FDA Regulatory Compliance
FDA Pre-Market and Post-Market Testing and Monitoring
Your cybersecurity partner in meeting and maintaining FDA requirements
Every Medical Device is Unique, So are its Cybersecurity Requirements
Praetorian’s device security experts ensure comprehensive protection and compliance by tirelessly partnering with clients to customize the security strategy for every device.
From security insight during design and actionable testing throughout the product lifecycle, to continuously identifying and mitigating emerging threats postmarket, Praetorian is the trusted partner for todays leading medical device manufacturers.
Pre-Market
Navigate the complexities of FDA premarket compliance requirements with ease. Praetorian's expert advisory and comprehensive testing services provide verification of critical security controls and guidance to meet FDA compliance standards, paving the way for a successful market launch.
Post-Market
Ensure your medical devices comply with the highest safety standards through our continuous offensive security monitoring, tailored specifically for FDA-regulated entities. Protect patient data and maintain trust with unparalleled security vigilance.
Both Stages
Developing a comprehensive security strategy for the entire device lifecycle recognizes its role within a broader environment that requires continuous protection. From pre-market security assessments to maintaining proactive security post-release, manufacturers need a partner they can rely on.
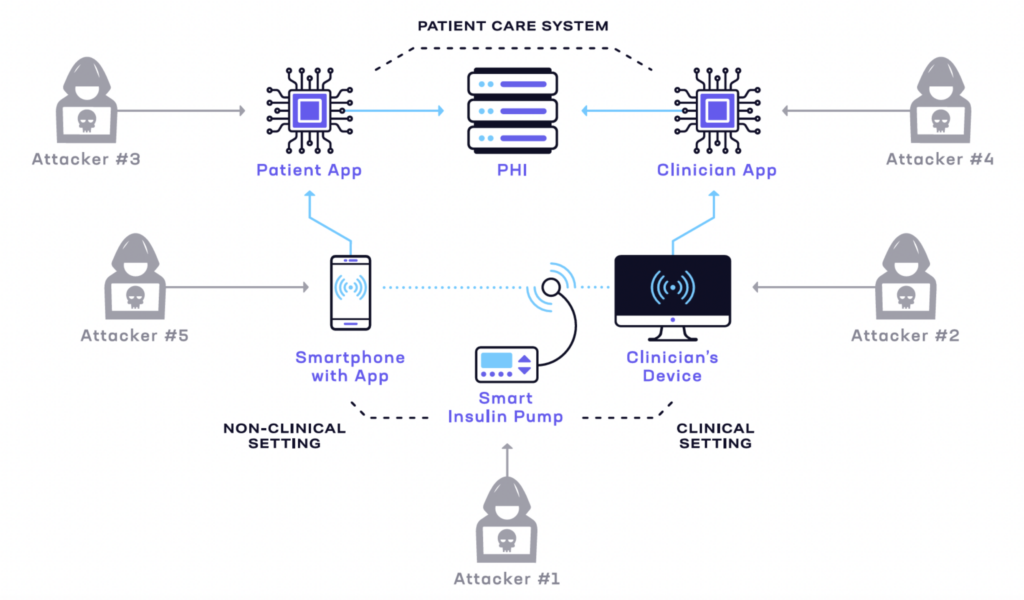
sample threat model
Executing an Offensive Security Strategy for Medical Devices
Medical Device Penetration Testing Deliverables
Core of Hardware Security
Our engineers utilize your sample hardware to simulate usage conditions meticulously debugging, network, or wireless interfaces. This allows us to gain a comprehensive understanding of the device's internal operations and potential vulnerability to attacks.
Destructive Testing
Perform a light-touch disassembly of devices to expose additional interfaces and attack surfaces. We use optional destructive testing to thoroughly exploit the example hardware, which may result in rendering a device inoperable.
Backend Attacks
Address attacks on data in transit and data at rest in the backend cloud environment. Our engineers have expertise in various IoT PaaS and cloud IoT registries, as well as the asynchronous messaging systems often used alongside them.
Accelerate the Pre-Market Submission Process So You Can Bring a Secure, Effective Device to Market Sooner
Comprehensive Pre-Market Testing and Risk Assessments
Security Control Implementation
Your Continuous Offensive Security Solution to Address Evolving Threats for Postmarket Monitoring
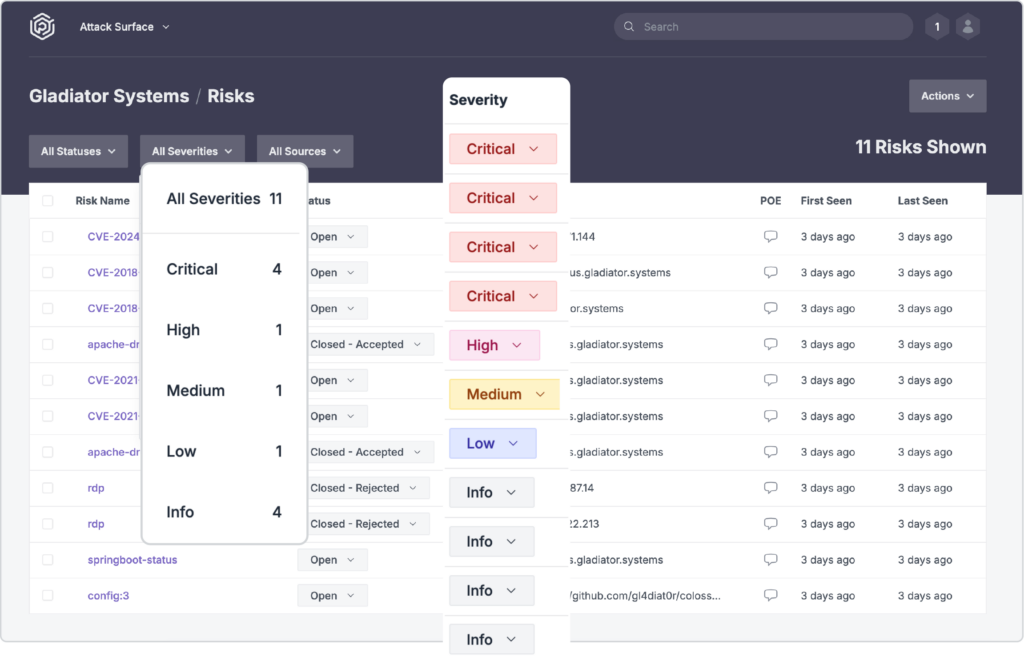
Continuous Human Led, Platform Driven Postmarket Management
Praetorian’s continuous security solution combines Attack surface management and continuous penetration testing to ensure comprehensive postmarket monitoring of your devices. Our expert managed service team, enabled by our continuous automation platform, Chariot, provides superior breadth of assessment and time-on-target than one-off penetration testing can provide.
Monitor
Gain continuous, comprehensive, and contextual asset discovery and vulnerability monitoring when you integrate Chariot with your cloud providers, source code managers, container registries, workloads, and CI/CD pipelines.
Identify
Save your internal team time and energy by eliminating the triage process. Gain confidence that any alert from our team represents a material risk that adversarial engineers have verified as an exploitable attack path.
Address
Validate that remediation steps were effective and operate within the guidelines of your vulnerability disclosure processes.
Ready to Discuss Your FDA Pre-Market and Post-Market Testing Initiative?
Praetorian’s Offense Security Experts are Ready to Answer Your Questions