Penetration Testing
IoT Penetration Testing
Praetorian’s IoT penetration testing assesses the full IoT ecosystem, from backend systems and business processes to hardware and mobile devices, to identify security risks associated with design, implementation, and manufacturing.
Identify Security Risks Associated with Design, Implementation, and Manufacturing
Our engineers review source code, API specifications, and technical standards to understand potential weaknesses and tailor their testing. We then utilize the latest in tools and technology to identify vulnerabilities, demonstrate attacks, analyze protocols, and enumerate the attack surface.
IoT Penetration Testing Deliverables
Core of Hardware Security
Our engineers use your hardware to simulate usage conditions and access debugging, network, or wireless interfaces. This provides us a detailed understanding of the device’s internal mechanisms and how it might be attacked.
Destructive Testing
Praetorian experts perform light-touch disassembly of devices to expose additional interfaces and attack surfaces. Optional destructive testing is utilized to thoroughly exploit hardware but may result in device malfunction.
Backend Attacks
Our experts cover attacks against both data in transit and data at rest within the backend cloud environment. We provide deep experience in various IoT PaaS and cloud IoT registries, as well as the asynchronous messaging systems commonly used in conjunction with them.
SAMPLE THREAT MATRIX
IoT Attack Path Assessment
Manual Techniques for Penetration Testing

Design Advisory
- Threat modeling
- Secure design advisory
- Program maturity analysis

Security Training
- Hardware penetration testing
- Firmware analysis and reverse engineering
- Wireless protocol analysis
- Supply chain security review
- Network traffic analysis

Compliance Assessments
- CVE “CBOM” analysis
- Primary controls verification
Assess the IoT Ecosystem, from Backend Systems and Business Processes to Hardware and Mobile Devices
Identify Attack Paths to Critical IoT Assets
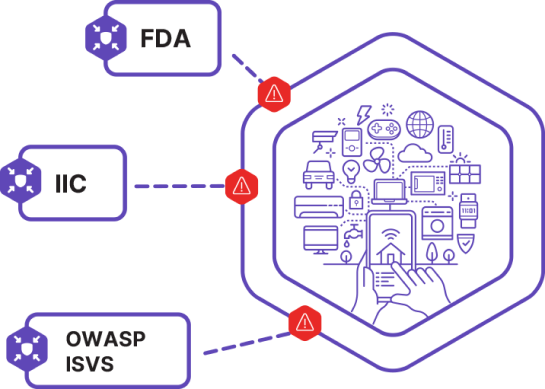
Orient an assessment on established industry or government standard—such as OWASP ISVS, the IIC Industrial IoT Security Framework, or FDA requirements—or create a customized threat model for the specific device.

Collaborative, Transparent Partnership to Help You Focus on the True Material risks
For each engagement, our engineers review source code, API specifications, and technical standards to understand where weaknesses are likely to arise, then tailor their testing accordingly. We then use tools–both commercially available and bespoke from Praetorian Labs–to identify vulnerabilities, demonstrate attacks, analyze protocols, and enumerate the attack surface.

Why Choose Praetorian
At Praetorian, we provide a timely, tailored, and thorough assessment of your product’s cybersecurity from the backend to the user interface and everywhere in between. We have industry-specific experience involving:
- Medical devices
- Automotive security
- ICS/ SCADA
- Carrier-grade network appliances
- Business or home automation
Leading Security Engineers
Our adversarial experts have decades of experience and deep technical expertise in hardware penetration testing
Proven Methodology
Whether you choose to orient your engagement around a government or industry framework or a custom threat model, our engineers will take a creative, rigorous approach in identifying potential attack paths and technically exploiting them.
Innovative Enablement Platform
Our continuous offensive security platform underpins every engagement, so your team can partner with our experts on the things that matter.
Who Needs this Service
Device Manufacturers
Enterprises designing or manufacturing connected devices or firmware.
Device Users
Organizations deploying connected devices in their critical infrastructure
PaaS Providers
Companies developing IoT infrastructure for device manufacturers
Ready to Discuss Your IoT Penetration Testing Initiative?
Praetorian’s Offense Security Experts are Ready to Answer Your Questions