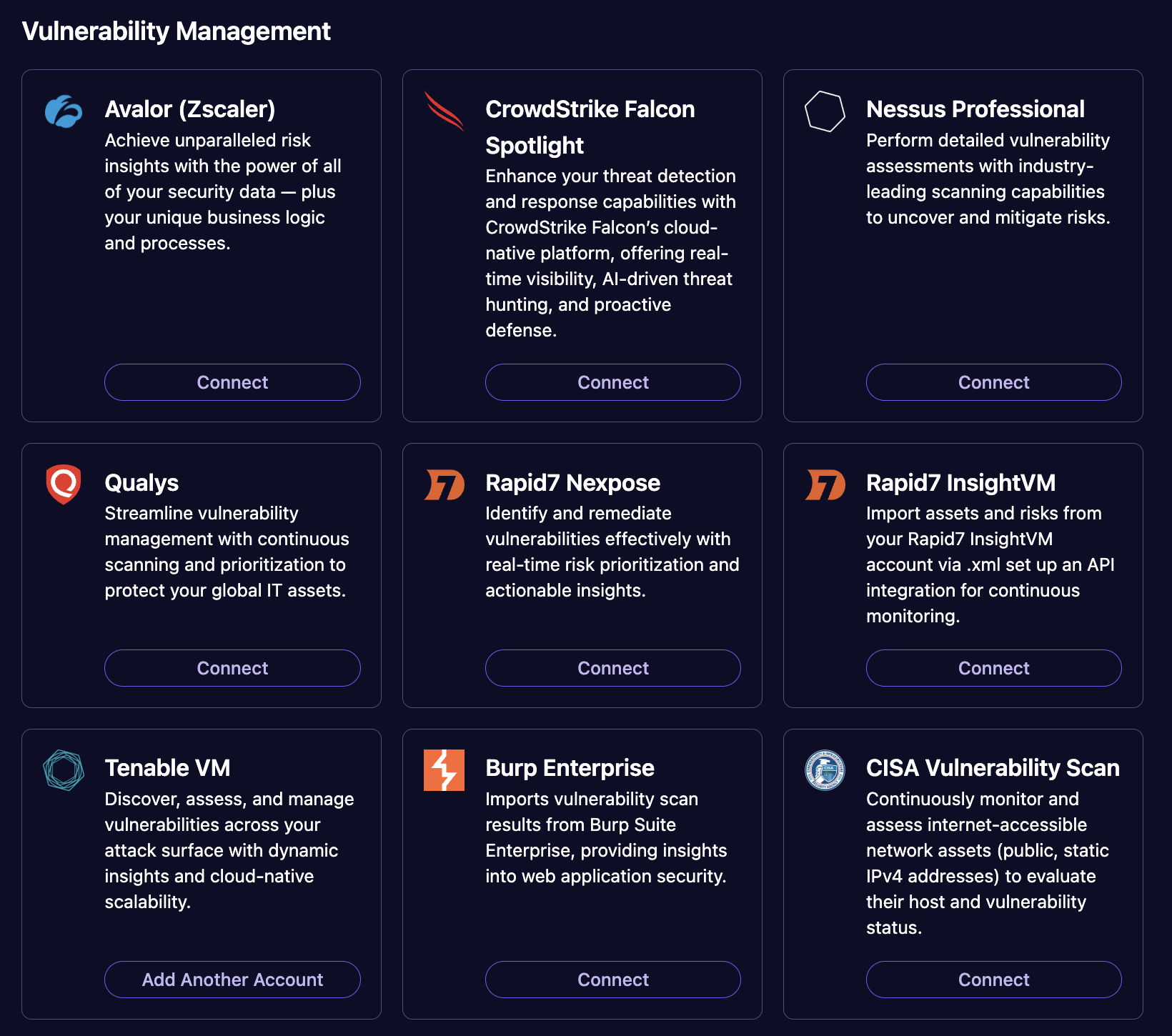
Leverage integrations with industry-leading tools such as Qualys, Nessus, Rapid7, and Wiz to ensure thorough and accurate vulnerability scanning across all assets.
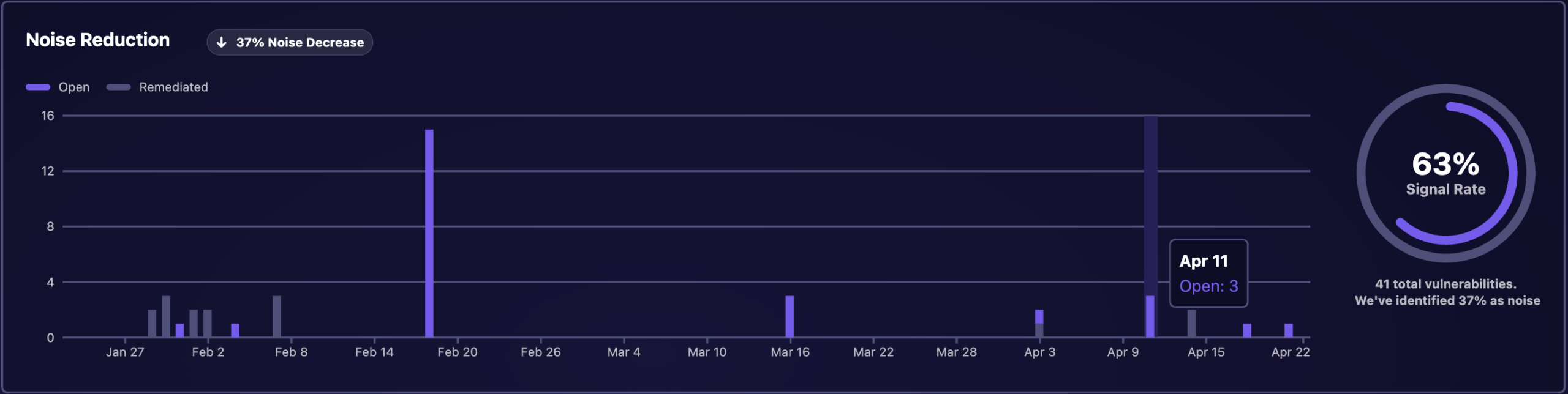
Watch The Noise Eliminate
We utilize offensive experts and advanced AI algorithms to assess the criticality of vulnerabilities based on exploitability, potential impact, and business context, allowing your team to focus on the real, material risks.
Ready to Silence the Vulnerability Noise?
Praetorian’s Offense Security Experts are Ready to Answer Your Questions