Continuous Threat Exposure Management
The Evolution of Cybersecurity
In today’s rapidly evolving threat landscape, traditional vulnerability management is no longer sufficient. Many organizations are now adopting Continuous Threat Exposure Management (CTEM) — a proactive and continuous approach that identifies, validates, and mitigates security risks across environments. By combining vulnerability management, attack surface management, and validation processes, CTEM delivers a unified strategy that improves resilience, reduces exposure, and strengthens cybersecurity protection.
How CTEM Shapes Praetorian’s Platform
Designed to embody the principles of CTEM, our platform integrates attack surface management, vulnerability management, attack path mapping, breach and attack simulation, continuous penetration testing, and threat intelligence. Furthermore, these capabilities operate as a managed service to deliver continuous, real-world validation. Together, these components work holistically to provide comprehensive visibility, improved resilience, and unmatched security coverage.
Integration of People, Processes, and Technologies
People
Designed to embody the principles of CTEM, our platform integrates attack surface management, vulnerability management, attack path mapping, breach and attack simulation, continuous penetration testing, and threat intelligence. Recognized globally, these team members are thought leaders, conference presenters (Black Hat, DEF CON, ShmooCon), published authors (Hacking Exposed series, Irreducibly Complex Systems), CVE contributors, and open-source tool developers.They do not just report the news; they make the news by developing new and novel attack techniques. With 33 MITRE TTPs attributed to Praetorian, our experts help us rapidly incorporate emerging threats into our platform, enabling our customers to prevent attacks before they happen.

Processes
We have developed robust processes to integrate these technologies and expertise into a cohesive, efficient, and effective CTEM strategy. Through a managed service approach, all components work together seamlessly to provide continuous monitoring and improvement.
Define Material Risk
We begin by analyzing a company's 10-K filing to identify material risks that could impact the business. This financial analysis helps us understand where the most critical data resides and what assets are most vital to the organization.
Locate Material Risk
Once we identify key risks, we map out the assets where this critical data is stored. This step is crucial for understanding the potential attack surface and identifying all possible entry points for attackers.
Map Attack Paths to Material Risk
With a clear understanding of asset locations, we perform continuous attack path mapping to identify and visualize potential routes of compromise. This dynamic process helps us understand how an attacker could move laterally within the network to reach critical assets.
Demonstrate Impact of Material Exposure
To provide concrete evidence of vulnerabilities and their potential impact, we demonstrate possible compromises using breach and attack simulations. This step helps in illustrating the real-world implications of identified threats and justifies the need for immediate action. To reduce rollout friction, we deploy through your existing EDR/XDR technology. There is no new agent to install!
Technologies
Our platform consolidates a range of point products into a cohesive and comprehensive solution. By integrating these technologies, we create a platform where the whole is greater than the sum of its parts. This approach allows us to quantify risks and focus on material threats rather than attempting to address every potential issue. Each technology’s output serves as an input to the next, creating a seamless flow that zeroes in on the risks that truly matter.

