Offensive Security
Red Team
Test and exercise your cybersecurity program against real-world attacks. Praetorian Red Team will put your security capabilities through its paces, while leveraging weaknesses across people, process and technology across prevention, detection and response
Simulate Sophisticated Attacks to Strengthen Your Defenses
Praetorian’s red‑team engagements immerse your organization in a realistic cyber‑attack. Rather than running a purely theoretical tabletop exercise, we emulate the tactics of nation‑state adversaries and advanced persistent threats to expose weaknesses across your people, processes and technology. Each engagement is tailored to your business objectives and risk profile – from protecting customer data to safeguarding critical infrastructure – and is delivered by a team of ex‑NSA, CIA and elite security researchers. This precision and expertise are essential in cybersecurity marketing because buyers want technically sound content that converts into meaningful action
Our red‑team services are not just about finding vulnerabilities; they are designed to help you prove the resilience of your security program, validate playbooks, and prioritise investments. Through expert‑driven content and clear communication, we build the trust that decision‑makers demand
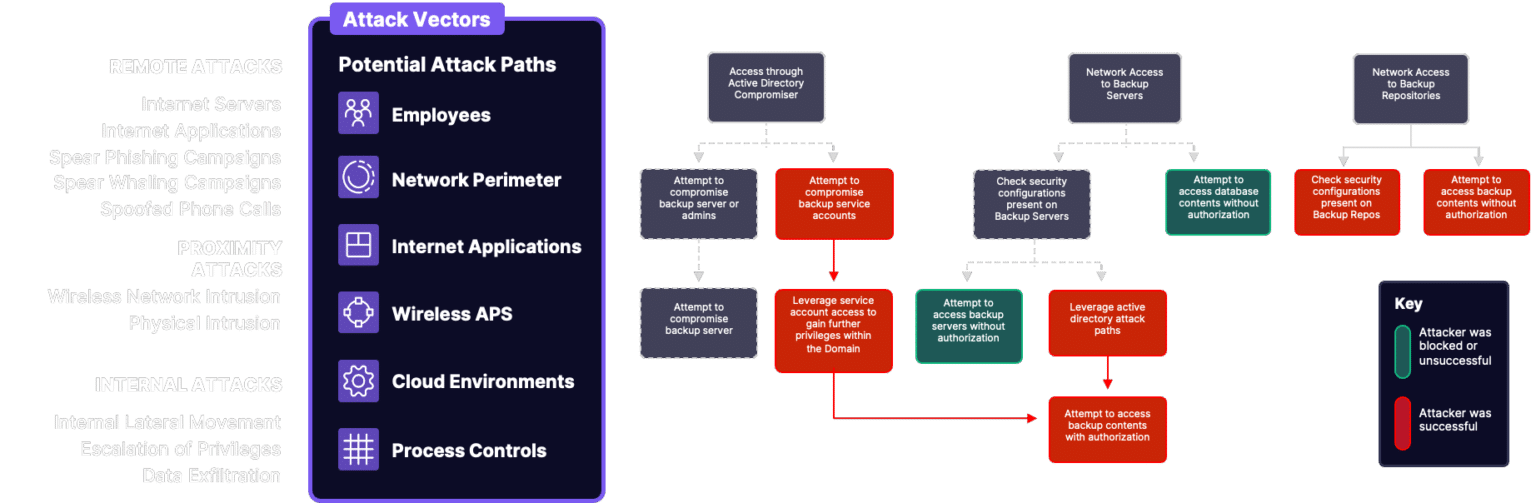
Common Red Team Attack Objectives
Demonstrate direct financial loss through the transfer of monetary funds to a nominated bank account
Demonstrate access to VIP mailbox, data, or workstation
Demonstrate ability to exert control over an ICS device or environment [water plant, food processing, oil refinement]
Demonstrate control over a critical capability such as power supply to a geographic location
Simulate ransomware attack by encrypting test systems and demanding a ransom
Perpetrate theft of intellectual property (IP) and competitive differentiation or theft of customer data such as PII, PHI, or CC information
Why Praetorian?
Exoert Offensive Security Engineers
Our core operators are former NSA and CIA officers and top‑tier security researchers with decades of offensive experience. They can simulate nation‑state attack patterns and advanced persistent threats, giving your organisation a realistic assessment of how sophisticated adversaries would operate
Cutting-Edge Offensive Security Research
A dedicated offensive labs research team continuously develops new tactics, techniques and procedures (TTPs), creates bespoke covert tools, and discovers zero‑day exploits for use in engagements. This emergent attack intelligence ensures your red‑team assessment stays ahead of the evolving threat landscape.
Chariot™ Red Team Platform
Our core operators are former NSA and CIA officers and top‑tier security researchers with decades of offensive experience. They can simulate nation‑state attack patterns and advanced persistent threats, giving your organisation a realistic assessment of how sophisticated adversaries would operate
Close Collaboration With White Team
We work closely with your stakeholders to set objectives, define rules of engagement and establish a threat model. Throughout the exercise we maintain open communication with designated defensive teams, then deliver a comprehensive report and an in‑depth debrief to ensure actionable remediation and program improvemen
Red Team Attack Lifecycle
Attack Staging
Prepare the infrastructure and tooling required to orchestrate the attack.
Reconnaissance
Obtain information about the client’s people, process, and technology to identify attack surfaces and provide intelligence to attacks.
Initial Access
Identify and exploit attack vectors to gain initial access to the target environment
Persistence
Establish a persistent foothold within the target environment
Lateral Movement
Compromise additional assets and gain additional privileges in a strategic fashion that supports the attack mission
Privilege Escalation
Compromise additional assets and gain additional privileges in a strategic fashion that supports the attack mission
Actions on Objectives
Understand the standard operating procedures surrounding the attack objectives and perform necessary steps to achieve the goal
Collaborative Attack Objectives
We work with you to set attack objectives that align with specific business risks. The objectives guide the engagement, shaping the technical milestones we establish. Ultimately, we offer a focal point for demonstrating impact.
How Praetorian’s Red Team Will Work with You
Project Kickoff
Praetorian’s Practice Manager will set up a kickoff call with client stakeholders to introduce the team.
Rules of Engagement and Threat Model
We explicitly determine the scope of the exercise and collaboratively define the attack objective.
Red Team Excercise
Our engineers execute the end-to-end attack lifecycle. Communications occur between the predefined teams in a fluid fashion.
Technical Report
Upon completion of the live exercise, Praetorian compiles the draft report.
Executive Presentation
We hold a debriefing call between all participants and the client’s project stakeholders wherein we discuss an in-depth narrative of the exercise.
Who Needs this Service
Boards of Directors
Seeking to ascertain the risk of a high profile attack and understand potential impacts to the business, its customers, and partners.
Security teams
Wanting to run their playbooks or justify new security initiatives, budget cycles, or recent security investment
Organizations
Needing to demonstrate resilience against cyber-attacks and/or demonstrate resolution of audit findings as part of previous engagements or regulatory requirements
Ready to Discuss Your Red Team Initiative?
Praetorian’s Offense Security Experts are Ready to Answer Your Questions