Penetration Testing
Cloud Penetration Testing
Identify cloud-based vulnerabilities and understand their connections within your environment.
Gain Visibility into the Gaps and Links that Threaten Your Cloud Environment
Praetorian’s cloud security experts excel at uncovering links between seemingly independent attack vectors and exploiting them to emulate a determined attacker.
- Find and remediate access chaining in cloud environments
- Understand the extent of misconfigurations
- Identify unique threats specific to your cloud environment
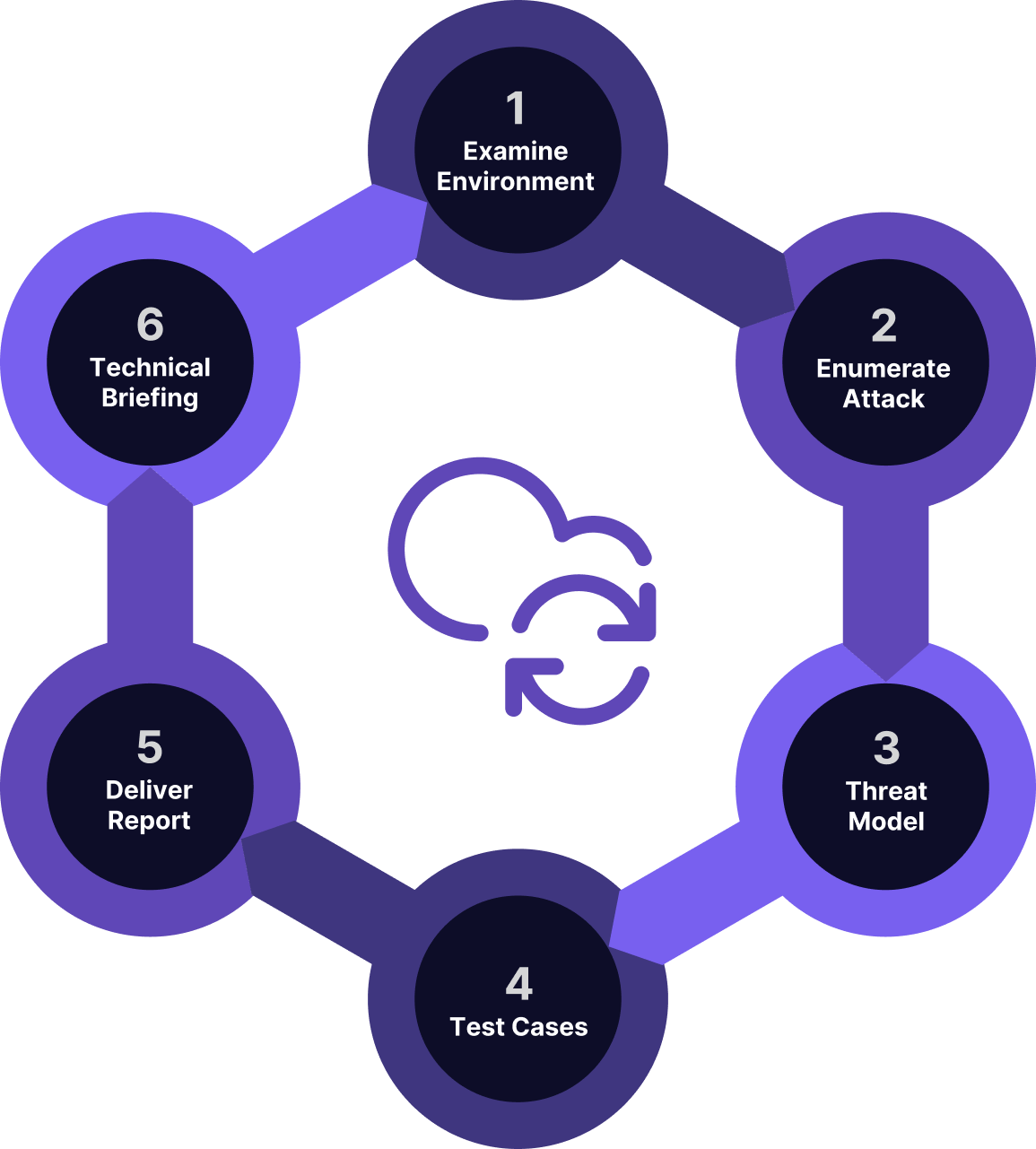
Cloud Environment Attack Path Assessment
Examine the Environment
Conduct collaborative interviews and workshops with client teams to gain a ture understanding of client’s cloud environment
Enumerate Attack Paths
Identify all avenues of attack.