Attack Surface Management
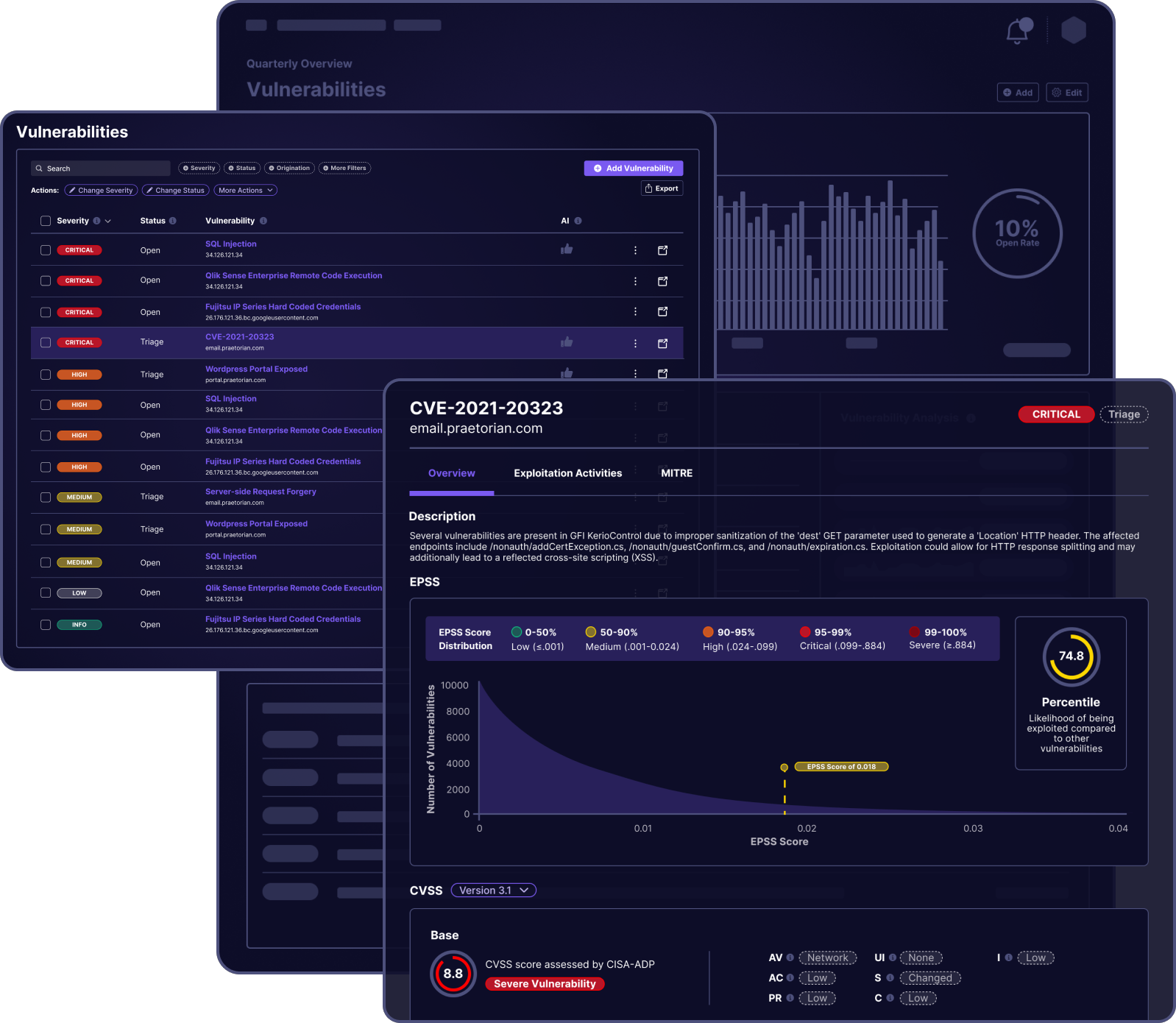
Vulnerability Management
Attack Path Mapping
Continuous Penetration Testing
Adversarial Exposure Validation
Cyber Threat Intelligence
Benefits of Our CTEM Approach
By incorporating these technologies, people, and processes, we enable organizations to move beyond traditional vulnerability management to a comprehensive, continuous threat exposure management strategy. This approach not only enhances security but also builds resilience, ensuring that your organization is prepared to face the challenges of today’s cyber threat landscape.
We Consolidate and Save Money
We consolidate attack surface management, vulnerability management, continuous penetration testing, breach simulation, and exploit intelligence into a single cost-effective platform.
We Include Security Experts
Our team of offensive security experts provides continuous support, aligning your security strategy with best practices and emerging threats.
We Are All Signal and No Noise
We prioritize only critical and validated risks, ensuring you focus your time and resources on what truly matters.
We Give Your Team The Ammo It Needs
As an external third party, we help you obtain the buy-in from the business to fix the risks we uncover through demonstration of impact and hard evidence.
We Got Compliance Covered
Our tech-enabled service meets annual penetration test requirements, ensuring compliance and adding value to your security efforts.
We Verify Mitigation
We ensure identified risks are remediated and provide third-party validation, supporting your IT teams every step of the way.
Too Much Noise
Too Many Tools
Too Few Resources
Not Enough Security

Ready to Start Your Continuous Threat Exposure Management Initiative?
Get a free trial to see Chariot in action.