Threat Model
Identify attack vectors and paths, and determine threat prioritization and overall anticipated risk.
Manually Agree to Test Cases
Converge with client on which attack paths to pursue in testing.
Execute Test Cases
Execute on targets of interest using a combination of automated tools and precise analysis. Daily updates with immediate notification of critical findings.
Write & Deliver Report
Document all findings with technical details, exploitation paths, and risk level assessment.
Technical Briefing
Collaborative read out call that allows for the client to dig into findings and identity strategic paths forward.
Understand the Root Causes of Vulnerabilities, with Recommendations and Analysis that Go Beyond a Checklist of Issues
Identify the Business Risk Potential of Every Vulnerability
By combining traditional offensive security approaches with attack vectors unique to the cloud, Praetorian engineers thoroughly test the client’s entire cloud environment. We analyze network, infrastructure, and web application paths to achieve privileged cloud access and meet our objectives.
Cloud Penetration Testing Services Comparison
A comprehensive, adversarial-focused assessment of your web or cloud’s security posture.
| Testing Requirements |
Cloud Security Configuration Review |
Cloud Penetration Test |
Cloud Attack Path Mapping |
|---|---|---|---|
| Authentication Credentials | |||
| Customer-defined objectives | |||
| Security and Engineering Interviews | Optional | ||
| Approach | |||
| Configuration-based | |||
| Objective-based | |||
| Feature Comparison | |||
| CSP Service Configuration Analysis | |||
| Kubernetes Cluster Configuration Analysis | Optional | Optional | Optional |
| Risk demonstration via exploitation | |||
| Threat Modeling | Optional | ||
| Deliverables | |||
| PDF Report | |||
| Engagement Summary Letter | |||
| Threat Model | Optional | ||
| Strategic Recommendations | Optional | ||
| Technical and Executive Debrief |

Why Choose Praetorian
Praetorian has decades of experience in conducting penetration testing engagements, and the resulting adversarial perspective underpins everything we do. Our highly technical cloud security engineers set our cloud security services apart from fully automated or tool-dependent competitors. By combining our offensive security DNA with profound cloud expertise, we deliver a Risk Informed Security Assessment with an emphasis on cloud attack vectors
Industry Leading Engineers
Our adversarial experts have extensive experience in building cloud infrastructures and assessing cloud security at scale. They frequently collaborate with their red team and application penetration testing colleagues.
Proven Methodology
By combining unique vectors identified from and into the cloud with traditional offensive security, we thoroughly test the client’s entire cloud environment.
Innovative Enablement Platform
Our continuous offensive security platform underpins every engagement, so your team can partner with our experts on the things that matter.
Cloud Penetration Testing Deliverables
Executive Summary
Concise explanation of engagement goals, significant findings, business impacts, and strategic recommendations
Engagement Outbrief Presentation
Similar to the executive summary, presented to the audience of your choosing
Engagement Outbrief Presentation
Similar to the executive summary, presented to the audience of your choosing
Who Needs this Service
Companies exploring their cloud environment from an attacker’s perspective
Compliance teams demonstrating their environment meets regulations
Security teams confirming readiness before a launch date
Ready to Discuss Your Cloud Penetration Testing Initiative?
Praetorian’s Offense Security Experts are Ready to Answer Your Questions